How to choose your integrated risk management solution
- Marketing Team

- 2 hours ago
- 17 min read
Trying to manage risk with each department in isolation is like trying to assemble a jigsaw puzzle with half the pieces missing. This outdated and disconnected approach creates dangerous blind spots, leaving the entire organization vulnerable to threats lurking in plain sight. An integrated risk management solution isn't a luxury; it's the strategic necessity that finally unites these teams in a proactive and cohesive defense.
Why disconnected risk management is hurting your business

Imagine this: Your security team detects a potential data exfiltration risk. At the same time, HR is dealing with an unconnected employee who has access to that same data. Meanwhile, your compliance team is preparing for an audit, completely unaware that these two unrelated events have just created a massive regulatory gap.
This isn't just a hypothesis. It's the everyday reality for countless companies. When risk management operates in isolation, each department only possesses a single piece of a much larger puzzle. It becomes nearly impossible to see the full picture of organizational risk, especially when it comes to insider threats.
The problem of departmental silos
A disconnected approach ensures that crucial information is lost in translation. HR, Compliance, and Security often operate with different vocabularies, metrics, and systems, creating communication barriers that slow down, or even halt, effective collaboration.
Without a common operating language, teams are forced to react individually to events instead of acting together based on shared information. This model is fundamentally reactive. By the time a risk reaches a sufficient magnitude to transcend departmental boundaries, the damage has usually already begun.
Understanding the true cost of reactive investigations shows how costly this outdated method is, not only in dollars, but in reputational damage and loss of trust.
The greatest vulnerability of any organization lies in the gap between its departments. When information does not flow freely, risks multiply in the shadows created by organizational divisions.
The strategic shift towards integration
An integrated risk management solution is much more than just software; it's a strategic framework designed to break down these internal barriers. It creates a single source of truth where data from different functions can finally connect, revealing risk patterns that would otherwise remain hidden.
This integration provides a unified 360-degree view, enabling your organization to:
Connect the dots: Link an HR performance signal with a security alert and a compliance issue to create a complete risk narrative.
Enable proactive intervention: identify early and subtle indicators of risk long before they become full-blown crises.
Ensure consistent governance: apply standardized policies and workflows across all departments, guaranteeing a fair and auditable process every time.
Ultimately, disconnected risk management is a relic of the past, struggling to keep pace with the complexity of modern business. The only way forward is a unified strategy that transforms scattered data into actionable, shared insights.
What is an integrated risk management solution?
To truly understand a comprehensive risk management solution , let's start with a common analogy. Imagine trying to keep a patient healthy with a team of top-tier specialists who never speak to each other. The cardiologist runs their tests, the neurologist keeps their own notes, and the general practitioner tries to guess how it all fits together. No one has the complete picture, so crucial connections between symptoms are consistently overlooked.
For years, this is exactly how most organizations have managed risk. The security team operates in one silo, HR in another, and compliance in a third, each with its own data, language, and priorities. An integrated risk management (IRM) solution is the central, collaborative medical team for the entire organization. Finally, it brings all the specialists together in the same room.
Create a single, shared patient file: a unified source of truthful information where every observation, test result, and treatment plan is visible to everyone. This type of platform centralizes risk information, standardizes workflows, and aligns governance across the organization. It transforms scattered and confusing data into a coherent and actionable health plan for the organization.
It's more than just a software tool
Don't mistake an IRM for just another software program; it's a fundamental shift in strategy. It's about changing your organization from a reactive and isolated approach to a proactive and unified one.
Instead of waiting for a serious problem to arise in a department, the system connects low-level signals from multiple sources. This allows emerging threats to be detected long before they can cause real damage.
This strategic approach is gaining significant momentum as companies realize its value. The global integrated risk management market is projected to grow from $16.36 billion in 2025 to $26.44 billion in 2030. This compound annual growth rate of 10.14% indicates a clear trend: organizations worldwide are adopting these platforms to manage complex compliance requirements and today's modern threats.
This shift focuses on creating a common operating language. When HR, security, and compliance teams work with the same strategy, the combined information becomes far more powerful than the sum of its individual components. To delve deeper into this concept, see our comprehensive guide on enterprise risk management in modern organizations .
