What is insider threats: A Practical Guide to Protecting Your Business
- Marketing Team

- Jan 8
- 16 min read
When you hear "what is insider threats," it’s easy to picture a disgruntled employee sneaking out of the office with a hard drive full of company secrets. While that scenario is definitely part of the story, it’s only a small piece of a much larger business liability.
An insider threat is any business risk that comes from someone who already has authorized access—employees, contractors, or even partners. It covers everything from malicious actions like outright theft to unintentional mistakes that can spiral into huge financial losses, regulatory fines, and a damaged reputation.
This isn't a cyber issue; it's a complex human-factor challenge that starts and ends with people. Managing it demands a strategy built on proactive prevention, not costly and intrusive reactive investigations.
Understanding Insider Threats Beyond the Surface

At its core, an insider threat is any security or operational risk originating from within your trusted circle. What makes these threats so damaging is that they come from people who already have legitimate access to your systems, data, and processes.
Unlike an external hacker who has to break down the door, an insider is already inside. They operate from a position of trust, which makes their activities incredibly difficult for traditional, outward-facing security tools to spot. After all, those tools were built to keep outsiders out, not to analyze the risks posed by insiders. This isn't a cyber problem; it's a human-factor risk.
The Two Faces of Insider Risk
To fully grasp what is insider threats, you have to understand that they come in two main forms. Each stems from different motives and requires a different preventive strategy.
The Malicious Insider: This is the intentional actor. They might be motivated by financial gain, revenge, or corporate espionage. They knowingly abuse their access to commit fraud, sabotage a project, or steal valuable intellectual property. This is a deliberate breach of trust with severe business impact.
The Accidental Insider: This individual causes harm unintentionally. Their actions are usually the result of a simple mistake, negligence, or being deceived by a phishing attack. Think of an employee accidentally misconfiguring a database, sending a sensitive file to the wrong recipient, or clicking a malicious link that compromises the network.
Surprisingly, recent data shows that accidental insiders are often the most costly. Their mistakes can fly under the radar for months, quietly compounding the damage. This drives home a critical point: effective internal risk management isn't about policing your team with surveillance. It's about building stronger, more resilient processes and fostering a culture where people can do their jobs safely and ethically.
Here's the business impact: insider-related incidents now account for nearly 60% of all data breaches. This is not a niche problem. It is a central operational risk that requires a modern, proactive approach—one focused on ethical prevention before the damage is done.
To give you a clearer picture, let's break down these core ideas. The table below simplifies the key components of an insider threat, from the types to their ultimate impact on the business.
Insider Threat Key Concepts at a Glance
Threat Component | Description |
|---|---|
Origin | Comes from individuals with legitimate access (employees, contractors, partners). This is a human-factor risk. |
Types | Divided into malicious (intentional harm) and accidental (unintentional mistakes). |
Primary Motives | Malicious: financial gain, revenge, espionage. Accidental: negligence, error, being deceived. |
Business Impact | Can lead to financial loss, data breaches, regulatory penalties, and severe reputational damage and liability. |
Thinking about these components frames the issue correctly. It's not a cyber problem; it's a business problem that impacts every department, from HR and Legal to Compliance and Security.
To tackle insider threats, you first need a solid grasp of organizational vulnerabilities. For a great primer on the fundamentals, you can check out a complete guide to what risk management is. From there, spotting these risks requires more than watching network traffic; it means understanding the subtle signals that appear before an incident. You can learn more by reading up on key insider threat indicators.
The Hidden Costs of Human Factor Risk

The real story of an insider threat is never just about one event. It’s a story told in lost revenue, operational gridlock, and shattered stakeholder confidence. When decision-makers ask, "what is insider threats," they are really asking about the impact on the bottom line and business liability. The financial damage goes far beyond the initial incident, kicking off a chain reaction that stalls projects, triggers regulatory fines, and can cripple a company's reputation.
Most organizations completely underestimate the true financial toll. They fixate on the direct cost of stolen data or funds, but that's just the tip of the iceberg. The real damage is buried in the secondary expenses that accumulate rapidly, and that’s where the most significant business pain is felt.
Beyond Direct Financial Loss
The most obvious impact from an insider incident is the direct loss of cash or assets. But the financial bleeding doesn't stop there. Organizations are then liable for a host of follow-up expenses that are often just as damaging, if not more so.
