How to Define Insider Threat: A Guide to Proactive Prevention
- Marketing Team

- Dec 25, 2025
- 15 min read
Updated: Dec 26, 2025
Let's get right to it. An insider threat isn't some shadowy, niche problem handled by IT. It's a fundamental business liability that comes from someone who already has the keys to the kingdom—an employee, a contractor, or even a trusted partner—using their legitimate access to harm your organization.
This is a core human-factor risk, and whether the damage is intentional or not, the consequences for your bottom line, reputation, and compliance posture are just as severe. The old way of reacting after the damage is done is a failed strategy; the new standard is proactive, ethical prevention.
What Is an Insider Threat in Business Terms?
In simple business terms, to define insider threat is to acknowledge the potential for anyone with authorized access to your assets to cause serious damage. This goes way beyond cyber attacks. We’re talking about financial fraud, the loss of priceless intellectual property, crippling operational disruptions, and the kind of reputational damage that takes years to repair.
The real danger is that these individuals are already inside your defenses. Your firewalls and traditional surveillance tools are completely blind to them, making their actions incredibly difficult to spot until it's far too late. This is a human problem that requires a human-centric solution, not more reactive technology.

The Three Faces of an Insider Threat
Leading risk management frameworks from agencies like CISA and NIST don't paint this threat with a single brush. They break it down into three distinct categories, because understanding the "why" is just as important as the "what" when building a preventive strategy.
Malicious Insiders: These are the classic "bad actors." They intentionally cause harm for personal gain, revenge, or even ideological reasons. Think of a disgruntled employee walking out the door with your entire client list to take to a competitor.
Negligent Insiders: Far more common, these are the employees who make honest mistakes with disastrous consequences. They might misconfigure a server, fall for a sophisticated phishing scam, or accidentally email sensitive data to the wrong person. Their intent isn't harmful, but the business impact is just as severe.
Compromised Insiders: These individuals are the unwitting pawns in a larger attack. An external hacker steals their credentials and uses their legitimate access to move through your network. To your security systems, they look like a trusted employee.
To help clarify these concepts from a business liability perspective, the table below breaks down the core dimensions of an insider threat.
Key Dimensions of an Insider Threat
Dimension | Description | Business Impact Example |
|---|---|---|
The Actor | An individual with current or former authorized access to the organization's network, systems, or data. | A recently terminated salesperson uses their still-active login to download proprietary sales strategies for a new competitor. |
The Action | Intentionally or unintentionally misusing that authorized access to negatively affect the company's confidentiality, integrity, or availability. | A well-meaning but rushed marketing employee accidentally publishes a spreadsheet with sensitive customer PII to a public-facing web server. |
The Asset | The target of the action, including confidential data, intellectual property, financial systems, or brand reputation. | A systems administrator, motivated by a personal grievance, deliberately deletes critical operational databases, causing a company-wide outage. |
The Impact | The resulting harm to the organization's financial stability, regulatory standing, operational continuity, and brand reputation. | A finance manager falls for a spear-phishing email, leading to the compromise of executive credentials and a multi-million dollar fraudulent wire transfer. |
Each dimension shows how a breakdown in process, oversight, or ethical governance can lead to significant, tangible business damage.
The Financial and Operational Reality
Every leader in Compliance, HR, and Security needs to internalize this, because the financial impact is staggering. Recent analysis shows that insiders are responsible for a significant percentage of all data breaches, driving the average annual cost of managing these risks to an eye-watering $17.4 million per organization.
Those numbers make it painfully clear: this is an enterprise-wide governance challenge, not just another IT problem to solve.
To properly define insider threat is to see it as a business risk leveraged through legitimate access. Whether it's a disgruntled employee exfiltrating intellectual property or a careless contractor exposing customer data, the outcome is the same—a direct blow to your organization's bottom line and reputation.
This reality demands a major shift in thinking. The old way of using reactive, invasive surveillance to "catch" people after the fact is a losing game that creates legal liability. The new standard is proactive, non-intrusive, and EPPA-aligned prevention. It's about identifying the behavioral and contextual signals that point to elevated human-factor risk before an incident happens. You can get a head start by reading our complete guide on insider threat indicators.
