What Is Insider Threats: A Guide to Proactive Prevention
- Marketing Team

- 3 days ago
- 14 min read
An insider threat is a significant business liability originating from individuals with authorized access—such as employees, contractors, or partners—who misuse that access, whether intentionally or accidentally, to cause harm. It is critical to understand that this is a human-factor risk first and foremost, not merely a cybersecurity issue. The business impact cascades across financial stability, operational continuity, and your organization's regulatory standing.
Defining Insider Threats as a Human Factor Risk
Many organizations adopt a narrow, technical view when considering what is insider threats, focusing on network logs and data exfiltration reports. This approach is dangerously incomplete because it overlooks the root cause.
An insider threat is not fundamentally about technology; it's about the human behaviors, motivations, and errors that create vulnerabilities from within. This human element is precisely why traditional security tools, which are engineered to combat external attacks, consistently fail to prevent internal incidents. Treating an insider threat as just another cyber attack is a critical error. The risk is not a technical glitch; it's a business problem that starts and ends with people.
Shifting Focus from Technology to People
The entire conversation must shift—away from servers and firewalls and toward the human-factor risks within the organization. This liability extends far beyond a malicious employee intentionally stealing corporate secrets.
Internal threats also manifest through:
Negligent Employees: An individual who accidentally clicks a phishing link or misconfigures a cloud server, unintentionally exposing sensitive information.
Compromised Insiders: A person whose credentials are stolen by an external actor, turning a trusted account into a weapon without their knowledge.
Privileged Misuse: An administrator who uses their high-level access for unapproved purposes, even if their intent isn't explicitly malicious.
Understanding these distinctions is essential for building a prevention strategy that addresses the full spectrum of human-factor risk.
As the data shows, the source of these threats is varied, which highlights why a purely technical or surveillance-based approach is destined to fail. For a deeper analysis, you can explore our complete insider threats definition and its business implications.
The core challenge for leaders in Compliance, HR, and Security is not policing employee activity but understanding and mitigating human-factor risk before it manifests as a security incident. This requires a proactive, ethical, and non-intrusive strategy.
Ultimately, addressing what is insider threats effectively means moving beyond the costly and failed model of reactive investigations and intrusive surveillance. Legacy methods are not only often non-compliant with laws like the EPPA and damaging to morale, but they also fail because they act far too late.
The new standard of internal risk prevention, embodied by platforms like Logical Commander's E-Commander, focuses on early, ethical risk mitigation that respects employee dignity while protecting the organization from the inside out.
The Four Core Types of Insider Threats
To effectively manage internal risk, leaders must recognize the different scenarios they face. The motivation—or lack thereof—is key to building a robust and targeted prevention framework. Not all insider threats are the same, and a one-size-fits-all reactive approach is insufficient.
The table below breaks down the primary categories, helping decision-makers prepare for the diverse situations that create business liability.
Threat Type | Primary Motivation or Cause | Common Examples |
|---|---|---|
Malicious Insider | Intentional harm, financial gain, revenge, or ideology. | A disgruntled employee stealing intellectual property to sell to a competitor; a salesperson taking a client list before resigning. |
Negligent Insider | Unintentional error, carelessness, or lack of security awareness. | An employee clicking a phishing email link; accidentally sending a sensitive file to the wrong person; misconfiguring a cloud database. |
Exploited Insider | An external actor gains control of a legitimate user's account. | An attacker stealing an employee's login credentials through malware or social engineering to access the network undetected. |
Privileged Misuse | Abusing authorized access for non-business or unapproved purposes. | A sysadmin snooping on executive emails out of curiosity; a finance manager looking up the salaries of their colleagues. |
Each of these types requires a different mitigation strategy, but they all reinforce a core business truth: the most significant risks often come from those already inside your perimeter.
The Escalating Business Impact of Insider Threats
Discussing insider threats is a direct conversation about business liability and survival. When an internal risk materializes, the damage is not an abstract concept—it directly impacts the balance sheet, shatters brand trust, and can create deep operational and legal cracks that take years to repair.
The financial fallout alone demands executive attention. The average cost of a single insider threat incident has now reached a staggering $15.4 million. This isn’t a minor issue; it's a deeply concerning trend that threatens enterprise stability. The total average annual cost has ballooned from $8.3 million in 2018 to $17.4 million today, a shocking 109.6% increase in just seven years. These are enterprise-level crises, not minor operational hiccups.
Financial Drain Beyond the Initial Incident
The initial price tag is just the beginning. The longer an incident festers undetected, the more the costs multiply. For example, incidents contained within 31 days cost an average of $10.6 million. But if that incident lingers for over 91 days? The cost skyrockets to $18.7 million.
