How to Prevent Employee Theft: Effective Strategies for 2026
- Marketing Team

- Oct 13, 2025
- 13 min read
Updated: Nov 9, 2025
When it comes to stopping employee theft, the old playbook of clear policies, background checks, and a "positive work culture" is a good start, but it's no longer enough. The challenge for modern businesses is identifying internal risks before they escalate into significant losses, all without creating a culture of distrust. This is where Logical Commander's ethical, AI-powered internal risk management software provides a decisive advantage, helping you protect assets while upholding human dignity.
The True Cost of a Trusted Insider Threat

Employee theft is far more than just missing cash or inventory. It's a quiet poison that wrecks morale, dissolves trust, and leaves your business wide open to serious operational risks.
The financial bleed is staggering. U.S. businesses are losing around $50 billion a year to internal theft, a figure that jumped 8% in the last year alone. This isn't just a rounding error; it’s a critical vulnerability that traditional security—often focused on outside threats—completely misses.
Beyond the Balance Sheet
The real damage goes way beyond the direct financial hit. Think about the collateral damage:
Destroyed Morale: The moment theft comes to light, an ugly cloud of suspicion hangs over your honest, hardworking employees. Teamwork dies.
Reputational Harm: If that theft involves a data breach or customer fraud, the damage to your brand’s reputation can be permanent.
Operational Paralysis: Investigations suck up time, energy, and resources. Your team gets pulled away from their real jobs to clean up the mess.
Real-World Scenario: A mid-sized tech firm discovered a trusted, senior employee had been quietly funneling proprietary code to a competitor for months. Their existing security saw nothing because it wasn't designed to look for subtle shifts in behavior from a "trusted" source. The theft was only discovered after a product launch failed, costing them market share and millions in R&D.
This is why reactive investigations are a failing strategy. They are expensive, disruptive, and always, always too late. You can dig deeper into the true cost of reactive investigations to see why a proactive stance is the only one that makes sense.
Adopting a Proactive Defense
This kind of all-too-common scenario is exactly why a modern, proactive approach is essential. Instead of waiting for the alarm to sound after the fact, you need systems that can ethically and non-intrusively identify risk indicators before a line is crossed.
By shifting from reactive enforcement to proactive risk management, businesses can protect their assets while fostering a culture of integrity and respect. This is where ethical AI becomes a powerful ally for HR, Compliance, and Security teams.
This guide will show you how to build that resilient defense. We'll start with the foundational policies and move toward integrating AI-powered solutions like Logical Commander, which spots risk indicators before they become six-figure breaches—all while maintaining a culture of respect and human dignity.
Crafting Anti-Theft Policies That Actually Work

Your first line of defense against internal theft isn't a camera or a security guard—it's a clear, comprehensive, and well-communicated policy. But let's be honest, a dusty document filed away in a shared drive is useless.
To be effective, your policy must be a living part of your company culture. It needs to set unambiguous expectations and serve as the foundation for an ethical and secure workplace.
This isn't just about listing "don'ts." A powerful policy uses plain language to define what theft actually means, covering everything from physical inventory and cash to intellectual property and data. It also has to tackle the more subtle forms of theft that quietly eat away at your bottom line. Beyond general theft, businesses need a specific plan to prevent time card fraud, which can snowball into significant financial losses.
Key Components of an Effective Policy
A robust policy leaves no room for misinterpretation. Ambiguity is the enemy of compliance, so every detail matters.
Broad Definitions of Theft: Clearly state that theft includes tangible assets (cash, equipment, inventory), intellectual property (client lists, code, trade secrets), and company time (falsifying timecards, excessive personal activities).
Explicit Consequences: Detail the disciplinary actions for violations, ranging from verbal warnings and retraining to immediate termination and potential legal action. This removes any guesswork about the seriousness of an offense.
Confidential Reporting Procedures: Provide a safe, anonymous channel for employees to report suspicious activity without fear of retaliation. Your honest employees are often your best source of intel.
Constant Accessibility: Don't bury the policy. It should be easily accessible in your employee handbook, on the company intranet, and reviewed during onboarding and regular training sessions.
From Policy to Practice
The real impact comes from how you bring a policy to life. A logistics company slashed its inventory shrinkage by 30%. They didn't just write a new policy; they paired it with mandatory, non-accusatory training sessions for everyone, from warehouse staff to senior management.