These secondary costs always include:
Investigation and Remediation: Suddenly, you’re paying for forensic experts and legal teams, pulling your own people off revenue-generating jobs just to figure out what happened and plug the holes. This is the high cost of reactive failure.
Regulatory Fines: A single breach that violates regulations like GDPR, HIPAA, or CCPA can trigger severe financial penalties that easily run into the millions.
Operational Disruption: Business grinds to a halt. Key teams are pulled away from their core functions to manage the crisis, leading directly to missed deadlines, lost productivity, and stalled growth.
This is exactly why a reactive approach is so dangerous. Waiting for an incident to happen guarantees you'll face these escalating costs and liabilities. Understanding the true cost of reactive investigations is the first step toward seeing the immense business value of a proactive, preventive strategy.
The Staggering Price Tag of Insider Risk
The scale of this problem is growing at an alarming rate. Recent data shows a troubling trend: insider threats have become one of the most persistent and costly challenges for businesses today. The number of organizations hit by insider attacks jumped from 66% to 76% in just a few years.
During that same window, the total average annual cost of dealing with insider risks exploded from $8.3 million to $17.4 million—a staggering increase of over 109.6%. What makes this even more concerning is that 71% of organizations admit they feel at least moderately vulnerable to these threats. You can discover more insights about these insider threat statistics and what they mean for business liability.
The data paints a clear picture: ignoring the human factor is a recipe for financial disaster. The old model of waiting for an incident and then reacting is no longer sustainable from a risk, compliance, or financial standpoint.
The real risk isn't just the incident itself, but the chain reaction of liability it triggers. A single data leak can lead to a loss of customer trust, which in turn leads to churn and a damaged brand reputation that can take years and significant investment to rebuild.
The Unseen Operational and Reputational Damage
While the financial metrics are stark, the non-monetary costs can be just as devastating. These intangible damages strike at the long-term health, governance, and stability of the entire organization.
Just consider these impacts:
Eroded Customer Trust: Customers who feel their data isn't safe will simply take their business elsewhere. Rebuilding that trust is a long, uphill battle that directly impacts revenue.
Damaged Employee Morale: When incidents are met with intrusive, surveillance-heavy investigations—which are often not EPPA-aligned—it breeds a culture of suspicion and fear, tanking productivity and retention.
Loss of Competitive Advantage: The theft of your intellectual property—like trade secrets or product roadmaps—can hand a massive advantage straight to your competitors.
Ultimately, the hidden costs of human-factor risk prove that a proactive, ethical, and non-intrusive approach to internal risk management isn't just a compliance checkbox. It’s a core business necessity for protecting the bottom line.
Why Your Current Security Is Not Enough
If you’ve invested heavily in firewalls, endpoint protection, and other perimeter security, you’ve built a strong fortress. That’s essential for external threats. But those tools all share a fundamental blind spot: they’re designed to stop attackers from getting in, not to understand the human-factor risks coming from people who are already inside.
This creates a dangerous gap in your risk management framework. When a threat comes from a trusted employee, contractor, or partner using their legitimate credentials, traditional security systems are often completely oblivious. They see an authorized user accessing authorized data and sound no alarms—even if the intent is malicious or the action is dangerously negligent. This isn't a cyber failure; it's a failure to address human risk.
The Problem with Outward-Facing Security
Perimeter security works on a simple premise: keep unauthorized people out. That model completely breaks down when the risk isn't an intruder but a trusted insider. Your firewall can't stop a sales manager from emailing a sensitive client list to a personal account, and your antivirus software won't flag a project manager downloading proprietary plans onto a USB drive.
These actions fall under the umbrella of authorized behavior, which makes them invisible to tools that weren't built to understand context or intent. This is precisely why a different, human-centric approach is needed. In fact, data shows that insider actions are behind 45% of all file security breaches, making them a primary threat vector that exploits legitimate access through everyday operations. You can learn more about how insiders exploit authorized system access on kiteworks.com.
The Pitfalls of Surveillance and Reactive Methods
Some organizations, recognizing this gap, turn to outdated surveillance methods like monitoring employee emails or tracking keystrokes. This strategy is not only ineffective but also introduces enormous legal, ethical, and cultural problems. It operates on a foundation of distrust, treating employees like suspects and creating a toxic workplace.