The Three Faces of Insider Risk: Malicious, Negligent, and Compromised
If you want to define insider threat in a way that actually helps your business, you have to realize you’re not dealing with a single problem. The risk shows up in completely different ways, driven by unique motives and circumstances. Getting a handle on these three archetypes is the first step toward building a risk management strategy that works in the real world.
Focusing only on finding the classic "bad actor" is a strategy destined to fail. Why? Because it completely ignores the two most common sources of insider incidents.
The Malicious Insider: The Deliberate Saboteur
This is the villain of the insider threat story. The malicious insider is someone who intentionally uses their authorized access to cause harm. Their motives are often deeply personal, ranging from financial desperation to pure, unadulterated revenge.
Imagine a sales director, furious after being passed over for a promotion, quietly downloading the entire client database and your strategic plans. A week later, they resign and walk that priceless intellectual property straight over to your biggest competitor. This isn't an accident; it's a calculated act of sabotage that reactive tools only catch after the data is gone.
The malicious insider acts with clear intent. Whether driven by greed, ego, or ideology, their goal is to inflict direct financial, operational, or reputational damage on the organization.
These actors are especially dangerous because they know exactly where the valuable data is and understand how to sidestep basic security controls without raising immediate red flags. Their actions often involve fraud, intellectual property theft, or the deliberate destruction of critical assets.
The Negligent Insider: The Unintentional Catalyst
By far the most common—and often the most costly—source of insider risk is the negligent insider. These aren’t bad people. They are well-intentioned employees who make simple, human errors that end up having catastrophic consequences. Their actions are born from haste, distraction, or a lack of awareness, never malice.
Think about the HR manager working late to finish payroll who accidentally emails a spreadsheet packed with employee salaries and social security numbers to the wrong distribution list. Or the busy project manager who, just trying to be efficient, uploads sensitive project files to a personal, unsecured cloud storage account to work from home.
These are the everyday mistakes that create massive vulnerabilities. In fact, a significant majority of insider-related incidents stem from this kind of unintentional negligence. A strategy that only hunts for malicious behavior is completely blind to this enormous area of risk.
The Compromised Insider: The Unwitting Pawn
The third face of insider risk is the compromised insider—a legitimate employee whose credentials have been stolen and are now being used by an external attacker. This person is an unwilling participant, effectively becoming a digital puppet for a hacker.
A classic scenario involves a sophisticated phishing email that looks like it’s from the IT department, asking an employee to reset their password. The employee clicks the link, enters their credentials on a convincing fake login page, and unknowingly hands the keys to a cybercriminal.
The attacker then logs in as that trusted employee, moving through the network with completely legitimate access. To your security tools, everything appears normal. This makes internal threat detection based on old surveillance models incredibly difficult, as the system just sees a valid user performing actions they are authorized to do.
Understanding the Hidden Costs and Business Impact
When we talk about the impact of an insider threat, most people think about the immediate cleanup. But that’s just the tip of the iceberg. To really get a handle on the risk, you have to look past the initial incident and see the cascade of financial, operational, and reputational damage that can ripple through a company for years.
The first wave of expenses is obvious enough: forensic teams, legal bills, and the immediate scramble to plug the hole. But the financial bleeding doesn't stop there. It quickly expands to include regulatory fines for compliance breaches, skyrocketing insurance premiums, and the massive cost of notifying customers and providing credit monitoring services.
The Financial Drain of Reactive Responses
The financial footprint of insider threats is huge, and it's getting bigger every year. The average organization is now spending around $17.4 million annually to manage these risks—a figure that covers everything from incident response to reputational harm.
Here's the kicker: companies are still pouring money into containment rather than prevention. This reactive spending model isn't just inefficient; it's completely unsustainable as the threats continue to evolve. Prevention is always more cost-effective than a cure, especially when the cure involves costly, after-the-fact investigations.