From silos to synergy: the evolution of risk management
The difference between a traditional, disjointed approach and a modern, integrated one is vast. Understanding this evolution helps to grasp the unique value that an MRI solution offers. It's the difference between being reactive and fragmented, versus being proactive and unified.
This table contrasts the outdated and compartmentalized approach to risk management with the modern and integrated framework being adopted by leading organizations.
Feature | Traditional (siloed) approach | Integrated Risk Management (IRM) Approach |
|---|---|---|
Data visibility | Information gets trapped within departments, creating blind spots. | A centralized platform provides a 360-degree view of risk across the entire organization. |
Collaboration | Teams work independently, often with competing priorities and metrics. | Cross-functional workflows and shared data foster seamless collaboration. |
Response model | Fundamentally reactive, addressing problems only after they occur. | Proactive, using predictive knowledge to identify and mitigate risks early. |
Governance | Policies and procedures are applied inconsistently across different teams. | A unified governance framework ensures consistent, fair, and auditable processes. |
This table highlights a crucial transition. Adopting a Global Risk Management (GRI) framework involves removing obstacles that prevent effective risk mitigation and building bridges that facilitate shared intelligence and collective action. It is the architectural blueprint for organizational resilience.
The main capabilities of a modern MRI platform
A truly integrated risk management solution goes far beyond simply collecting data; it integrates that information into a coherent and actionable defense strategy. To achieve this, modern platforms rely on five critical capabilities. Think of them less as checklist features and more as the functional pillars that enable your organization to see, understand, and act on risk in a unified way.
This concept map shows how centralized intelligence, automated workflows, and consistent governance combine to form the basis of an effective MRI system.
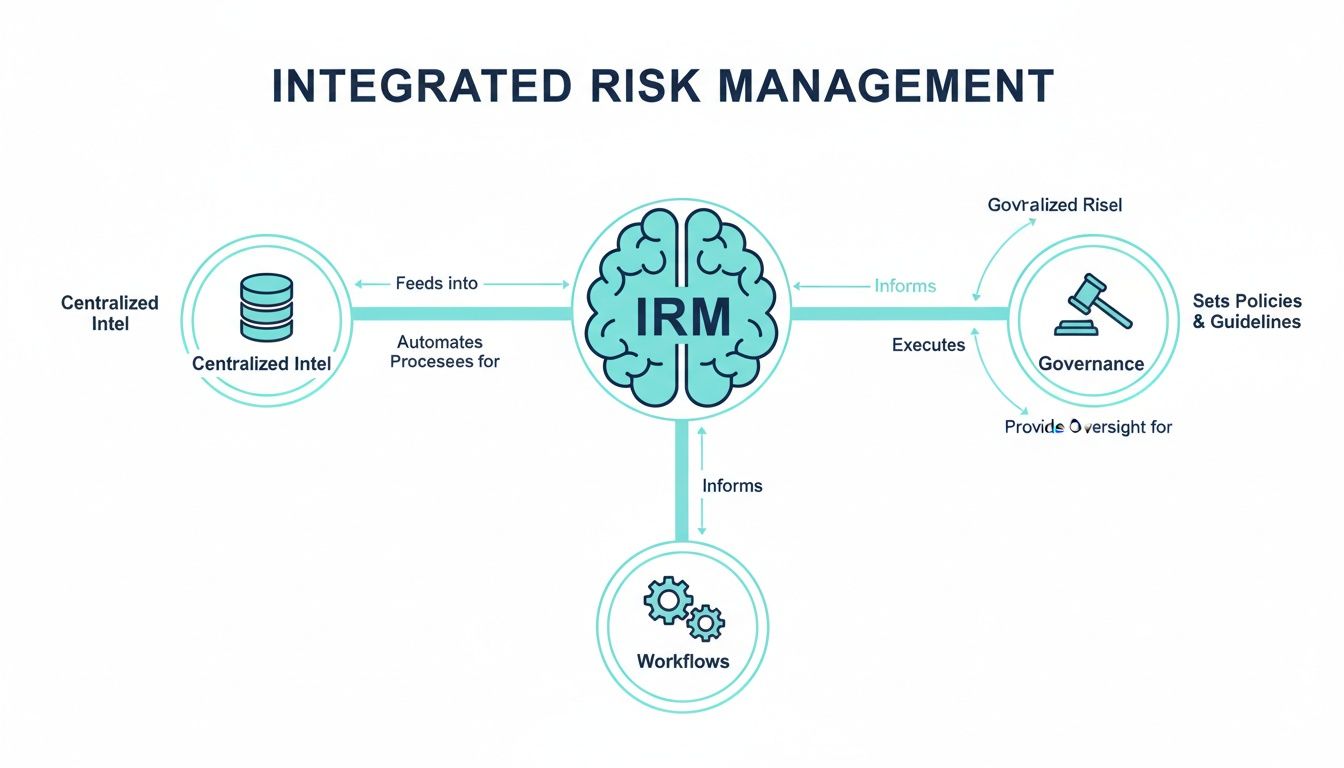
As you can see, a true MRI platform is not just a database. It is an active system where intelligence drives action, all under a single set of rules.