The goal of a policy isn't to create an atmosphere of suspicion. It's to establish a shared understanding of integrity. It protects honest employees and the business simultaneously, creating a framework where proactive tools can do their job effectively.
That experience highlights a critical insight: a policy is only as strong as its communication and enforcement. It has to be discussed openly and applied consistently across every level of the organization.
When your team understands the rules and sees them applied fairly, the policy transforms from a static document into a dynamic cultural standard. This groundwork is absolutely essential before you even think about layering on more advanced internal risk management software. Without this clear foundation, even the most powerful tools will struggle. It all starts by setting clear, enforceable expectations for everyone.
Hiring for Integrity with Ethical Screening
Real theft prevention doesn't start with security cameras or inventory counts. It begins long before a new hire even walks through the door—it's baked right into your hiring process.
Traditional background checks are a good first step, but they only give you a static picture of someone's past. To build a team that's genuinely resilient against internal threats, you have to go deeper with a more dynamic, ethical approach to screening that respects privacy while still flagging potential risks.
The foundation is always solid candidate vetting. A comprehensive pre-employment screening process is non-negotiable for identifying red flags and hiring people with a demonstrated history of integrity. This establishes a baseline of trust from day one.
But here’s the thing: a one-time check doesn’t account for the pressures and personal circumstances that can change over time, influencing even the best employee's behavior down the road.
Moving Beyond Traditional Checks
Relying solely on criminal records and calling a few references leaves some serious gaps in your defense. Modern, ethical integrity assessments are designed to fill them. Instead of judging someone on past events, these assessments look at an individual's ethical consistency and how well their values align with your company's.
This is more important than ever. For instance, one study found that a staggering 56.8% of millennial employees admitted to theft-related offenses. This isn't about pointing fingers at a generation; it's about recognizing that we need more nuanced prevention strategies than a simple background check can provide. (You can find more workplace theft statistics on smbguide.com).
An ethical, privacy-first approach shifts the focus from "Is this person trustworthy?" to "Does this person's ethical framework align with our company's?" This non-intrusive method respects candidate privacy while providing a much clearer view of human capital risk.
An EPPA-Compliant AI Solution
This is exactly where an AI-powered, EPPA-compliant tool like Logical Commander’s Risk-HR solution comes in. It analyzes how candidates respond to situational judgment questions to spot risk indicators, all without using intrusive or biased methods. The system focuses on ethical consistency, not "truth verification," which keeps the entire process fair and compliant.
Imagine a financial services firm hiring for a role with access to sensitive client data. The traditional background check comes back clean. But by using our Risk-HR solution, the firm discovers one candidate shows major inconsistencies in their ethical decision-making when faced with scenarios about data privacy.
This isn't a mark against their character. It's simply a clear signal that their approach doesn't align with the firm's strict compliance culture. The company confidently chooses another candidate, preventing a potential insider threat before they ever get a company ID badge.
Actionable Insights You Can Apply:
Integrate Ethical Screening Early: Introduce EPPA-compliant integrity assessments at the pre-hire stage to identify human capital risks before making an offer.
Focus on Value Alignment: Use screening results to discuss ethical scenarios during interviews, ensuring a candidate's decision-making process aligns with your corporate values.
By bringing this kind of technology into your process, you’re not just hiring someone to fill a seat. You're investing in an individual whose integrity truly aligns with your mission.
Request a demo to see how our Risk-HR solution can ethically detect internal human risks from day one.
Using Ethical AI to Detect Real-Time Internal Risks
While strong policies and ethical hiring are your foundation, technology is what gives you a real edge in stopping employee theft before it happens. Traditional surveillance is often reactive and invasive, breeding a culture of mistrust. Modern, ethical AI flips that script. It allows you to spot risk indicators in real time without making your employees feel like they’re constantly being watched.
AI-powered risk management software, like Logical Commander’s E-Commander platform, analyzes behavioral and communication metadata—not the content itself. It looks for anomalies that could signal fraud, data theft, or other internal threats.
Crucially, it does all this while strictly adhering to privacy laws like GDPR and CPRA, focusing on patterns of behavior, not personal conversations.
A Proactive, Privacy-First Approach
This technology is specifically designed to be non-intrusive. It doesn't read private emails or listen to phone calls. Instead, it flags subtle shifts in digital behavior that deviate from an established baseline.
