Your Guide to Insider Risk Management
- Marketing Team

- Oct 14, 2025
- 10 min read
External hackers and sophisticated cyberattacks dominate headlines, but what if the most damaging threats are already inside your organization? Insider risk management is the strategic plan for addressing this reality. It’s how forward-thinking companies identify, assess, and mitigate risks from employees, contractors, and partners who have legitimate access to sensitive systems and data. These incidents can be accidental, negligent, or malicious, making them incredibly difficult to spot with outdated security tools. Logical Commander's AI-powered platform provides an ethical, EPPA-compliant solution, enabling organizations to detect human capital risks proactively while upholding employee privacy and human dignity.
The Hidden Threat Inside Your Walls - Your Guide to Insider Risk Management

The real challenge with insider risk is that it often looks like a normal Tuesday. Unlike a loud, brute-force attack from the outside, an internal incident can blend right in with everyday business activities.
Under our Guide to Insider Risk Management, we will conduct a specific analysis:
A great first step is a comprehensive cybersecurity risk assessment. This process is essential for mapping out what your most critical data is and, just as importantly, who can access it.
But a one-time check-up won't cut it. Legacy security systems are blind to the subtle shifts in behavior that signal a growing risk, leaving the door wide open for data breaches or fraud. This is where you need a modern approach.
Logical Commander offers an ethical, AI-powered platform designed for this new era of insider risk management. We give you the visibility needed to protect your assets without crossing the line into employee surveillance. Our approach is built on key differentiators that make our program both effective and respectful:
Ethical & Non-Intrusive AI: Our system is fully EPPA-compliant. We focus on risk indicators and behavioral patterns, not on monitoring private content or using prohibited practices like "truth verification."
Privacy-First Design: We're built from the ground up to respect human dignity. With ISO 27001/27701, GDPR, and CPRA compliance baked in, our platform protects your people while securing your organization.
Real-Time Detection and Measurable ROI: Know first and act fast. Our platform delivers immediate insights, so you can step in before a small risk mushrooms into a full-blown, costly incident.
This guide will show you how to build a resilient defense against these internal threats. By bringing HR, Security, and Compliance together with the right technology, you can protect your sensitive data and build a genuine culture of integrity from the inside out.
What Insider Risk Management Really Means Today

Let’s be clear: true insider risk management isn’t about watching over your employees’ shoulders. It’s a strategic function designed to protect your most critical assets—data, intellectual property, and reputation—from the inside out. This isn’t a reactive, people-policing model; it's a proactive, data-centric one.
Think of it like a sophisticated safety system in a large building. Its purpose isn't to spy on residents but to monitor for smoke, unusual activity, or open fire doors. The goal is to prevent a disaster before it happens, safeguarding everyone inside. An effective insider risk program works the same way, focusing on risky behaviors and data movements, not personal intent.
This distinction is crucial because most insider incidents aren’t driven by malicious actors. They actually fall into three very different categories, each needing its own unique approach.
The Three Faces of Insider Risk
Understanding who you're dealing with is the first step toward building a resilient defense. Each of these personas highlights a different vulnerability, and they all demand a nuanced, ethical response—not a one-size-fits-all security clampdown.
The Accidental Insider: This is your most common threat. It’s the well-meaning employee who unknowingly clicks a phishing link, misconfigures a cloud storage setting, or sends a sensitive file to the wrong person. Their intent isn't harmful, but the damage can be just as severe as a deliberate attack.
The Compromised Insider: This person has had their credentials stolen by an external attacker. The real threat actor then uses this legitimate access to move through your systems, steal data, and escalate privileges, all while looking like a trusted employee.
The Malicious Insider: This is the classic "bad actor"—a disgruntled employee or an opportunist who intentionally steals data for financial gain, revenge, or to take to a competitor. While less common, the damage from a single malicious act can be catastrophic.
An effective insider risk management program prepares an organization to respond to any potential data breach, regardless of the user's intent. By focusing on the data at risk, you can address the full spectrum of threats without resorting to invasive surveillance.
A Proactive, Human-Centric Solution
A forward-thinking strategy acknowledges that these risks are fundamentally human. That's why Logical Commander's E-Commander and Risk-HR platforms are designed to help you understand your organization's human capital risks ethically and effectively.
Our ethical, non-intrusive AI analyzes behavioral patterns and risk indicators to provide real-time alerts. This allows your teams—from HR and Compliance to Security and Legal—to collaborate and intervene early. You can get ahead of these challenges by reading our in-depth guide to human capital risk detection.