Unification of risk aggregation
The first pillar is risk aggregation . This is simply the ability to bring together disparate data from different departments (HR, Security, Compliance) into a centralized view. Without this, you operate with enormous blind spots.
Imagine a security system alerting an employee for downloading an unusually large file. On its own, this might be a minor issue, even a mistake. But an IRM platform connects that alert with an HR alert about recent performance issues and a compliance note about that same employee accessing sensitive customer data.
Suddenly, three isolated, low-level signals combine to reveal a significant internal risk that no single department could have detected on its own. This holistic view is the first step toward anticipating problems rather than simply fixing them.
Automation of optimized workflows
Once a risk is identified, the platform should automate the response. Streamlined workflows ensure that the right information reaches the right people at the right time, always following a predefined process and complying with regulations.
For example, when an HR concern is logged in the system, a workflow can automatically trigger a security review and notify the compliance team. This creates a seamless, integrated process where every action is tracked.
This level of automation eliminates the manual transfers, messy email chains, and lost information that plague traditional investigations. It ensures that every case is handled consistently, minimizing human error and guaranteeing procedural fairness.
The true power of a platform lies not only in what it sees, but in what it does with that information. Automated workflows transform passive data into an active and intelligent response mechanism that protects the organization.
Enabling predictive analytics
Modern investment risk management (IRM) platforms use analytics to move from reacting to past events to anticipating future ones. This is where predictive analytics comes in, identifying patterns and correlations in historical data to predict potential risks before they materialize.
By analyzing thousands of data points, the system can detect the subtle combinations of events that often precede misconduct or policy violations. It's not about profiling individuals, but about recognizing high-risk situations .
This provides leaders with a powerful prevention tool. It allows them to allocate resources to emerging areas of concern, strengthen controls, and provide targeted training to proactively mitigate threats.
Generating auditable evidence
In today's regulatory world, being able to demonstrate that the right thing was done is non-negotiable. A fundamental function of any integrated risk management solution is to create a complete and tamper-proof record of every action taken.
This auditable evidence record documents who did what, when, and why. From the initial signal to the final resolution, every step is recorded, providing a clear and defensible record for auditors or legal review.
This completely eliminates the burden of manually compiling reports from spreadsheets and emails. It provides compliance officers with a single source of truthful information, demonstrating that the organization followed its own policies and acted in good faith. You can explore more about how this integrates with broader strategies in our roundup of the best governance, risk, and compliance software .
Centralization of governance
Finally, the entire system must operate under a centralized governance framework. This means that the platform is configured to apply your organization's specific policies, procedures, and ethical standards consistently across all areas.
Ensure that risk is defined, assessed, and managed in the same way across all departments, from sales to operations. This consistency is essential for building a fair and transparent culture where employees truly trust the process.
Centralized governance assures leaders that the organization operates within its established risk tolerance and complies with all its legal and ethical obligations. It transforms risk management from a disconnected set of activities into a strategic, company-wide discipline.
Navigating regulations, privacy, and ethics in risk management
An effective, comprehensive risk management solution cannot operate in isolation. It must exist within a complex and uncompromising world of laws, privacy rights, and ethical principles. It is best to view these constraints not as barriers, but as essential safeguards that keep the platform on track, ensuring it builds trust rather than eroding it.
Modern regulations, such as Europe's General Data Protection Regulation (GDPR) and California's Consumer Privacy Act (CCPA), are not mere suggestions. They are strict legal mandates that fundamentally define how risk management technology operates, establishing clear boundaries on what organizations can and cannot do with their employees' data.