Think of an unusual spike in data downloads after hours, or an employee suddenly communicating with unauthorized external domains. These are the kinds of red flags the system is built to catch.
This approach gives your teams an early warning about potential risks, letting you step in before a small problem becomes a major incident. It also gets HR, Security, and Compliance on the same page by providing a unified, data-driven view of what's happening across the organization.
Real-World Scenario: Averting a Data Breach
A financial services firm integrated the E-Commander platform into its security stack. The AI quickly flagged a subtle but consistent pattern: an employee in the wealth management division began accessing and downloading client files at unusual hours, far outside their normal workflow. The system also noted encrypted files being sent to a personal cloud storage account—a clear policy violation.
Because the alert came in real time, the firm’s security and compliance teams were able to intervene immediately.
They discovered the employee was getting ready to sell a confidential client list to a competitor. That single, data-backed intervention prevented a catastrophic data breach, saving the firm from millions in potential losses and severe reputational damage.
The Advantage of Ethical AI Over Manual Surveillance
The data below really highlights the efficiency and compliance benefits of an ethical AI system compared to traditional, manual methods for spotting internal risks.
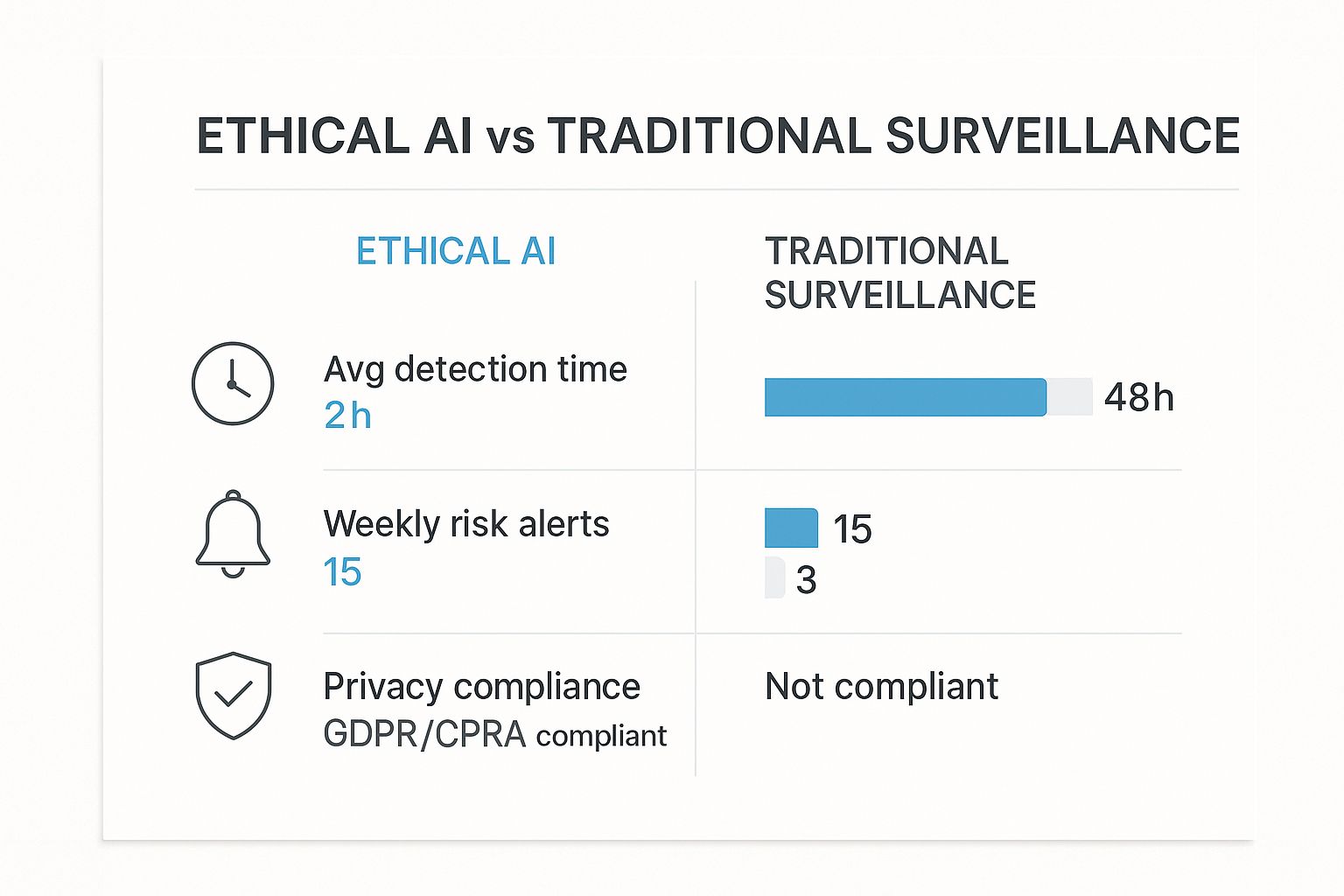
As you can see, ethical AI delivers faster detection and more relevant alerts, all while ensuring you stay fully compliant with modern privacy laws.