This infographic breaks down the primary categories of insider threats, showing the different human elements that are in play.
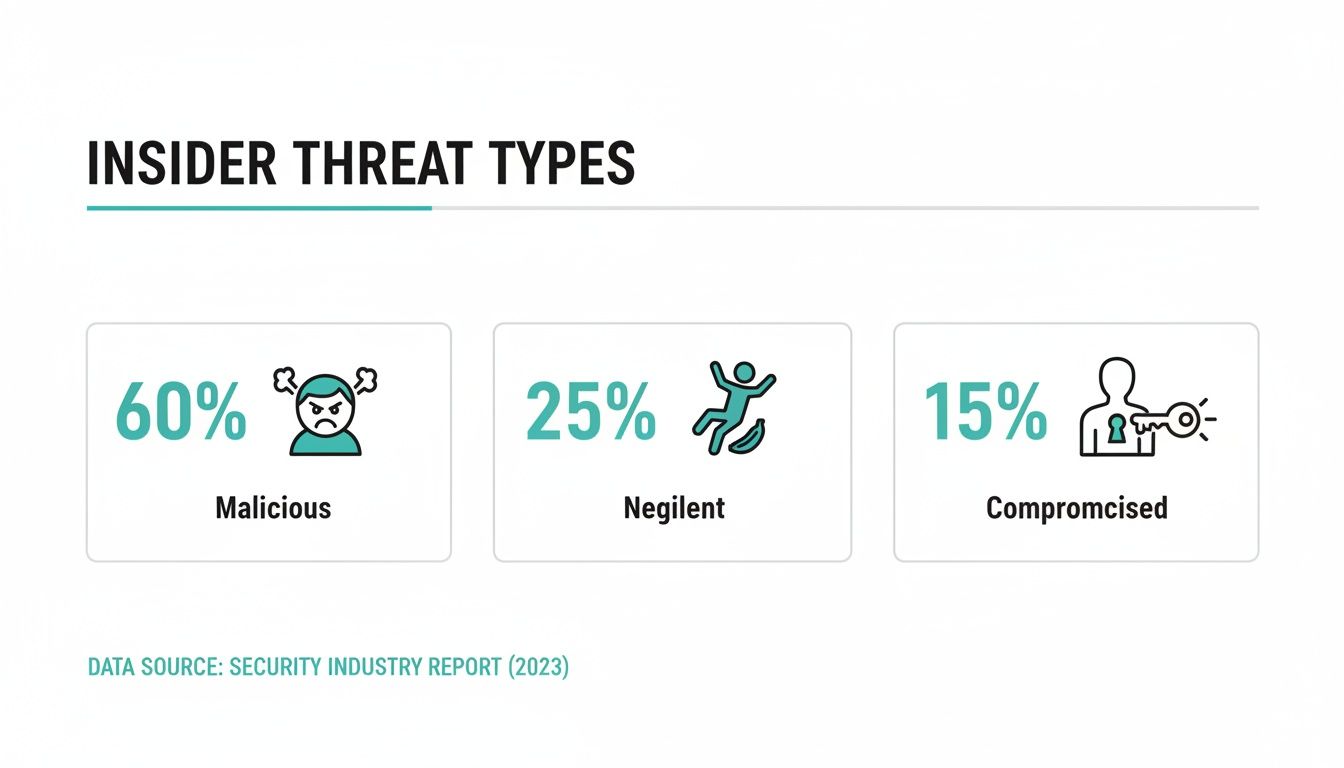
Understanding these distinct threat types—Malicious, Negligent, and Compromised—is crucial for calculating the full scope of potential business impact and tailoring preventive strategies that actually work.
Beyond the Balance Sheet: Reputational and Operational Damage
While the financial numbers are staggering, the intangible costs can be even more devastating. A single, high-profile incident can shatter years of carefully built customer trust and brand loyalty. This erosion of confidence often leads to customer churn, a hit to your market value, and a damaged public image that’s incredibly difficult to rebuild.