This legal framework is the foundation of any ethical system. For a risk management platform to comply with the standards, it must be designed from the ground up with these standards in mind, making privacy a fundamental element, not an afterthought.
What a compatible MRI platform cannot do
To understand what an ethical integrated risk management solution is , it's helpful to first define what it isn't . Regulatory and ethical boundaries are very clear on several points, and systems that comply with regulations are expressly prohibited from crossing them. A system based on integrity will never engage in practices that violate the dignity or legal rights of employees.
These prohibitions include:
Prohibition of psychological profiling: The system cannot and should not attempt to analyze an employee's personality, emotions, or psychological state. This is not only unethical, but also highly unreliable and legally indefensible.
Non-invasive surveillance: Covert or continuous monitoring of employee communications or activities constitutes a direct violation of the right to privacy. An ethical platform uses structured and consented data, not surveillance.
No AI-based judgments: A machine cannot determine guilt or innocence. The platform's role is to present objective indicators to human decision-makers, never to make accusations or draw conclusions on its own.
Without lie detection logic: any technology that claims to detect deception through algorithms is considered pseudoscience and is strictly prohibited by regulations such as the Employee Polygraph Protection Act (EPPA).
These limits are non-negotiable. They ensure that technology serves as a decision-support tool for human experts, not as an automated judge that circumvents due process.
The power of being ethical by design
An integrated risk management solution, ethical by design, considers regulatory compliance a strategic asset. Instead of collecting vast amounts of unstructured data in the hope of finding a problem, this approach focuses on identifying specific, predefined risk indicators. It's the difference between installing cameras in every room and having a smoke detector. One is invasive and presupposes irregularities; the other is a targeted, ethical tool that alerts you to a specific hazard.
An ethical internal risk management (IRM) system is based on a simple yet effective principle: it provides objective signals, not subjective judgments. Its purpose is to identify potential risks based on verifiable data, empowering human leaders to make informed, fair, and consistent decisions.
This indicator-based approach respects employee dignity by separating data from the individual's identity. It reports on an event, such as a policy violation or conflict of interest, without presuming intent. Navigating the complex landscape of regulations, privacy, and ethics also involves having robust privacy policies to transparently communicate how data is managed.
Ultimately, a platform based on regulatory compliance and ethical principles not only mitigates risk, but also strengthens organizational culture from within, fostering an environment of fairness and transparency. When employees know the process is objective and respectful, they are much more likely to trust leadership and actively participate in building a safe and ethical work environment. This trust is an invaluable asset that a purely technical solution can never generate.
How to choose the right integrated risk management solution
Analyzing marketing to find the right comprehensive risk management solution can seem like an impossible task. Every provider promises a miracle cure, but the reality is that a poor choice can create more risks than it solves.
This guide eliminates the confusion. It's a simple framework for HR, Compliance, and Security leaders to ask the tough questions: the ones that truly reveal whether a platform is a strategic asset or simply an obsolete product.
We'll review how to evaluate everything from privacy safeguards and governance alignment to the scope of implementation and the all-important ROI.
Assessment questions that get straight to the point
When you're sitting across from a vendor, you need to go beyond the sales pitch and get to the heart of what their platform actually does.
Here are the questions that will help you do it in just a few minutes:
How does the platform specifically defend and demonstrate employee privacy rights?
Can it be adapted to our organization's specific governance policies immediately, without a massive coding project?
Is there a truly unified operational vision for Human Resources, Compliance, and Security, or is it simply a matter of integrated dashboards?
How flexible is the workflow engine for managing cross-departmental processes? Can we see a live demonstration?
What specific analytical and reporting metrics are used to drive early risk detection?
What are the provider's service level agreements (SLAs) and what is the actual support process like?
Is it possible to integrate the solution with our existing HRIS, GRC, and SIEM tools? We need proof.
What is the true total cost of ownership and what is the expected time to see genuine value?
These aren't just items on a checklist. They invite a conversation about whether a solution aligns with your organization's values and operational realities. Always insist on a proof of concept (POC) in a test environment to verify integration, performance, and user adoption.
Evaluate privacy, governance, and configurability
When evaluating a platform that handles employee data, privacy protection is non-negotiable . Period.