The table below breaks down the key differences between the old way of doing things and a modern, ethical AI solution.
Comparing Traditional vs AI-Powered Prevention Methods
Feature | Traditional Methods | Ethical AI (Logical Commander) |
|---|---|---|
Approach | Reactive (investigates after an incident) | Proactive (detects risk indicators in real time) |
Data Focus | Content-based (reads emails, monitors screens) | Metadata-based (analyzes patterns, not content) |
Privacy Impact | High; often invasive and erodes trust | Low; designed to be privacy-first and non-intrusive |
Detection Speed | Slow; relies on manual review or whistleblowers | Instant; automated alerts for immediate response |
Accuracy | Prone to false positives and human bias | High; AI models identify true anomalies |
Compliance | Difficult to align with GDPR, CPRA, etc. | Built for compliance; ISO 27001/27701 certified |
Ultimately, the goal isn't just to catch bad actors but to create a system that proactively protects the company and its trustworthy employees without violating privacy.
Actionable Insights For Implementation
Integrating this kind of technology doesn't mean ripping out your entire security infrastructure. It's about augmenting what you already have with smarter, more focused tools.
Here’s how to get started:
Define Your Risk Indicators: Get your HR, Legal, and Security teams in a room to identify the specific behaviors that pose the greatest threat. This could be anything from intellectual property theft to financial fraud. Tailor your AI's monitoring parameters to these specific risks.
Integrate and Automate: Connect the AI platform to your existing communication and IT systems. Set up automated alerts that notify the right people across departments when a high-priority risk is detected. A rapid, coordinated response is key. To dig deeper into what these red flags look like, check out our unethical behavior at the workplace with an AI-powered guide.
Logical Commander stands apart with its privacy-first design, which is ISO 27001/27701 certified, and its ability to deliver real-time detection with measurable ROI.
By focusing on ethical consistency rather than invasive surveillance, you can effectively prevent employee theft while upholding a culture of trust and respect. This proactive stance not only protects your assets but also strengthens your organization's integrity. It empowers you to turn your security strategy from reactive to preemptive.
Building a Culture That Deters Theft Naturally

When it comes to preventing employee theft, technology is a powerful ally. But it’s not the whole story. The single most sustainable defense you can build is a positive workplace culture where people feel genuinely valued and respected.
It’s simple, really. When employees are engaged and feel like they’re part of a mission, the temptation to steal plummets. This strategy gets to the root of the problem, rather than just treating the symptoms.
And the problem is huge. Shockingly, studies show that internal theft is a contributing factor in nearly 30% of all business bankruptcies. That’s a staggering figure that highlights just how critical a proactive, culturally-focused approach is. You can dig deeper into the scope of employee theft at getsafeandsound.com.
A human-centric security strategy isn't "soft"—it's smart. An employee who feels respected, heard, and fairly compensated is far less likely to rationalize stealing from their employer.
Fostering Transparency and Trust
Building this kind of culture has to start at the top. It requires intentional actions that prove to your team that their well-being and integrity are more than just buzzwords.
Implement a Genuine Open-Door Policy: This is more than just a phrase. Leaders need to be approachable and actively listen to concerns without judgment. The goal is psychological safety.
Provide Truly Anonymous Reporting Channels: People won't report suspicious behavior if they fear retaliation. Solutions like Logical Commander's SafeSpeak module offer a secure, confidential outlet they can actually trust.
Consistently Reward Ethical Behavior: Publicly recognize employees who demonstrate high integrity. This sends a clear message that how you achieve results is just as important as the results themselves.