This approach is fundamentally flawed and legally risky. It damages morale and exposes the organization to significant liabilities under regulations like the Employee Polygraph Protection Act (EPPA), which strictly prohibits coercive or intrusive practices. These tools are the opposite of ethical risk management.
Worse yet, surveillance tools generate a massive amount of noise, making it nearly impossible to separate real risks from normal business activity. Security teams are left chasing an endless stream of false positives while the real threats continue to slip through the cracks. For a deeper analysis, explore our guide on the limitations of traditional insider threat detection tools.
The Clear Need for a New Standard
The failure of both perimeter security and invasive monitoring makes one thing crystal clear: a new standard is required to manage human-factor risk. The future of internal risk management isn't about building higher walls or watching employees more closely. It’s about adopting a smarter, more modern approach focused on proactive and ethical prevention.
This new standard, championed by platforms like Logical Commander's E-Commander, moves away from the old model of reaction and blame. Instead, it centers on identifying risk signals within business processes before they can escalate into incidents. By doing so, organizations can protect their assets, maintain compliance, and foster a culture of integrity—all without compromising employee dignity or legal standards. The goal is prevention, not reaction.
Adopting The New Standard Of Ethical Prevention
For far too long, the approach to internal risk has been stuck in a costly, backward-looking cycle. Organizations wait for the damage—the data leak, the compliance fine, the fraud—and then launch expensive, intrusive investigations to piece together what went wrong.
This old model is fundamentally broken. It fails to stop the loss and breeds a culture of suspicion that poisons employee morale. It’s time for a fundamental shift. The new standard for managing what is insider threats is built on proactive, ethical prevention.
This modern framework, embodied by Logical Commander, is designed to protect the organization while respecting its people. It operates on a simple but powerful idea: prevention is always better than a cure. The goal is to get out of the reactive business of forensics and move into the proactive strategy of neutralizing risks before they cause harm. This protects your assets, your reputation, and your culture.
The Philosophy Of Non-Intrusive Risk Management
At the heart of this new standard is a critical distinction: the focus is on risky processes, not on individuals. This is the philosophy that drives Logical Commander's advanced AI platform, which is designed to spot risk signals within business workflows without ever resorting to invasive employee surveillance or monitoring.
Our approach doesn't involve reading private emails, tracking keystrokes, or deploying any other methods that violate privacy and create massive legal liabilities.
Instead, this ethical strategy analyzes procedural data to find anomalies, conflicts of interest, and deviations from your established policies. It's an ethical risk management framework that answers the questions that truly matter for business liability:
Are there gaps in our processes that someone could exploit?
Does an employee have conflicting roles that create an unmanaged risk?
Is someone bypassing a critical workflow in a way that exposes sensitive data?
By focusing on the "what" (the risky action) rather than the "who," you can intervene early. You can fix a broken process, provide more training, or reassign duties to eliminate a risk before it ever turns into a full-blown incident.
The diagram below drives this point home. It shows how traditional security is so focused on external threats that it leaves a huge, unguarded gap where insider threats operate freely.