This direct link between containment time and financial damage makes a powerful business case for proactive prevention. A reactive "wait-and-see" approach is no longer a viable strategy; it is a direct path to maximizing financial and reputational harm.
This infographic breaks down the common sources of these threats, showing how both malicious and unintentional actions contribute to these staggering costs.
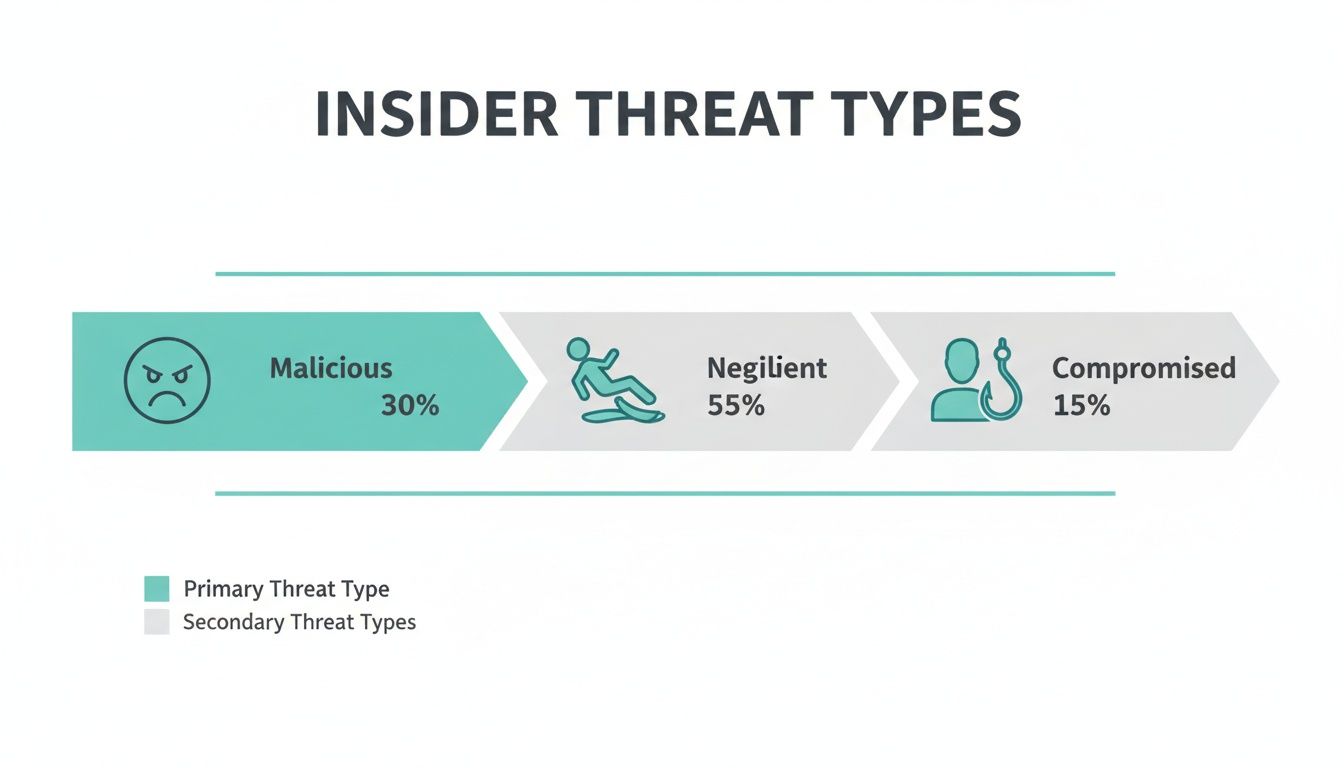
What's striking here is that while malicious insiders cause significant harm, simple negligence is far more common. This makes it crystal clear that any effective prevention strategy must address human error, not just malicious actors.
The true liability of an insider threat is rarely confined to a single department. It’s a cascading failure that strains resources across legal, HR, compliance, and security teams, often for months or even years.
The Hidden Costs That Cripple Organizations
Beyond the direct budgetary impact, insider threats inflict severe, lasting damage on an organization’s health and stability. These "hidden costs" represent the greatest danger.
Reputational Damage: In an era of instant information, a major internal breach can permanently tarnish a company's reputation, eroding customer trust and rattling shareholder confidence.
Regulatory Penalties: For companies in regulated industries like finance or healthcare, a single compliance failure can trigger massive fines, sanctions, and intense regulatory scrutiny that cripples business operations.