Operationally, the consequences can be crippling. Think about what happens when intellectual property or trade secrets are stolen. The loss of that competitive advantage can derail product launches, undermine your market position, and hand a massive victory to your rivals.
Don't forget the internal damage, either. Lengthy, invasive investigations create a culture of suspicion and distrust, wrecking morale and hurting productivity long after the incident is "resolved." You can explore more about this downward spiral in our deep dive on the true cost of reactive investigations and their impact on a company's health.
The real damage from an insider threat is rarely confined to a single event. It’s a slow bleed of financial resources, competitive edge, and market reputation, driven by a failure to move from a reactive to a proactive risk posture.
Ultimately, every part of the business is connected. A critical aspect of mitigating business impact involves safeguarding sensitive information, and you can further protect your company from data breaches with secure data destruction practices to close potential security gaps. Recognizing these interconnected costs builds a powerful business case for adopting a modern, ethical, and non-intrusive approach to internal risk management. It reframes prevention not as a security expense, but as a core strategy for protecting your bottom line and ensuring long-term business resilience.
Why Traditional Detection Methods Fail Your Business
Many companies operate under the dangerous assumption that their existing security stack has internal risk covered. Tools like Data Loss Prevention (DLP) and User Activity Monitoring (UAM) promise visibility, but they are surveillance-based technologies that create a dangerous ‘prevention gap’ that leaves businesses completely exposed to legal and financial liability.
These traditional methods are fundamentally reactive. They're designed to sound the alarm after a potential policy violation has already happened. Waiting for a data breach alert isn't a strategy; it's an admission of failure.
This after-the-fact approach means the damage—whether it's data exfiltration, system sabotage, or a compliance breach—is already in motion. Instead of preventing the fire, these tools are just fire alarms. They force your teams into a constant, costly cycle of forensic investigation and damage control, built only to analyze an event that has passed, not to spot the warning signs that come first.
The Crushing Weight of False Positives
Traditional surveillance-based tools operate by casting a wide net, flagging any activity that deviates from a rigid, predefined set of rules. The result? An overwhelming flood of false positives. Security and HR teams are forced to chase down countless meaningless alerts, burning valuable time and resources investigating events that pose no real risk.
This constant alert fatigue desensitizes teams, making it far more likely that a genuine threat will be overlooked amidst the noise. It’s an inefficient and unsustainable model that keeps your most valuable people bogged down in low-value work instead of focusing on what matters: proactive risk mitigation.
Navigating a Legal and Ethical Minefield
Beyond being operationally clumsy, surveillance-based tools create massive legal and ethical problems. Aggressive employee monitoring can easily cross the line into an invasion of privacy, creating a hostile and distrustful work environment.
In the United States, this approach often runs afoul of regulations like the Employee Polygraph Protection Act (EPPA), which sets strict limits on how employers can assess an employee's integrity. Relying on invasive tools not only fails to stop threats but also exposes the company to serious legal liability and cultural decay.
An environment built on surveillance erodes the psychological contract between employer and employee. It damages morale, stifles collaboration, and ultimately harms productivity, turning risk management into a source of organizational friction rather than a source of resilience.
This is a critical point for leaders in HR, Legal, and Compliance. Relying on invasive tools not only fails to prevent threats effectively but also exposes the company to legal liability and cultural decay.
The High Cost of Slow Detection
The fundamental flaw in traditional methods is their inability to catch risks early. It's a massive blind spot, and the numbers prove it. Recent industry surveys show that 93% of security leaders find insider threats as difficult or more difficult to detect than external attacks, and a mere 23% feel strongly confident in their ability to stop them before serious damage occurs.
This detection deficit has severe financial consequences. Organizations take an average of 81 days to resolve an insider incident, with costs escalating dramatically the longer a threat goes undetected. For risk and compliance officers, these long detection windows and low confidence in existing controls represent a massive financial and reputational liability. You can learn more about these challenges in the 2025 Insider Risk Report.
Reactive Forensics vs Proactive Prevention
The difference between the old way and the new way couldn't be more stark. It's a fundamental shift in philosophy, moving from a culture of suspicion and reaction to one of proactive integrity and prevention. The table below breaks down what this looks like in practice.