Request written case studies from providers that clearly demonstrate how they manage data minimization and consent frameworks. You need to see exactly how their audit logs record changes in consent over time and how that data supports a formal ethical and legal investigation.
Evaluate unified operational visibility
A "single pane of glass" is one of the most overused phrases in technology, but the concept is crucial. A true unified view avoids the dangerous blind spots that arise when an HR alert and a security alert about the same employee reside in separate, completely disconnected systems.
Verify that the dashboards and APIs offer real-time data accessible to all stakeholders. Better yet, ask for a specific example of an incident where your platform's unified visibility directly prevented a compliance violation. If they can't provide one, that should tell you everything you need to know.
Giving meaning to implementation and ROI
A great platform is useless if its launch is a nightmare and you can't prove its value.
Plan a phased implementation. This limits disruptions and helps you build trust and achieve milestones throughout the process.
Budget the big picture. The selling price is just the beginning. You must factor in training, customization, and the overhead costs of running the system.
Measure success with real metrics. Focus on aspects such as reducing the time needed to detect an early sign of risk and reducing costs by preventing a serious incident.
Assigning expected benefits to specific KPIs is the only way to set realistic return on investment (ROI) expectations. Analyze the potential cost savings from fewer internal investigations, lower non-compliance fines, and even higher employee retention. Define your internal success metrics from day one and review them quarterly with all stakeholders.
Why E-Commander Aligns Ethics and Efficiency
E-Commander is designed to identify early signs of risk while firmly upholding employee dignity and compliance.
It provides ethical indicators, not accusations . It focuses on systemic risk patterns, not individual surveillance.
It is configured according to your policies without the need for a single line of code .
It reveals hidden patterns with AI-powered analysis bounded by clear and transparent rules .
Choosing E-Commander means partnering with someone as committed to ethical design as they are to operational clarity. Our PartnerLC program offers regional support, testing, and proven proofs of concept (POCs) for a wide range of industries.
Feature | Generic MRI tool | Electronic Commander |
|---|---|---|
Privacy by design | It varies depending on the supplier. | Integrated consent models |
Ethical indicators | Optional add-on | Main functionality |
Policy configurability | Limited, often requires code | Drag and drop rule generator |
Don't forget the stakeholder collaboration tools
How will your teams use this system on a daily basis? Evaluate the integrated messaging, task assignment, and alert routing to ensure teams stay coordinated during a changing situation. And most importantly, verify that role-based access controls are granular enough to protect privacy while still sharing critical information with those who need it.
Look for the supplier's reputation and support
Confirm that they have customer references in different industries and for various use cases.
Check their average support response times and what their escalation procedures are like.
Strong vendor support isn't just a nice-to-have; it dramatically reduces risk during onboarding and throughout the platform's lifecycle. A thorough assessment not only helps you find a standards-compliant IRM provider but also a long-term partner you can rely on. And in a world of risk, trust and transparency are everything.
Building an ethical and proactive internal defense

When managing internal risks, the stakes are high. We're talking about everything from fraud and data loss to serious breaches of workplace integrity. This is a sensitive and complex area where generic, one-size-fits-all platforms simply aren't enough. An integrated, targeted risk management solution must go beyond simply connecting data points; it must operate on the foundation of ethics and integrity.
The real challenge is to shift from a reactive approach—investigating only after harm has been done—to a proactive one that prevents incidents from happening in the first place. This requires a new way of thinking, moving away from surveillance and judgment toward a structured and ethical model of analysis.
This is where the idea of providing "ethical indicators, not accusations" becomes a strategic imperative. The goal is to separate objective data signals from subjective human judgment, creating a clear and fair process that preserves due process from beginning to end.
A common language for a united defense
Effective insider threat management is often hampered by organizational silos. HR, Compliance, and Security teams often speak different languages, use different tools, and operate under different mandates. This fragmentation creates dangerous blind spots where early warning signs are missed simply because no one has the complete picture.
An advanced integrated risk management solution eliminates these barriers by creating a common operating language. It establishes a unified framework that allows for real-time correlation of a concern reported by HR, a compliance policy alert, and a security data access alert.
This shared vocabulary and centralized view allow teams to collaborate effectively from a single source of information. Instead of searching for information across disconnected systems, stakeholders can see the full context of a potential risk as it unfolds, enabling a coordinated and timely response.