Employee Morale and Culture: A major incident, followed by a disruptive and often accusatory internal investigation, can poison a workplace culture. It breeds suspicion and distrust, wrecking productivity and driving away top talent.
Legal and Investigative Expenses: Responding to an incident is incredibly resource-intensive. You can learn more about the true cost of reactive investigations, which covers everything from legal fees and forensic analysis to the immense operational cost of diverting key personnel from their primary duties.
Ultimately, the growing impact of these threats forces a strategic choice: continue absorbing the escalating costs of reactive forensics and damage control, or invest in a proactive, ethical prevention framework that addresses human-factor risk before it becomes a multi-million-dollar crisis. The data makes the right path clear.
Why Traditional Detection Methods Are Failing Businesses
For years, organizations have attempted to solve the insider threat problem with a toolkit designed for external attacks. They have relied on reactive investigations and intrusive employee surveillance, only to find these methods are not just ineffective—they are often counterproductive. This legacy approach is fundamentally flawed because it treats a complex human-factor risk as a simple technical glitch, creating far more business liability than it solves.
The most common strategy, reactive forensic investigation, is a perfect example of a failed model. These investigations only begin after the damage is done—whether it's stolen intellectual property, a data breach, or a major compliance failure. By then, the financial and reputational harm is locked in, and the organization is left with the costly, disruptive job of cleanup.

The Pitfalls of Surveillance and Monitoring
In an attempt to get ahead of the problem, many businesses turned to employee surveillance and monitoring tools. While these might seem proactive, they create crippling drawbacks. They often operate on the edge of legal and ethical lines, putting companies at significant risk of violating privacy and labor laws like the Employee Polygraph Protection Act (EPPA).
Worse, these tools create a culture of distrust by treating every employee as a potential threat. Constant monitoring poisons morale, erodes psychological safety, and craters productivity. Instead of fostering a collaborative environment, it creates a "Big Brother" atmosphere that damages the employer-employee relationship. Furthermore, these systems are notoriously inefficient.
The fatal flaw of surveillance-based tools is their inability to distinguish between genuine risk and benign anomalies. They flood security and HR teams with countless false positives, burying them in alerts that waste time and obscure real threats.
This "alert fatigue" means that when a genuine risk signal appears, it is often lost in the noise. Teams become desensitized to warnings, and the organization remains just as vulnerable—now with the added burden of a complex and intrusive tech stack. For a more detailed look, our guide on modern insider threat detection tools explores why this shift in strategy is so necessary.
An Inherently Flawed Mindset
The core failure of traditional methods lies in their reactive mindset. They are built on a foundation of suspicion, designed to catch people doing wrong rather than preventing risk from emerging in the first place. This approach is misaligned with modern workplace values and is strategically ineffective against the diverse nature of what is insider threats.
Consider these limitations:
They Miss the "Why": Surveillance may show what an employee did but almost never reveals why. It cannot identify the underlying motivations or pressures that lead to risky behavior, which is critical for true prevention.
They Ignore Unintentional Threats: Tools designed for malicious activity are often completely blind to negligent behavior—which, as data shows, is the most common source of insider incidents.
They Create Legal Exposure: Deploying solutions that could be interpreted as coercive, like those resembling lie detectors or tools for interrogation, creates significant legal risk and regulatory exposure.
Ultimately, these outdated methods fail because they only address symptoms, not the cause. They focus on policing actions instead of understanding and mitigating the human-factor risks that drive them. This leaves organizations stuck in a costly cycle of reaction, cleanup, and distrust—a cycle that a modern, ethical, and proactive strategy is designed to break.
What’s Fueling the Alarming Rise in Insider Incidents?
The conversation around insider threats has shifted from a theoretical risk to an urgent operational reality. It’s no longer a question of if an organization will face an internal incident, but when. The data paints a clear picture for leaders in Compliance, HR, and Security—this is a rapidly accelerating business problem that legacy security models are failing to contain.
Recent findings show that insider incidents are not just more frequent; they have become a dominant cause of organizational data breaches. The scale of this problem is staggering, with incidents having jumped by 47% in just the last two years. This surge proves that internal, human-factor risk is growing faster than most companies can manage it.
The New Reality: A By-the-Numbers Look
The statistics reveal a landscape where internal threats are no longer a niche concern but a pervasive issue impacting the majority of businesses. The sheer prevalence of these incidents across companies of all sizes and industries is a call to action for decision-makers.
