Your Guide to Fraud Risk Assessment
- Marketing Team
- Nov 27, 2025
- 16 min read
Updated: Dec 1, 2025
A fraud risk assessment is the process your organization uses to systematically identify, analyze, and mitigate potential fraud threats before they turn into costly disasters. Think of it as drawing up the architectural blueprint for your company's security—it’s designed to find every hidden vulnerability and weak point that could be exploited by fraudsters, both inside and out.
Why a Fraud Risk Assessment Is a Business Imperative

Viewing a fraud risk assessment as just another compliance checkbox is a huge mistake. It’s actually a core business process that builds resilience, protects your assets, and defends your company’s reputation. Ignoring it is like building a fortress but never checking the walls for cracks. Sooner or later, an attacker will find a way in.
And make no mistake, the threats aren't just hypothetical—they are constant, sophisticated, and always evolving.
Modern fraud schemes have moved far beyond simple scams. Today’s threats are complex, blending sophisticated tech with clever social engineering. From payment diversion fraud to synthetic identity schemes, the methods used to steal money and data are in a constant state of flux. A proactive assessment framework is what moves your organization from a reactive, damage-control posture to one of smart, strategic prevention.
The Proactive Advantage in a High-Threat Environment
Waiting for a fraud incident to happen before you act is an incredibly expensive gamble. The damage goes way beyond the initial financial loss. You’re also looking at regulatory fines, steep legal fees, major operational disruption, and a serious hit to customer trust that can take years to rebuild.
A formal fraud risk assessment gives you a structured way to get ahead of these threats.
It forces you to map out your specific vulnerabilities, whether they’re hiding in procurement, payroll, or your customer payment systems. This clarity is everything. Instead of wasting money on generic, one-size-fits-all security, you can focus your strongest defenses on the areas of highest risk. It’s the smartest way to get a real return on your security investment.
The numbers don't lie. A staggering 79% of organizations reported being targeted by payment fraud attacks, showing just how widespread this threat is. But here's the key takeaway: organizations with a robust fraud risk assessment program in place saw a 30% lower rate of successful fraud attempts than those without one. You can read the full research about these payments fraud findings to see just how powerful a proactive stance can be.
Core Objectives of Your Assessment
A real fraud risk assessment is much more than a simple audit; it’s a strategic initiative with clear business goals. By systematically evaluating your defenses, you're not just looking for problems—you're working toward key outcomes that make the entire organization stronger.
The table below breaks down the primary goals that an effective fraud risk assessment program is designed to achieve.
Core Objectives of a Fraud Risk Assessment
Objective | Description | Business Impact |
|---|---|---|
Identify Vulnerabilities | Pinpointing the specific processes, systems, and roles most susceptible to fraudulent activity. | Reveals hidden weak spots before they can be exploited, reducing the likelihood of a successful attack. |
Evaluate Existing Controls | Honestly assessing the effectiveness of current safeguards and identifying any critical gaps. | Ensures your security investments are actually working and prevents a false sense of security. |
Prioritize Risks | Focusing time, budget, and talent on mitigating the threats that pose the greatest potential harm. | Maximizes the ROI of your security efforts by directing resources where they are needed most. |
Foster a Culture of Integrity | Raising fraud awareness across the organization and empowering every employee to be part of the defense system. | Turns your entire workforce into a human firewall, making the organization more resilient from the inside out. |
Ultimately, these objectives work together to transform fraud prevention from a reactive, check-the-box exercise into a dynamic and proactive strategy that protects your bottom line and your brand.
The Four Pillars of an Effective Assessment Framework
Breaking down a fraud risk assessment isn't as complicated as it sounds. When you clear away the jargon, you're left with a straightforward, four-pillar framework that turns a daunting task into a manageable strategy.
Think of it like a doctor's approach to patient care. You can't just jump to treatment without a proper diagnosis. Each pillar represents a critical stage, moving logically from identifying the problem to performing ongoing wellness checks. This structured approach ensures you don't miss anything and that your efforts are focused where they matter most. The four pillars are Identification, Analysis, Response, and Monitoring. Master each one, and you’ll build a resilient defense against fraud.