Ethical indicators, not accusations
The most profound change in this modern approach is the precise focus on objective indicators. A system designed for internal risk should never make judgments, draw conclusions, or attempt to determine intent. Its sole purpose is to identify predefined and structured signals that align with the organization's governance policies and standards.
Think of it like a smoke detector. It doesn't accuse anyone of starting a fire; it simply provides a clear and objective signal of the presence of smoke. That alert allows the fire department (the human experts) to investigate and make an informed decision. An ethical MRI platform operates on the same principle.
The system's function is to flag a potential discrepancy or concern based on verifiable data, not to label an individual. This crucial distinction ensures that technology enhances human governance rather than attempting to replace it.
This approach upholds employee dignity by focusing on events and patterns, not personalities. It provides leaders with the structured information needed to initiate a fair, consistent, and compliant due diligence process, ensuring that each situation is handled according to established due process.
The power of proactive prevention
Reacting to internal incidents is always more costly and damaging than preventing them. Investigations consume resources, erode morale, and can cause lasting damage to an organization's reputation. A proactive strategy based on early indicators radically changes this dynamic.
By identifying the subtle signs that often precede misconduct or policy violations, an integrated risk management solution enables organizations to intervene constructively.
This proactive stance can take many forms:
Specific training: identification of procedural vulnerabilities that can be addressed through specific education for employees.
Process improvement: detecting gaps in internal controls before they can be exploited.
Supportive intervention: Recognizing signs of employee pressure or disengagement that HR can address before they become risk events.
This shift from a punitive to a preventative mindset creates a healthier and more resilient organizational culture. It builds trust by demonstrating a commitment to fairness and support, showing that the goal is to protect both the institution and its staff. Ultimately, this dignified, responsible, and forward-thinking approach transforms risk management from a necessary cost factor into a strategic asset that strengthens the entire organization.
Your questions, answered
When evaluating a new way of managing risk, questions inevitably arise. Let's examine some of the most common questions raised by leaders trying to anticipate internal threats without creating a culture of distrust.
How disruptive is the implementation?
"How difficult is it to implement an integrated risk management solution?"
This isn't the tedious year-long review you might be imagining. With modern platforms, the process is surprisingly quick. Most organizations implement the first phase (addressing one or two priority risk areas) in under three months. A good vendor guides you through the entire setup process, so your teams can start seeing real value without putting a huge strain on internal resources.
In fact, 85% of organizations complete the first phase in less than 90 days, which drastically reduces the implementation risk.
Will this replace our people?
Will an integrated risk management solution replace our current staff?
Not at all. Think of it as a force multiplier for your experts, not a replacement. It's a strategic tool that handles the heavy lifting of gathering risk data and automating workflows. This frees your HR, Compliance, and Security teams from information hunting so they can focus on what they do best: strategic analysis, nuanced investigations, and making smart, informed decisions.
How do we measure ROI?
"What is the typical ROI of an integrated risk management solution?"
The return on investment is reflected in various ways. You'll see concrete figures in reduced losses from fraud, fewer fines for non-compliance, and much faster resolution of investigations. But the real value often lies in what it prevents . By detecting and neutralizing risks early, it avoids those catastrophic crises whose true costs—in reputation, trust, and morale—are almost impossible to calculate.
Research costs are typically reduced by 30% .
Consistent governance can reduce penalties for non-compliance by up to 20% .
How are privacy and ethics handled?
"How does an integrated risk management solution respect privacy and ethical constraints?"
This is the most important question, and the answer is simple: an ethical platform is built on respect. Modern enterprise risk management (IRM) solutions are designed to fully comply with stringent regulations such as GDPR, CCPA, and EPPA. They operate with indicator-based alerts, not with continuous, suspicious surveillance. This approach protects employee dignity and due process, which is the only way to build a culture of trust while simultaneously meeting legal obligations.
Consent models ensure that all data handling is aligned with employee permissions.
Auditable logs create a transparent record of every action performed within the system.
Ethical indicators point to potential risk events without making premature judgments about individuals.
Ready to protect your organization with an ethical, integrated risk management solution? Discover E-Commander from Logical Commander Software Ltd. at https://www.logicalcommander.com
%20(2)_edited.png)