Attribute | Reactive Surveillance and Forensics (The Old Way) | Proactive and Ethical Prevention (The New Standard) |
|---|---|---|
Core Philosophy | Catch bad actors after the fact through invasive employee monitoring. | Identify human-factor risks before they escalate into incidents. |
Primary Method | Surveillance, rule-based alerts, and after-the-fact investigation. | Ethical, EPPA-compliant risk assessments and behavioral indicators. |
Key Focus | What happened? (Analyzing past events) | What might happen? (Anticipating future risks) |
Employee Impact | Creates a culture of distrust, fear, and "us vs. them." Damages morale. | Fosters a culture of integrity and psychological safety. Respects dignity. |
Legal & Ethical Risk | High. Often violates privacy norms and regulations like EPPA. | Low. Designed from the ground up to be fully compliant and non-intrusive. |
Business Outcome | High costs from incidents, investigations, fines, and employee turnover. | Reduced liability, lower incident costs, and a more resilient organization. |
Ultimately, clinging to reactive tools means you'll always be one step behind. Proactive prevention, on the other hand, puts you in control, allowing you to manage human-factor risk intelligently, ethically, and effectively.
A New Standard: Proactive Prevention With Ethical AI
The old surveillance-based tools are failing. That leaves every leader in compliance, risk, and HR asking the same critical question: How do you stop a threat you can't see coming without creating a culture of distrust? The answer is a complete paradigm shift, moving away from reactive policing and toward proactive, ethical risk governance. This new standard isn't about watching employees; it's about understanding organizational risk signals.

This modern way to define insider threat management is built on a foundation of respect for employee dignity and unwavering compliance with regulations like the Employee Polygraph Protection Act (EPPA). Logical Commander’s E-Commander platform completely rejects invasive methods like monitoring personal emails or analyzing keystrokes—tactics that are not only legally dicey but also poison employee morale.
Instead, our AI-driven platform acts as a central nervous system for your organization's risk intelligence. It ethically connects and analyzes scattered, business-related data points you already have. This isn't spying. It's about finally seeing the whole picture.
How Ethical AI Proactively Identifies Risk
An advanced AI human risk mitigation system doesn’t look for "bad people." It looks for patterns and connections that point to elevated human-factor risk. By analyzing non-personal, work-related information, it can surface the critical warning signs long before they escalate into damaging incidents.
This process is about smart connections, not surveillance:
Centralizing Risk Data: It pulls together relevant, business information from various systems to create a single, unified view of organizational risk.
Identifying Conflicts of Interest: It can spot undisclosed relationships or external business activities that might compromise an employee's judgment or lead to fraud.
Analyzing Integrity Signals: It detects patterns suggesting a higher likelihood of misconduct or ethical lapses without making judgments about an individual's character.
Respecting Privacy Boundaries: It operates strictly within an EPPA compliant platform, guaranteeing no analysis ever crosses into legally or ethically forbidden territory.
This approach gives leadership the chance to intervene constructively and preventatively. It’s all about managing risk, not punishing people.
The new standard of risk prevention isn't about catching someone in the act. It’s about identifying the confluence of risk factors that make an act possible and addressing them before damage occurs, preserving both institutional integrity and employee dignity.
Moving From Policing to Governance
This proactive model is a fundamental break from outdated, ineffective alternatives like UAM and DLP. While traditional tools treat employees as potential suspects, an ethical AI platform like E-Commander empowers the organization with foresight. It shifts the entire focus from costly, after-the-fact investigations to intelligent, forward-looking risk governance.
A core principle of modern risk prevention, especially against insider threats, is adopting a Zero Trust Security model. The "never trust, always verify" philosophy aligns perfectly with an ethical AI approach. Both strategies prioritize verification and risk assessment over blind faith, creating a far more resilient and secure environment.
Ultimately, this allows organizations to define insider threat management not as a punitive function but as a strategic capability. It protects the bottom line, safeguards your reputation, and builds a stronger, more resilient culture based on integrity and mutual respect. This is how you get ahead of human-factor risk—ethically, effectively, and intelligently.