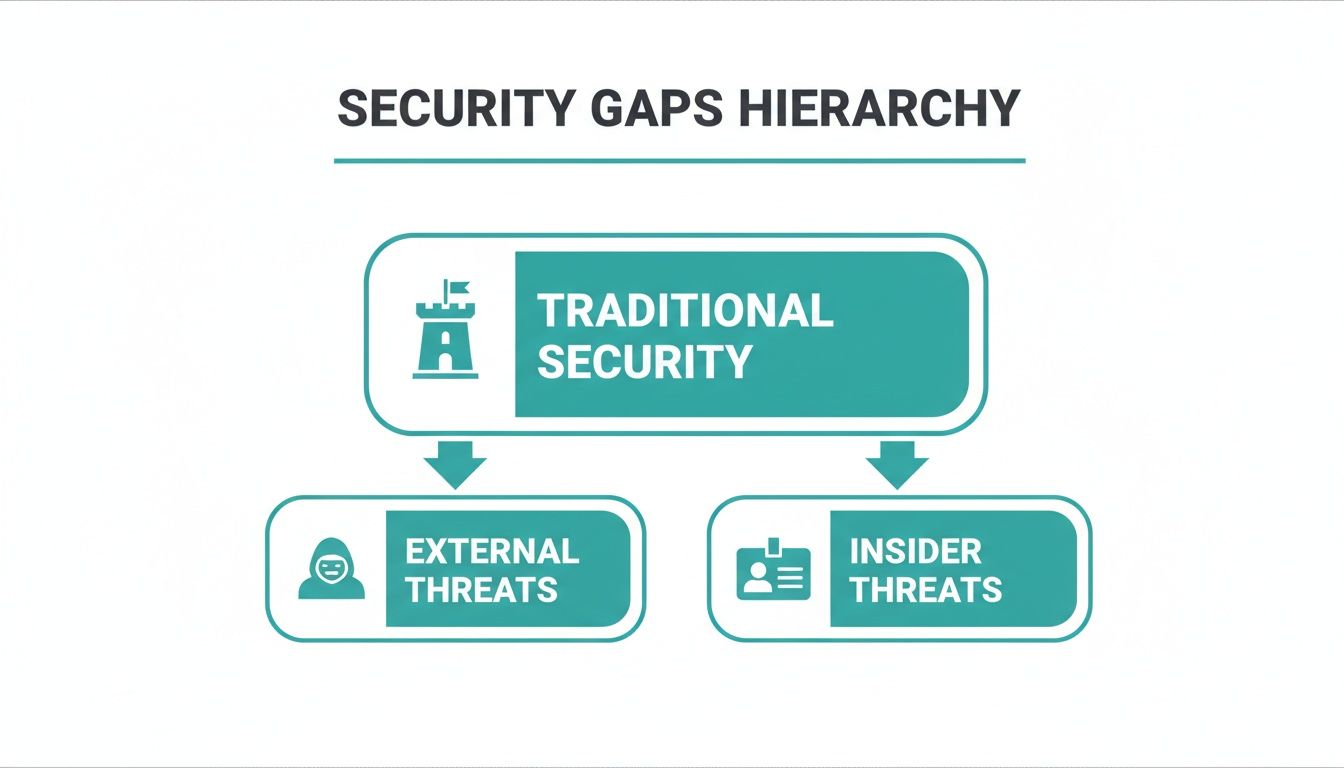
This visual makes a critical vulnerability crystal clear. While we pour resources into building digital walls, the internal human-factor risk is often a massive blind spot for conventional security. Logical Commander is built to close that gap.
Moving From Reactive To Proactive
The contrast between the old way and the new standard couldn't be more stark. A reactive investigation is an expensive admission of failure. Proactive prevention, powered by AI human risk mitigation, is a strategy for building resilience and true protection.
The new standard isn't about replacing human judgment; it's about empowering it. By providing objective, data-driven insights, an EPPA compliant platform like E-Commander enables HR, Legal, and Security teams to make timely, informed decisions that prevent harm and uphold organizational integrity.
The table below lays out the difference between these two worlds. It highlights why leaving the outdated, reactive model behind for a modern, preventive framework is a strategic business imperative.
Reactive Investigations vs Proactive Prevention
Attribute | Reactive Investigations (The Old Way) | Proactive Prevention (The New Standard) |
|---|---|---|
Timing | After the damage is done (data stolen, fraud committed). | Before a risk escalates into a breach or a financial loss. |
Methodology | Forensics and intrusive surveillance reviews. Highly invasive and legally complex. | Ethical risk assessments, workflow analysis, and AI-driven signal detection. Non-intrusive and EPPA-aligned. |
Focus | Assigning blame and gathering evidence for legal action. | Identifying and neutralizing risk to prevent harm from ever occurring. |
Cost | Extremely high costs from damages, legal fees, and reputational harm. | A predictable operational cost that delivers a high ROI by preventing catastrophic losses. |
Employee Impact | Creates a culture of suspicion and distrust. Destroys morale and opens the door to legal challenges. | Reinforces a culture of integrity and shared responsibility. Preserves employee dignity. |
Outcome | Damage control and recovery. | Organizational resilience, governance, and protection. |
Ultimately, adopting this new standard is a strategic business decision. It represents a move toward a smarter, more ethical, and far more effective way to manage the human-factor risks that are an inevitable part of any organization. It’s about building a resilient enterprise that can identify and address vulnerabilities from within—long before they ever threaten the bottom line.