Pillar 1: Identification — The Diagnostic Phase
The first pillar, Identification, is all about discovery. This is your diagnostic phase, where you actively search for potential fraud schemes and the vulnerabilities that enable them. Simply put, you can't protect your business from a threat you don't even know exists. This step involves creating a complete inventory of all historical, current, and potential future fraud scenarios that could hit your organization.
This isn't a job for one department working in a silo. It has to be a comprehensive effort, pulling in insights from across the business. This typically includes:
Brainstorming Sessions: Get cross-functional teams in a room—finance, HR, operations, legal—to map out potential schemes from every angle.
Reviewing Historical Data: Dig into past fraud incidents, near-misses, and audit findings. Look for the recurring patterns.
Surveying Staff: Talk to the people on the front lines. Employees who work directly with fraud controls and vulnerable processes have invaluable insights.
The goal is to create an exhaustive "risk register," a complete list of potential threats, from bid rigging in procurement to classic expense reimbursement fraud. This register becomes the foundation for the entire assessment.
Pillar 2: Analysis — Assessing the Severity
Once you know what could go wrong, the next step is Analysis. This is where you figure out how bad each of those risks really is. Just as a doctor has to determine if a condition is a minor issue or a life-threatening emergency, you need to evaluate the likelihood and potential impact of each fraud scheme.
This pillar moves you from a simple laundry list of what could happen to a prioritized map of what is most likely to cause serious harm. It’s a two-part evaluation for every risk you’ve identified:
Likelihood: How probable is it that this specific fraud will actually happen?
Impact: If it does happen, what’s the damage? Think financial, reputational, and operational fallout.
A common and incredibly effective tool for this is the risk prioritization matrix. It’s a simple visual grid that helps you plot each risk based on its likelihood and impact scores. This makes it instantly clear which threats demand your immediate attention and which can simply be monitored.
This analytical step ensures your limited resources are aimed at your most critical vulnerabilities, instead of treating every potential threat as an equal five-alarm fire.
Pillar 3: Response — The Treatment Plan
With a clear picture of your highest-priority risks, you can move to the Response pillar. This is your treatment plan. Here, you design, implement, or strengthen the controls needed to neutralize the threats you’ve identified. The entire point is to reduce the residual risk—the danger that remains after your controls are in place—to a level your organization is comfortable with.
Your response strategies generally fall into three buckets:
Prevention: These are controls designed to stop fraud before it ever happens. Think mandatory approvals for large payments or proper segregation of duties.
Detection: These controls are built to catch fraud quickly if it does occur, like running exception reports or conducting regular account reconciliations.
Response: These are the actions you take after fraud is detected to stop the bleeding and prevent it from happening again, such as launching an investigation or blocking accounts.
Crucially, every single control should be directly mapped back to a specific risk you identified earlier. This ensures every defensive measure has a clear and defined purpose.
Pillar 4: Monitoring — Ongoing Health Checks
Finally, the Monitoring pillar ensures your fraud risk assessment isn’t a one-and-done project. It has to be a living, breathing process. Fraudsters are always changing their tactics, and your own business environment is constantly evolving. Ongoing monitoring acts as a continuous health check for your entire anti-fraud framework.
This final pillar is all about vigilance and adaptation. It involves:
Regular Reviews: Periodically reassess your risk landscape, especially after big changes like launching a new product, entering a new market, or a major system upgrade.
Control Testing: You have to "pressure test" your key controls to make sure they’re still working as intended. Don't just assume they are.
Dashboarding: Use real-time data to track key risk indicators (KRIs) and monitor how effective your mitigation efforts are.
A strong monitoring program keeps your defenses sharp and relevant. It transforms your fraud risk assessment from a static report that gathers dust into a dynamic, sustainable part of your organization's governance.
Your Step-by-Step Guide to Conducting an Assessment
Alright, let’s move from theory to action. Knowing the framework is one thing, but actually rolling up your sleeves and conducting a fraud risk assessment is where the real work begins. This isn’t a passive, box-ticking exercise; it’s an active, structured investigation into where your organization is most vulnerable. A successful assessment is methodical, leaving no stone unturned.