By focusing on aligning employee actions with your company’s ethical standards and compliance requirements, you create a stronger, more resilient organization. This approach protects your critical assets while upholding the human dignity and privacy of your workforce—a core principle of our privacy-first design.
Why Traditional Security Measures Fall Short

For years, security teams built fortresses. The goal was to defend the perimeter with firewalls, Data Loss Prevention (DLP) tools, and basic monitoring designed to keep bad actors out. But when it comes to insider risk management, that approach is like building a castle wall to stop a threat that’s already inside the courtyard.
These traditional tools are rigid. They operate on a simple, rules-based logic that blocks obvious violations, like someone trying to email a huge file named "Confidential" outside the company. That’s helpful, but it’s a tiny piece of the puzzle. They have zero context for human intent or the subtle, cumulative actions that truly signal a growing risk.
This outdated model leaves massive gaps, especially now. Workforces are distributed, data lives in the cloud, and the old security playbook just wasn't written for this reality.
The Problem of Noise and Missed Signals
One of the biggest failures of legacy tools is the deafening noise they create. Security teams are drowning in a sea of false positives—alerts triggered by legitimate work that just happens to trip a rigid rule. "Alert fatigue" is real, and it means the truly critical signals get buried in an avalanche of junk.
Traditional security asks what happened—a file was moved. A modern insider risk program asks about the context—who moved it, when, where it went, and if that behavior is a departure from their normal activity.
This is where the real danger lurks. Legacy systems are completely blind to the slow-burn threat. They might flag a single, massive data theft, but they will almost certainly miss the far more common and insidious patterns that develop over weeks or months.
Real-World Scenario: The Incremental Data TheftConsider a sales executive planning to join a competitor. A basic DLP tool would likely catch an attempt to download the entire customer database at once. Instead, they export a few dozen contacts each day for weeks, renaming files, zipping them, and uploading them to a personal cloud drive. To a traditional system, each small action is unremarkable and flies under the radar. But the pattern, when analyzed contextually, tells a clear story of deliberate data exfiltration.
The Growing Gap in Insider Threat Detection
This isn't just a theoretical problem; it’s a full-blown crisis for many organizations. Recent trends show a massive spike in insider incidents, with 76% of organizations reporting an increase in insider threat activity over the last five years. Yet, less than 30% of businesses feel they have the right tools to handle it. You can dig deeper into these numbers with the latest insider threat research.
That gap is precisely where Logical Commander’s ethical AI changes the game. Our AI-powered risk management platform moves beyond simplistic rules to analyze behavioral risk indicators in real time, giving you the context that matters.
Ethical & Non-Intrusive AI: Our EPPA-compliant system analyzes metadata and patterns without ever inspecting personal content, putting employee privacy first.
Privacy-First by Design: We are ISO 27001 certified and built to adhere to GDPR and CPRA, ensuring our technology fosters trust, not a culture of surveillance.
Cross-Department Collaboration: Our platform provides a single source of truth that enables HR, Security, and Legal to get ahead of a risk before it escalates.
By focusing on "ethical consistency" and "integrity alignment," our E-Commander platform empowers you to see the subtle patterns legacy systems can't. It’s time to move from reactive security to proactive risk mitigation and stop leaving your organization vulnerable.
The Escalating Financial Impact of Insider Incidents
Insider risks aren't just a security headache—they represent a massive and growing financial liability for organizations. When an incident happens, the costs don't stop at the initial cleanup. They ripple outward, touching everything from regulatory standing to the trust you've built with your customers.
Getting a handle on this full financial picture is the first real step in making the business case for a serious insider risk management program.
The Numbers Don't Lie
The financial fallout from insider incidents is accelerating, and the data paints a very clear picture. The chart below breaks down not only the rising costs over time but also how those costs are split between the obvious expenses and the more damaging, long-term impacts.