How to Build Your Insider Risk Program
Moving from theory to a real-world plan is the single most important step in tackling what is insider threats. A strong insider risk program isn’t a piece of software you buy or a policy you write. It’s a coordinated, company-wide strategy that gets key departments working together toward one goal: proactive prevention.
It’s time to ditch the scattered, manual processes. The modern approach requires an intelligent, tech-enabled framework that helps you mitigate human-factor risks before they impact the business.
Establishing Cross-Functional Governance
It all starts with clear governance. This means tearing down the silos that traditionally separate HR, Legal, Security, and Compliance. These teams can’t operate in their own worlds anymore. They need to collaborate within a unified structure, sharing intelligence and coordinating their response to potential risks before they escalate.
A successful program needs defined roles and shared responsibilities. Each department brings a unique and essential perspective, creating a complete picture of human-factor risk across the business.
The core of this collaborative model includes:
Executive Sponsorship: The program must have visible support from leadership to secure resources and ensure it is taken seriously across the organization.
A Steering Committee: This group, with leaders from HR, Legal, Security, IT, and Compliance, should meet regularly to review risk intelligence and guide the program's strategy.
Defined Workflows: You need clear, documented procedures for how risks are identified, evaluated, and mitigated. This ensures every situation is managed with consistency, accountability, and in line with governance policies.
When you're setting up your program, it's crucial to build in preventative measures right from the start. That begins with robust pre-employment checks to head off potential human factor risks before someone is even hired.
The Central Role of an Ethical Tech Platform
Trying to manage a modern insider risk program with spreadsheets and email is a recipe for failure. You’re dealing with a massive volume of data and incredibly subtle risk indicators. This demands a central technology platform that acts as the single source of truth—the new standard in risk management. This is where an AI-driven preventive risk management solution like Logical Commander's E-Commander becomes essential.
A unified platform like Risk-HR doesn't just centralize data; it provides the analytical power to connect disparate events and reveal hidden risk patterns that are invisible to the human eye. It automates the process of risk signal detection, freeing your teams to focus on strategic mitigation instead of manual, reactive fire-fighting.
A platform built for ethical risk management ensures your program is both effective and compliant. It operates without surveillance, ensuring that all risk identification is non-intrusive and aligned with EPPA guidelines. This protects employee dignity and helps build a culture of trust and integrity. For a complete blueprint, check out your guide to insider risk management to see how all these pieces fit together.
Fostering a Culture of Awareness
Technology is only half the battle. Your program’s success ultimately hinges on your people. Ongoing training and awareness initiatives are vital for creating a risk-conscious culture where employees understand their role in protecting the organization. This can't be a one-time event; it has to be practical, engaging, and continuously reinforced.
Recent data shows just how urgent this is. While most organizations now have some kind of insider risk program, a shocking 69% still rely on informal, ad-hoc processes. This gap is incredibly costly. Organizations that contain incidents within 31 days face average costs of $10.6 million, but that number jumps to $18.7 million for those taking over 91 days to respond.
The numbers don't lie—there is a direct line between rapid, structured detection and saving millions of dollars. Ultimately, a well-built program weaves together governance, technology, and culture to create a resilient, proactive defense against internal threats.
Your First Step Toward Proactive Prevention
Simply understanding what insider threats are is a start, but awareness alone won’t protect your balance sheet or your reputation. The evidence is overwhelming: the financial and operational damage from human-factor risk is escalating, and launching a reactive investigation is an expensive admission of failure. Your traditional security tools were never designed to see this coming, leaving you with a dangerous blind spot.
It’s time to move from knowing to doing.
The new standard is ethical, AI-driven prevention, and Logical Commander offers a clear path forward. This modern approach protects your organization from the inside out—not by policing your people, but by reinforcing your processes. It allows you to identify and neutralize risks before they do any harm, which is how you build a real culture of integrity and preserve the trust you’ve earned with both employees and customers.
Embrace a New Strategy for Resilience
Making this shift means committing to a new way of thinking about internal risk. You must replace fragmented, manual processes with a coordinated, tech-enabled strategy that unites your HR, Legal, and Security teams. A modern Risk Assessments Software platform like E-Commander is the central intelligence layer that makes this possible.