Think of this as assembling and deploying a special operations team. You need the right people with different skill sets, a clear map of the terrain, an honest look at your defenses, and a precise plan of attack. Each step builds on the last, creating a comprehensive and defensible report that drives real change.
This flow chart shows how each stage—Identification, Analysis, Response, and Monitoring—connects to create a continuous cycle of improvement, not just a one-off project.
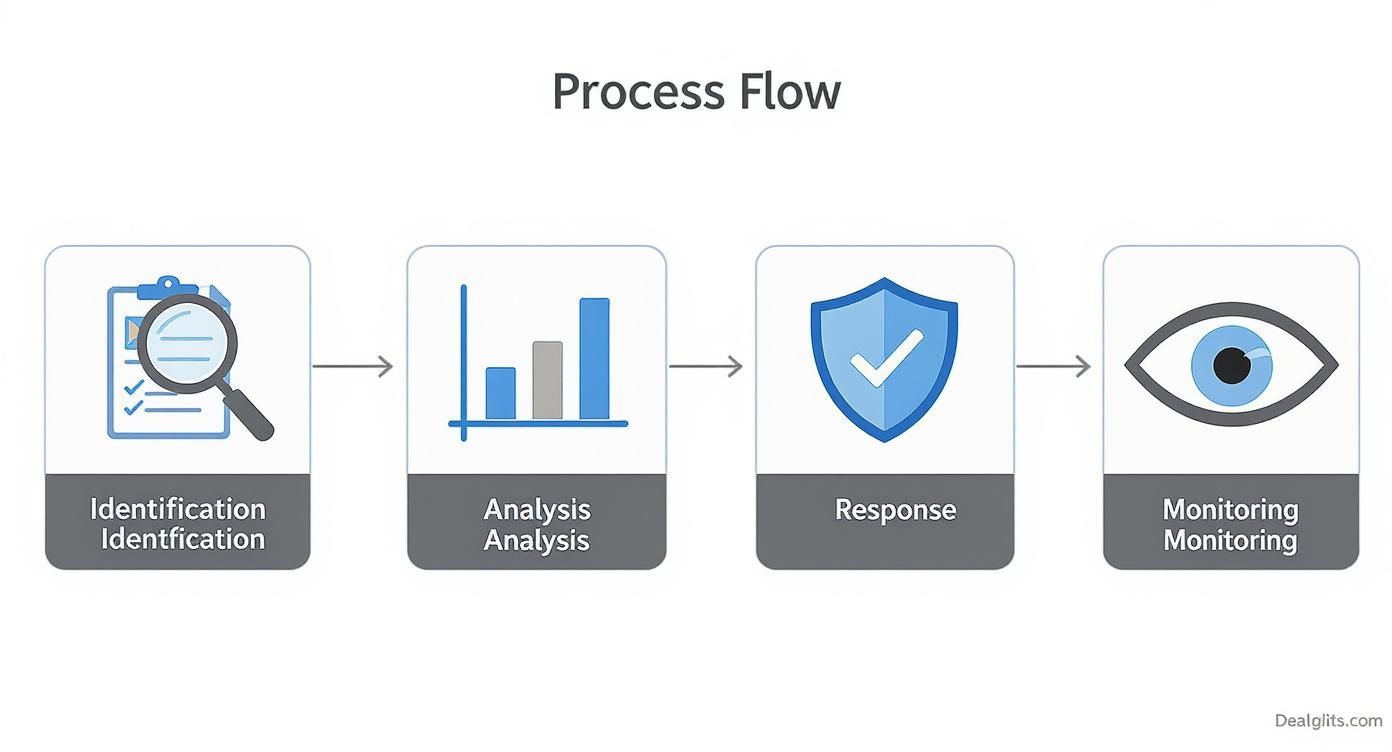
As the visual makes clear, a fraud risk assessment isn't a linear project with a neat finish line. It's a dynamic loop that has to adapt as new threats emerge.
Step 1: Assemble a Cross-Functional Team
Your assessment is only as strong as the people conducting it. A classic mistake is to hand this task off solely to the finance or internal audit departments. While their expertise is non-negotiable, a siloed approach guarantees you’ll miss critical risks that are only visible from other parts of the business.