From Culture to Actionable Insight
Think about a real-world scenario. A retail chain was seeing a spike in inventory shrinkage across several stores. Instead of launching an intimidating investigation, management decided to focus on the work environment.
They improved scheduling, increased communication from leadership, and started a recognition program for teams with the lowest shrinkage rates. The result? Within six months, theft-related losses dropped by 40%. The solution wasn't more cameras; it was a better culture.
This is where technology and culture intersect perfectly. Non-intrusive tools from Logical Commander can provide high-level insights into underlying cultural issues—like departmental friction or signs of widespread burnout—without ever targeting individuals.
By analyzing anonymized patterns, leaders can spot and address the root causes of discontent before they fester into actions like theft. You can learn more about how integrity directly impacts your bottom line by exploring the cultural ROI of integrity in our detailed article.
This blend of human-centric leadership and ethical analytics creates a powerful defense that not only stops theft but also builds a stronger, more resilient organization.
Your Top Questions About Employee Theft, Answered
When you're trying to stop internal theft, a lot of practical questions come up. Let's cut through the noise and get you some clear, straightforward answers. The goal is to build a strategy that’s both effective and ethical, blending smart technology with a culture of trust—all while staying on the right side of the law.
What's the Single Most Effective Way to Stop Employee Theft?
There isn’t one. The most effective strategy is always a multi-layered one.
Think of it like securing a building. You wouldn't rely on just a single lock on the front door, right? You'd have alarms, cameras, and strong access protocols. The same logic applies here. A truly resilient anti-theft program weaves several key elements together:
Rock-Solid Policies: Start with clear, written rules. Define what theft means in all its forms—from taking office supplies to intellectual property—and spell out the consequences. No grey areas.
Smarter Screening: Don't wait until it's too late. Use ethical, pre-employment integrity assessments to spot red flags before you make a hire.
A Positive Culture: This is a big one. When people feel valued, respected, and part of a team, they are far less likely to act out. A great culture is a powerful, natural deterrent.
Modern Tech: Use tools built for today's risks. AI-powered platforms like E-Commander are designed to spot weird patterns and anomalies in real-time, catching things a human would miss.
None of these work in isolation. A great policy is just a piece of paper without a strong culture to back it up. And even the best culture can have blind spots that only technology can uncover.
Is It Legal to Monitor Employees to Prevent Theft?
Yes, but you have to be incredibly careful about how you do it. This is where many companies get into trouble.
Laws like the EPPA, GDPR, and CPRA draw firm lines in the sand to protect employee privacy. Old-school surveillance methods often step right over those lines, creating massive legal and ethical headaches.
This is exactly why modern, ethical AI solutions were developed. A platform like Logical Commander is built on a privacy-first foundation. It works by analyzing behavioral metadata—the "how" and "when" of actions—to find risk indicators, not by reading the content of private messages. This non-intrusive approach keeps your prevention efforts fully compliant and shows respect for your team.
The real shift is from invasive surveillance to ethical risk detection. When you focus on spotting anomalous patterns instead of digging through personal content, you protect the organization without crossing critical legal or ethical boundaries.
How Do I Put an Anti-Theft Program in Place Without Killing Morale?
This is a crucial question. The answer comes down to two things: transparency and positive framing. Your team has to understand that this is about protecting the company and all the honest people in it, not about playing "big brother."
First, communicate the "why." Don't just roll out a new policy or tool. Explain that the goal is to protect company assets and data, which ultimately protects everyone's jobs and the integrity of the workplace.
When you introduce new technology, be explicit that it’s designed to spot unusual patterns, not to scrutinize individuals. Frame it as a safety net, not a spyglass.
Finally, always balance new security measures with trust-building initiatives. Introduce an anonymous reporting hotline. Create a program to reward and recognize ethical behavior. When you do this, your anti-theft program becomes just one piece of a much larger commitment to building a supportive, high-integrity culture.
Ready to see how ethical AI can proactively protect your organization without compromising trust? Logical Commander offers a suite of tools designed for modern internal risk management. We also empower partners through our global ecosystem to deliver these ethical solutions worldwide. Request a demo to learn how our platform provides real-time detection with measurable ROI, or consider joining our PartnerLC network to bring these solutions to your clients.
Know First. Act Fast. Ethical AI for Integrity, Compliance, and Human Dignity.
%20(2)_edited.png)