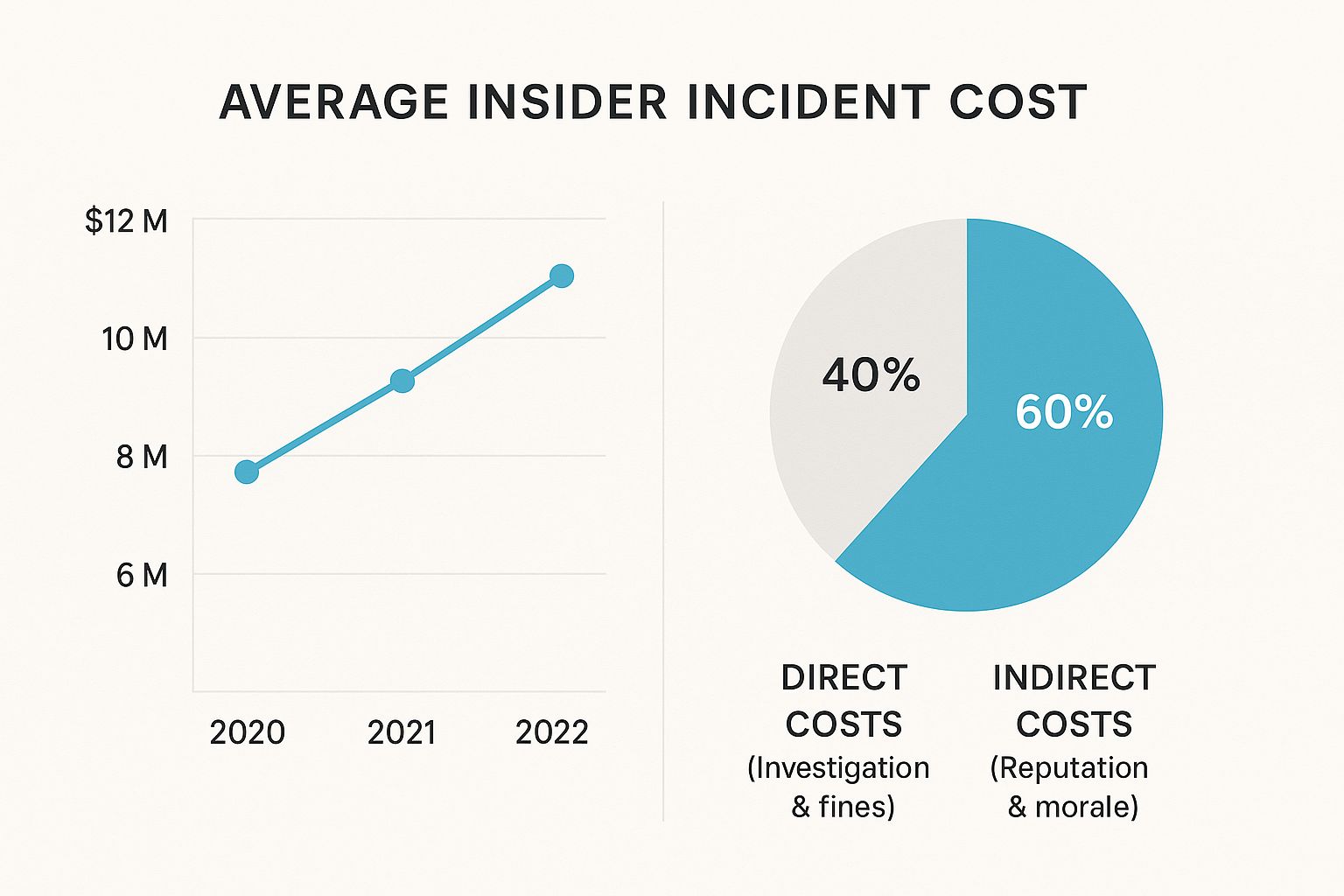
As you can see, the indirect costs—things like reputational damage and lost customer trust—are what really hurt. This is why preventing incidents before they hit the headlines is so critical.
Year-over-Year Growth in the Average Cost of an Insider Incident
The data shows a clear and troubling trend: the price tag for insider incidents is climbing steeply every year. The following table illustrates just how quickly this financial burden is growing for businesses worldwide.
Year | Average Annual Cost |
|---|---|
Year 1 | $8.3 Million |
Year 2 | $11.5 Million |
Year 3 | $15.4 Million |
Year 4 | $16.2 Million |
Year 5 | $17.4 Million |
These aren't small jumps. The surge from $8.3 million to $17.4 million in just a few years signals a global business imperative to get ahead of this problem.
There is, however, a silver lining in the data. The average time to contain an incident has improved slightly, dropping from 86 to 81 days. Speed is everything here. Organizations that can contain an incident in under 31 days save an average of $8.1 million compared to those that take over 90 days.
This proves that real-time detection and rapid response aren't just operational nice-to-haves; they are essential financial controls.