Your mission here is to build a cross-functional team that brings diverse perspectives to the table. This should absolutely include people from:
Finance and Accounting: They live and breathe the flow of money and financial controls.
Operations: They know the day-to-day processes inside and out—where the real work (and potential fraud) happens.
Human Resources: They’re on the front lines of employee-related risks, from payroll to expense claims.
Legal and Compliance: They provide the essential regulatory and governance guardrails.
IT and Security: They understand the system vulnerabilities and data protection weak points.
This blend of expertise ensures a 360-degree view of fraud risk, covering everything from procurement schemes to sophisticated data breaches.
Step 2: Identify Inherent Fraud Risks
With your team assembled, the next task is to identify inherent risks. This is a creative brainstorming phase where you map out all the fraud schemes that could hit your organization if you had zero controls in place. You’re essentially thinking like a fraudster.
Start by looking at the most vulnerable departments and processes. Common hotspots include procurement (bid rigging, phantom vendors), accounts payable (invoice fraud, duplicate payments), payroll (ghost employees), and expense reporting (inflated claims). Your team’s job is to document every plausible scenario in a central "risk register."
Key Takeaway: A fraud risk assessment isn't about finding blame; it's about finding vulnerabilities. You must foster an environment of open and honest discussion where team members feel safe to point out potential weaknesses without fear of reprisal. This psychological safety is the secret sauce for an effective assessment.
Step 3: Assess Your Existing Controls
No organization operates in a vacuum with zero controls. The next logical step is to take a hard, honest look at the effectiveness of the safeguards you already have in place. This is where you map your existing controls directly to the inherent risks you just identified.
For each risk you’ve logged, ask these simple but powerful questions:
What controls are supposed to prevent or detect this fraud? (e.g., mandatory two-person approval for payments over $5,000)
How well are these controls actually working? (Are they followed religiously, or are they frequently ignored or overridden?)
Where are the gaps? (Which risks are flying under the radar with weak or nonexistent controls?)
This gap analysis is one of the most valuable outputs of the entire assessment process. It's where the rubber meets the road.
Step 4: Score and Prioritize Risks
Let's be real: not all risks are created equal. You have to prioritize them to focus your limited time and resources where they’ll have the biggest impact. The best way to do this is by scoring each risk based on its likelihood (how probable it is) and its impact (the potential financial and reputational damage if it happens).
A simple 1-to-5 scale for both factors works great. You can then plot each risk on a matrix, which immediately gives you a visual map of your high-priority threats—the ones sitting in that scary high-likelihood, high-impact quadrant. These are the risks that demand an immediate and robust response plan. For a deeper dive, check out this expert guide on how to conduct a risk assessment, which offers a detailed methodology that works across various risk types.
Step 5: Document and Report Your Findings
Finally, you need to pull all this hard work into a clear, compelling report for leadership. This document is your primary tool for securing the buy-in and resources you need for mitigation. The report should summarize the process, present the prioritized risk matrix, and—most importantly—provide specific, data-backed recommendations.
This step is especially critical for tackling emerging threats. For instance, synthetic identity fraud now accounts for about 20% of all fraud cases, with global losses soaring past $2 billion. Organizations that perform comprehensive assessments and continuously monitor their controls have been shown to cut these types of incidents by up to 40%. Your report must translate your findings into an undeniable business case for action.
How to Spot Common Fraud Red Flags and Data Sources

An effective fraud risk assessment comes down to one crucial skill: knowing what you’re looking for. Abstract risks become very real threats once you can connect them to the concrete warning signs—the "red flags"—that pop up in day-to-day operations. These indicators are the smoke that signals a potential fire, giving you a chance to investigate before a crisis erupts.
Think of it like being a detective piecing together a case. You need to gather clues from different sources to see the full picture. A red flag isn't definitive proof of wrongdoing, but it’s a strong signal that a process, transaction, or individual needs a closer look.
Ignoring them is like hearing a weird noise in your car's engine and just turning up the radio. Eventually, you’re going to break down. These warning signs typically fall into three distinct categories, each telling a different part of the story.
Behavioral Red Flags
This category is all about the human element, because fraud is ultimately committed by people. Sudden, unexplained changes in an employee's lifestyle or on-the-job behavior can be powerful indicators of underlying pressure or illicit gains. These signs are often the most visible to colleagues and managers.