A staggering 56% of enterprises experienced at least one insider threat incident in the past year alone. This isn't just a big corporation problem; mid-sized companies with 500 to 2,500 employees have seen a dramatic 56% surge in these events. Most critically, insider threats now account for roughly 34% of all data breaches, a huge jump that underscores the growing role of internal actors. You can find more details in this in-depth insider threat pulse report.
This escalating frequency is made worse by a persistent detection problem.
The average time to identify and contain an insider threat incident still stands at a painful 77 days. This massive delay gives a bad actor a wide-open window to cause damage, from data theft and financial fraud to severe reputational harm.
Why This Is More Than Just a Security Problem
The growing volume and complexity of these threats are pushing traditional security frameworks to their breaking point. In fact, 68% of organizations now view insider threats as more challenging to detect and prevent than external attacks. This difficulty stems from a simple fact—insiders already have legitimate access, making their risky activities nearly impossible to distinguish from normal work using conventional, surveillance-based tools.
This challenge is especially vivid in sectors like healthcare, which has seen a 58% increase in insider-related incidents. Given the sensitivity of the data at stake, any internal breach in this sector is catastrophic.
The key takeaways from this data are clear:
Frequency is Accelerating: Organizations now report an average of 14.5 insider-related security incidents every year.
Detection is Delayed: The 77-day average containment time means most organizations are playing catch-up, discovering threats long after the real damage is done.
Complexity is Growing: The majority of security leaders agree that internal risks are now harder to manage than external ones.
These trends confirm that a reactive, forensic-based approach is no longer sustainable. Relying on investigations after the fact is a recipe for escalating costs and recurring damage. The only viable path forward is a strategic shift toward a dedicated, modern framework focused on proactive and ethical prevention.
A New Standard for Ethical and Proactive Prevention
The old model of launching a disruptive investigation after the damage is done is obsolete. A new standard is emerging, built on proactive, ethical prevention that safeguards your organization while respecting your employees. This isn't about treating your team as adversaries; it's about identifying and mitigating human-factor risk before it explodes into a crisis. This shift isn't just an ethical imperative—it's a business necessity for building a resilient, high-performing culture.
Logical Commander's E-Commander platform represents this new standard. It provides an ethical, EPPA-aligned, and non-intrusive alternative to outdated surveillance and reactive investigations, focusing on AI-driven preventive risk management.

From Surveillance to Strategic Insight
The core of this new standard is moving away from legally risky surveillance and toward AI-driven platforms that deliver actionable intelligence. Modern systems like E-Commander are designed from the ground up to be non-intrusive and fully compliant with regulations like the EPPA. They do not use surveillance, lie detection, or any form of invasive monitoring.
Instead, a solution like E-Commander analyzes behavioral risk signals within a completely ethical framework. It identifies patterns linked to potential misconduct, conflicts of interest, or compliance breaches. The goal isn't to police your staff but to give HR, Compliance, and Security the foresight they need to intervene constructively.
This method transforms risk management from a reactive, forensic exercise into a proactive, preventive function. It enables leaders to address potential issues early, often through support or policy clarification, rather than through punitive action after the fact.
This focus on ethical prevention is critical for maintaining trust. By ditching the "Big Brother" tactics that destroy morale, you create an environment where employees feel secure and valued—a powerful deterrent to insider risk. To learn more about this approach, explore our guide on ethical insider threat detection solutions.
How Non-Invasive AI Delivers Actionable Intelligence
So, how does this actually work? An ethical, AI-driven platform like E-Commander connects disparate data points to surface risk indicators that would otherwise go completely unnoticed. It all operates on principles that put privacy and dignity first.
No Surveillance: The system does not monitor emails, record conversations, or track personal activity. It is designed to be completely non-intrusive.
Focus on Behavior, Not Identity: The analysis centers on objective risk patterns, not on making assumptions about an individual's intent or character.
Actionable Alerts for Decision-Makers: Instead of a flood of false positives, the platform delivers high-fidelity alerts directly to the relevant departments (HR, Legal, etc.), empowering them to take measured and appropriate action.
Preserves Employee Dignity: The entire process is designed to be respectful and EPPA-aligned, ensuring that risk mitigation doesn't come at the cost of a healthy workplace culture.
Moving beyond traditional methods requires a new mindset and often, specialized guidance. When integrating new security frameworks, especially people-centric ones, choosing a reliable cyber security firm can provide the external expertise needed to ensure a smooth transition.
By embracing this new standard, your organization can finally break free from the expensive cycle of reaction. You can stop just documenting damage and start proactively preventing it, turning internal risk management into a strategic advantage that protects both the company and its people.