Every minute a potential insider risk goes undetected, the potential cost to your organization multiplies. Proactive detection isn't just about security; it's a direct investment in financial stability and resilience.
How Proactive Detection Minimizes Financial Loss
This is where Logical Commander’s real-time detection becomes a game-changer. Our AI-powered risk management platform is built to spot the subtle indicators of risk long before they blow up into a full-blown crisis, giving you the time to act fast and contain the financial exposure.
By shifting from a reactive, wait-and-see posture to a proactive one, you can neutralize threats before they become seven or eight-figure problems.
Instead of waiting for a breach and paying the price, a solution like E-Commander lets you manage risk intelligently. This transforms insider risk management from a cost center into a core financial strategy that delivers a measurable return. To dig deeper into these dynamics, learn about the true cost of reactive investigations and see how a proactive model protects your bottom line.
Building an Ethical and Compliant Program
Let's be clear: a truly effective insider risk management program isn't about buying a tool. It's about building a framework of trust, transparency, and technology. The goal is to protect your organization without making your employees feel like they’re constantly under a microscope.
This is where a privacy-first design isn’t just a feature—it's everything.
Logical Commander’s E-Commander platform was engineered from the ground up on this very principle. Our entire approach is non-intrusive and operates in full compliance with tough regulations like EPPA, GDPR, and CPRA. You won't find us using restricted terms or practices like "truth verification." Instead, our ethical AI is designed to identify patterns of "ethical consistency" and "integrity alignment," respecting human dignity while neutralizing threats.
Ultimately, you want a culture where security and employee trust aren't competing priorities. They should be two sides of the same coin, which all starts with a clear, well-defined strategy that gets everyone on the same page.
Establishing Your Governance Foundation
Before you even think about deploying technology, your first move is to build a cross-functional governance team. A successful program needs buy-in from multiple departments because each one brings a critical piece of the puzzle to the table.
Your team should include leaders from:
Human Resources: They provide essential context on employee lifecycle events and are the guardians of fairness.
Legal & Compliance: They ensure every policy and action stands up to regulatory scrutiny.
Security: They're on the front lines, managing technical controls and threat response.
IT: They handle the technical nuts and bolts of implementation and integration.
This kind of collaborative structure is your best defense against information silos. When a risk indicator is flagged, the response is coordinated, appropriate, and fully compliant—no guesswork involved. The team's first job? Define what a risk indicator actually looks like and create a playbook for responding.
To see how a strong framework for managing information security risks works in practice, understanding the principles of [ISO 27001 certification](https://visit-us.com/what-is-iso-27001-certification/) is a great place to start. It gives you a globally recognized standard for creating systematic, risk-based security controls.
Actionable Insights for a Stronger Program
Building an ethical program is about taking clear, proactive steps. Here are two actionable insights you can apply right away to strengthen your foundation:
Define Your "Crown Jewels" First: Before you do anything else, identify your most critical data and assets. When you focus protection on what truly matters, you can fine-tune your AI risk prioritization and avoid unnecessary monitoring. This reduces noise and reinforces the trust-based culture you're aiming for.
Communicate Transparently with Your Workforce: Be open about the purpose of your insider risk program. Frame it as a protective measure for both the company and its people. Emphasize that the focus is on risky behaviors involving critical data, not on watching personal activities.
By putting these strategies into action with a solution like Logical Commander, you’re not just building a compliant program. You’re fostering a culture of integrity and resilience from the inside out.
Ready to see how our platform empowers cross-departmental collaboration? Request a demo to see our ethical AI in action.
Your Path to Proactive Risk Management
The writing is on the wall: insider incidents are getting more complex and more expensive by the day. The old security playbooks just can't keep up. Relying on reactive tools that flood your team with noise while missing the real threats is a recipe for disaster—financially and reputationally. The only sustainable path forward is a modern, ethical, and intelligent approach to insider risk management.
This is exactly where Logical Commander comes in. Our ethical & non-intrusive AI gives you the real-time detection needed to get ahead of risks before they escalate. It all happens within a privacy-first architecture that is fully EPPA-compliant and ISO 27K certified. We're built for cross-department collaboration, giving HR, security, and compliance teams a single source of truth to protect your organization.
Ready to stop chasing threats and start preventing them? [Request a demo](https://www.logicalcommander.com/book-a-demo) of our E-Commander platform today and see what our ethical AI can do for your organization.
Know First. Act Fast. Ethical AI for Integrity, Compliance, and Human Dignity.
%20(2)_edited.png)