Key behavioral flags include:
Living Beyond Means: An employee suddenly showing up with luxury cars, talking about expensive vacations, or wearing designer goods that just don't square with their known salary.
Unusual Work Habits: An individual who insists on working odd hours, never takes a vacation, or gets overly protective of their tasks, refusing to let anyone else help. This is often an attempt to conceal fraudulent activities that would be discovered in their absence.
Overly Close Relationships with Vendors: An employee who develops an unusually close—and often inappropriate—friendship with a particular supplier or contractor.
These human signals are frequently the earliest warnings you’ll get. For a deeper look into this area, you can learn more about how behavioral risk analytics provides crucial insights into your organization's human capital risks.
Transactional Red Flags
While behavior provides the context, the data tells the real story. Transactional red flags are the anomalies and suspicious patterns buried within your financial and operational data. These are the hard numbers and records that point directly to potential manipulation or theft.
Common transactional indicators are:
A sudden, unexplained spike in payments to a new or unfamiliar vendor.
Invoices that consistently fall just below the dollar threshold that requires additional approval.
Duplicate payments made for the same invoice or service.
Payments to vendors with only a P.O. box for an address or with names suspiciously similar to an employee's.
These flags are often hidden in massive amounts of data, which is why automated analysis and exception reporting are so vital for any modern fraud risk assessment.
Systemic Red Flags
Systemic red flags point to weaknesses in your organization's internal controls. These aren't just isolated incidents; they're signs that your foundational safeguards are being bypassed, ignored, or are simply not good enough. They reveal a cultural or process-based vulnerability that fraudsters can easily exploit.
A key systemic red flag is the frequent or undocumented overriding of internal controls by management. When exceptions become the rule, it creates fertile ground for misconduct and sends a message that established procedures are optional.
Other systemic issues to watch for include a lack of segregation of duties, a poor "tone at the top" regarding ethics, and a history of not acting on audit findings. These issues signal that your defenses are weaker than they appear on paper. Identifying these systemic gaps is fundamental to building a resilient anti-fraud program.
Using Technology and AI for Advanced Fraud Detection
Let's be honest: manual spot-checks and yearly audits just can't keep up with modern fraud. Relying on them is like trying to stop a flood with a bucket. Technology flips the script entirely, transforming fraud risk assessment from a static, backward-looking exercise into a dynamic, always-on defense. By bringing in data analytics and artificial intelligence, your organization can finally stop reacting to incidents and start proactively shutting down threats in real time.
This isn't about replacing your experts with robots. It's about augmenting them. Think of a human analyst as a security guard who can only watch one camera feed at a time. AI is the system that monitors every single camera simultaneously, instantly flagging the most suspicious activities for the guard to investigate. This frees up your compliance and audit teams to act as strategic investigators, focusing their invaluable skills on the highest-risk threats instead of drowning in routine data analysis.
The Power of Machine Learning in Fraud Detection
At its core, machine learning is incredibly good at finding the needle in a haystack. AI algorithms can sift through millions of transactions in seconds, uncovering subtle, complex patterns of fraudulent behavior that are virtually invisible to the human eye. This capability massively improves detection accuracy and cuts down on the noise of false positives that plague older, rule-based systems.
A huge part of this is the use of predictive analytics in banking for fraud detection, which allows institutions to anticipate and block fraudulent activities before they cause any financial damage. These systems learn from historical data to build a rock-solid understanding of what "normal" looks like, making it much easier to spot any deviation that signals potential fraud. If you want to go deeper, our guide on machine learning for fraud detection offers a more detailed look.
The industry's confidence in this approach is overwhelming. A staggering 93% of financial institutions believe that AI is the future of fraud detection. More importantly, organizations already using AI in their fraud risk assessments have seen a 25% decrease in fraud losses compared to those stuck with traditional methods.
From Manual Reviews to Continuous Monitoring
The most significant advantage of using technology is the shift from periodic check-ins to continuous, 24/7 monitoring. Instead of reviewing risks quarterly or annually, AI-powered systems provide a constant stream of intelligence, enabling an immediate and decisive response.