The Measurable Success of Modern Insider Risk Programs
The conversation around insider threats has moved beyond fear and damage control. A massive shift is underway, with organizations investing in formal, proactive insider risk management programs. The results prove this strategy delivers significant business value and a strong return on investment.
The data shows that a mature, well-resourced program doesn’t just mitigate risk—it builds a more resilient and efficient organization.
Adoption of these programs has exploded. An incredible 81% of organizations now have a formal insider risk management program in place. That's a huge leap from the mere 10% adoption predicted just a few years back. This isn’t a fleeting trend; it’s a strategic pivot driven by a clear understanding that proactive prevention is the only effective defense against human-factor risk.
From Cost Center to Value Driver
Modern insider risk programs are proving their worth by preventing breaches and saving critical resources. A remarkable 65% of organizations with a formal program reported it was the sole security strategy that allowed them to preempt a breach before any damage was done. This highlights the crucial pivot from reactive forensics to proactive prevention.
On top of that, these programs make incident response faster and more efficient. When a breach does happen, 63% of companies with a mature program reported significant time savings during the response phase. That speed is critical, as every single day saved dramatically reduces the financial and reputational fallout of an incident.
Following the Money: A New Budgetary Priority
Executive leadership and boards are recognizing this value and are putting serious money behind it. Insider risk management now represents 16.5% of the average IT security budget, a substantial jump from just 8.2% previously. That works out to an average of $402 per employee dedicated specifically to managing internal threats.
But even with this increased investment, the challenge remains massive. 45% of security leaders say that current funding levels are still not enough to fully address the scale of the problem. While progress is strong, the need for continued focus and investment remains high.
For the first time ever, the average time to contain an insider incident has decreased, dropping from 86 to 81 days. This is the most compelling proof of success. Seeing this metric fall, especially while the frequency of incidents is rising, shows that mature programs can absolutely turn the tide.
However, the journey isn't over. Operational roadblocks, like the fact that 60% of HR-security coordination is still done manually, reveal there's still a lot of room for improvement. Advanced, non-intrusive technology is the key to closing that gap.
You can explore these findings and learn about the impact of mature insider risk programs yourself. The evidence is undeniable: investing in an ethical, proactive framework isn't just about avoiding losses—it's about building a stronger, more efficient, and more secure enterprise.
It's Time to Take Control of Your Internal Risk Landscape
Knowing what insider threats are is one thing, but building real resilience requires a decisive shift in strategy. The evidence is overwhelming: old-school reactive forensics and intrusive employee surveillance are failing. They are too slow, too expensive, and they shatter the workplace trust required for effective operation.
The only sustainable path forward is to embrace a new standard of proactive, ethical prevention that gets ahead of risk before it causes real damage.
This isn't just about new software; it's a fundamental change in mindset. It means moving from a culture of catching misconduct to one that actively cultivates a secure and resilient environment. It’s about giving your HR, Compliance, and Security teams the AI-driven intelligence they need to intervene early and constructively—protecting both the company’s assets and your employees’ dignity. This proactive stance is a strategic commitment to operational integrity and a healthy, high-trust corporate culture.
Charting Your Path to Proactive Prevention
Moving from theory to practice starts now. Your organization can begin this journey by exploring a new generation of non-intrusive, EPPA-aligned solutions like Logical Commander's E-Commander, built for the realities of the modern workplace. Instead of waiting for the next incident report, you can take control of your internal risk landscape today.
Of course, human behavior is just one piece of the puzzle. Managing your internal risk also demands solid policies for your physical and digital assets. This includes processes like proper IT asset lifecycle management to ensure discarded equipment doesn’t become your next data breach. You can learn more in this a simple guide to IT asset lifecycle management.
Ultimately, protecting your organization from the inside out is one of the most critical responsibilities a leader has. By adopting an ethical, AI-driven approach, you can finally stop chasing past events and start shaping a more secure future. This strategy gives you the foresight to mitigate risks tied to fraud, misconduct, and compliance failures before they mushroom into full-blown crises.
The ultimate goal is to move beyond the endless cycle of detection and response. A truly mature internal risk program transforms this function from a reactive cost center into a proactive, strategic advantage that protects your people, your data, and your reputation.
Now is the time to build a framework that prevents incidents rather than just documents them. Take the next step to secure your organization from within.
At Logical Commander Software Ltd., we provide the platform to make this transition seamless. Discover the power of ethical, non-intrusive internal threat prevention and transform your approach to human-factor risk.
Get Platform Access and start your free trial.
Request a Demo for a personalized walkthrough.
Join PartnerLC to become a partner in our ecosystem.
Contact Our Team for an enterprise deployment consultation.
%20(2)_edited.png)