Take Control of Your Internal Risk Landscape
Defining an insider threat is a good starting point, but taking decisive action is what actually protects your organization. You now see the full spectrum of risk—from the calculated sabotage of a malicious insider to the honest mistake of a well-meaning employee. You also see why traditional, reactive tools consistently fail to provide any real protection.
Clinging to outdated surveillance and forensic methods is a direct acceptance of unnecessary risk. The immense costs of inaction, measured in millions of dollars, lost intellectual property, and shattered reputations, are too high to ignore. Waiting for an incident to happen before you respond is no longer a viable or defensible business strategy. The operational and legal liabilities are simply too great.
Embrace a Proactive and Ethical Approach
It’s time to move beyond the failed paradigm of reactive policing. A modern approach to human capital risk management is proactive, non-intrusive, and fundamentally ethical. It recognizes that the vast majority of internal risk isn’t born from malice but from human factors that can be identified and managed before they escalate.
By embracing a new standard rooted in AI-driven preventive risk management, you can shift from a posture of damage control to one of strategic foresight. This isn't about invasive monitoring; it’s about ethically analyzing organizational risk signals to gain the intelligence needed to act preventively. This method protects your bottom line, reinforces your compliance framework, and preserves employee dignity.
The most significant advantage of a proactive strategy is control. It empowers your organization to manage human-factor risk on your own terms, guided by intelligence and ethics, rather than being forced to react to a crisis created by someone else.
The New Standard in Risk Management
You are now equipped with a clear understanding of what it means to truly define insider threat and recognize the shortcomings of legacy systems. This knowledge is your opportunity to lead a critical change within your organization—a change that protects its finances, its reputation, and its people.
Making this shift is about more than just adopting new technology; it’s about committing to a higher standard of governance and integrity. It’s about building a resilient organization that can anticipate and neutralize risk before it ever materializes. The next step is to see how this new standard works in practice.
FAQ on Insider Threats
When you start digging into the world of internal risk, a lot of questions pop up. It's a complex topic, but getting the fundamentals right is crucial. Let's break down some of the most common questions leaders ask when trying to protect their organizations from the inside out.
Here are some quick answers to the questions we hear most often.
Question | Answer |
|---|---|
What's the difference between insider risk and an insider threat? | Think of insider risk as the potential for harm. It’s a broad category that includes unintentional mistakes, like an employee accidentally emailing a sensitive file to the wrong person. An insider threat is the malicious side of that risk, where someone intentionally acts to cause damage, like stealing intellectual property for personal gain. |
Is a modern prevention platform the same as employee monitoring software? | Not at all. Traditional monitoring tools are surveillance-based—they watch keystrokes or record screens to reactively catch bad behavior. A modern, ethical platform like Logical Commander’s E-Commander analyzes business-related risk data to proactively identify risk signals before an incident, all without invasive surveillance. It’s about prevention, not policing. |
Does an employee clicking a phishing link count as an insider threat? | Absolutely. This is a perfect example of a negligent or compromised insider. While the employee didn't mean to cause harm, their authorized access was the gateway for the external attack. This is why any effective strategy has to account for human error, which is far more common than deliberate sabotage. |
Can you really prevent insider threats without surveillance? | Yes, and it's a smarter, more effective approach. True prevention isn't about watching everyone; it's about understanding risk indicators. By using AI to analyze business-related intelligence within a strict, EPPA-compliant ethical framework, you can spot and address risks—like a conflict of interest or a need for policy reinforcement—without destroying employee privacy or morale. |
Getting these distinctions right is the first step. It helps shape a strategy that is not only more effective at protecting your organization but also builds a culture of integrity rather than one of suspicion.
Ready to move from a reactive posture to proactive prevention? Logical Commander provides the ethical, AI-driven platform to manage human-factor risk without invasive surveillance. See how our EPPA-compliant solution can protect your organization's finances, reputation, and people.
%20(2)_edited.png)