An AI-powered fraud risk assessment operates like a home's smoke detector—it’s always on, silently monitoring for the earliest signs of trouble. This stands in stark contrast to a manual audit, which is like checking for fire damage only once a year. The former prevents disaster; the latter merely documents it.
This always-on approach ensures your defenses adapt as fraudsters change their tactics. It provides a level of vigilance and scalability that no manual process could ever hope to match.
Traditional vs. AI-Powered Fraud Assessment
The differences between the old and new ways of tackling fraud risk are stark. Looking at them side-by-side makes it clear why adopting modern tools is no longer an option but a necessity for building a truly resilient defense.
Feature | Traditional Assessment | AI-Powered Assessment |
|---|---|---|
Frequency | Periodic (Quarterly/Annually) | Continuous & Real-Time |
Data Scope | Sample-Based & Limited | Comprehensive & Full-Scope |
Detection Method | Known Rules & Manual Review | Anomaly & Pattern Detection |
Response Time | Reactive (Weeks/Months) | Proactive (Seconds/Minutes) |
Scalability | Low (Labor-Intensive) | High (Automated) |
False Positives | High | Significantly Reduced |
Ultimately, integrating AI into your fraud risk assessment framework isn't just an upgrade—it's a force multiplier. It equips your organization to see threats first and act fast in an increasingly complex world.
Building a Sustainable Anti-Fraud Culture
A fraud risk assessment is an incredibly powerful diagnostic tool, but its findings are only as valuable as the culture they exist in. Think of it this way: a blueprint for a fortress is useless if the builders don't believe in the design or know how to lay the stones properly.
To achieve lasting resilience, you must embed fraud awareness and ethical behavior deep into your corporate DNA. This turns a one-time project into a sustainable, living defense.
This final, crucial step is about moving beyond policies on paper to fostering an environment where integrity is the default setting. It requires a conscious, top-to-bottom commitment, making every employee an active participant in your anti-fraud efforts. The goal is to build a human firewall that is just as strong as your technical controls.
The Power of Tone at the Top
It all begins with leadership. A strong "tone at the top" is the non-negotiable foundation of any successful anti-fraud culture. When executives consistently and visibly champion ethical conduct, it sends an unmistakable message throughout the organization: integrity is not optional.
This means more than just sending out an annual email about the code of conduct. It involves leaders actively participating in fraud awareness training, talking openly about ethical challenges, and, most importantly, holding everyone—including senior management—accountable for their actions.
A culture of integrity doesn't happen by accident. It is the direct result of leaders who not only talk the talk but consistently walk the walk, making it clear that ethical shortcuts will never be tolerated, no matter the perceived business benefit.
When employees see this level of commitment from the top, they are far more likely to take fraud risks seriously and feel empowered to speak up when they see something wrong.
Empowering Employees as the First Line of Defense
Your employees are your greatest asset in the fight against fraud. They are on the front lines every single day and are often the first to notice the red flags that automated systems might miss. Empowering them requires a three-pronged approach.
Engaging Training: Move beyond dry, check-the-box compliance modules. Effective training uses real-world case studies and interactive scenarios relevant to employees' specific roles. It should teach them not just what fraud is, but how to spot it in their daily tasks.
Trusted Reporting Channels: Employees must have a safe, confidential way to report concerns without fear of retaliation. A well-publicized whistleblower policy and multiple reporting channels (like an anonymous hotline) are essential.
Clear Accountability: There must be a transparent process for investigating reported concerns and clear consequences for misconduct. When employees see that their reports lead to real action, it reinforces their trust in the system.
By investing in these areas, you transform your workforce from passive observers into an engaged and vigilant first line of defense. To explore this topic further, you can read our guide on how to boost integrity in a workplace to build a resilient ethical culture. This approach shifts the burden from a small compliance team to a collective organizational responsibility.
At Logical Commander Software Ltd., we believe that building a sustainable anti-fraud culture requires more than just policies; it needs an operational backbone. Our E-Commander platform helps organizations translate ethical principles into actionable, traceable workflows, enabling you to know first and act fast without compromising employee dignity or privacy. Learn how Logical Commander can help you build a culture of integrity from the ground up.
%20(2)_edited.png)