This strategy is built on a few core principles:
Proactive Mitigation: The focus is on finding and fixing procedural gaps before they can be exploited, not chasing damages after the fact.
Ethical Foundation: Uphold employee dignity and maintain compliance with an EPPA compliant platform that is fundamentally non-intrusive and avoids surveillance entirely.
AI-Driven Insight: Use AI human risk mitigation to analyze complex risk signals that are impossible for humans to spot, giving you objective data for timely, confident decisions.
The ultimate goal here is to build genuine organizational resilience. When you adopt a proactive stance with Logical Commander, you transform your insider risk program from a cost center focused on damage control into a strategic asset that safeguards your most valuable resources—your data, your capital, and your people.
Join the Movement Toward Ethical Risk Management
For B2B SaaS companies, consultants, and technology partners, this shift represents a massive opportunity. Leading the charge in ethical prevention establishes you as a trusted advisor in a field with growing demand and liability. By joining our PartnerLC program, you can equip your clients with the next generation of internal threat solutions, helping them build more resilient and ethical organizations.
This is your chance to be at the forefront of the new standard in corporate governance and risk management.
Your Questions About Insider Threats, Answered
When you start digging into human-factor risk, a lot of questions come up. It's a complex topic with significant business implications. Let's tackle some of the most common ones we hear from decision-makers in Compliance, Risk, and HR.
How Can You Detect Insider Threats Without Employee Monitoring?
This is the most critical question, and it gets to the heart of modern, ethical prevention. Real internal threat detection has nothing to do with invasive surveillance. The old way of reading emails or tracking keystrokes destroys company culture, is legally risky under EPPA, and is simply ineffective.
A modern, EPPA-aligned platform like Logical Commander's E-Commander doesn't monitor people; it analyzes risk signals within your existing business workflows. By using AI to spot procedural gaps, conflicts of interest, and deviations from compliance, the system flags high-risk patterns. The focus is on what is happening (the risky action), not who is doing it, allowing you to get ahead of a problem while preserving a culture of integrity.
Is an Insider Threat Program Only for Large, Regulated Companies?
Not at all. While heavily regulated industries have clear mandates, insider threats are a universal business problem. If your company has valuable intellectual property, sensitive customer data, or critical operational processes, you are exposed. The business impact from a single incident can be devastating for any size organization.
Think of a scalable insider risk program as a fundamental part of good governance and operational resilience. The reality is, the cost of just one incident—whether it's fraud, a data leak, or a compliance breach—almost always dwarfs the investment in a preventive platform. It's a crucial strategy for any organization serious about protecting its core assets and limiting liability.
What Is HR’s Role in Managing Insider Risk?
HR is central to any modern insider risk program, and their role is far more strategic than just handling disciplinary action after an incident. HR is a key partner in shaping clear policies, running ongoing training on security and ethics, and ensuring the employee offboarding process is secure.
With a unified platform like Risk-HR, silos between HR, Legal, and Security disappear. These teams can finally collaborate effectively, sharing the right intelligence to manage human-factor risk across the entire employee lifecycle—from pre-employment to post-exit. This coordinated approach ensures the whole process is consistent, fair, and incredibly effective at preventing risk.
How Does an AI Platform Help Manage Insider Threats?
Honestly, trying to manage insider risk manually is impossible at scale. There's just too much data and not enough time. That's where AI becomes essential. An AI-driven preventive risk management platform can analyze massive amounts of procedural data in real time, spotting the subtle risk indicators that would be completely invisible to a human auditor.
It is brilliant at connecting the dots between seemingly unrelated events to reveal complex risk scenarios, like sophisticated fraud schemes or patterns of policy violations.
Most importantly, ethical AI human risk mitigation brings objectivity to the table. It delivers data-driven insights that help leaders prioritize what truly matters and take targeted, preventive action—all without the human bias that can compromise manual reviews. It empowers your teams to act decisively before a potential risk spirals into a damaging crisis.
Ready to move from chasing incidents to preventing them ethically? The Logical Commander E-Commander platform gives you the AI-driven intelligence you need to manage human-factor risk without surveillance. Protect your assets, reputation, and culture with the new standard in internal threat management.
Discover how our EPPA-aligned solution can build true resilience in your organization.
%20(2)_edited.png)
