A Clear Insider Threats Definition for Enterprise Risk Management
- Marketing Team

- 4 days ago
- 12 min read
Updated: 5 hours ago
Focusing only on bigger walls to keep attackers out is a critical oversight. The most devastating business risks—and the most expensive—often originate from people who already have the keys to your kingdom.
Leaders in Compliance, Risk, and HR spend countless resources fortifying perimeters against external attacks, yet they often overlook the human-factor risks within their own organization.
An insider threats definition must encompass any significant business risk originating from within an organization. It's a fundamental human-factor challenge that reactive security tools, especially those labeled as "cyber," were never designed to address. This is a human problem that requires a human-centric, preventive solution.
Moving Beyond a Technical Insider Threats Definition
Here's the critical insight: these threats aren’t always caused by a disgruntled employee planning sabotage. More often, they are the result of a trusted team member making an unintentional—but costly—mistake.
A truly useful definition of insider threats must be broad enough to cover this entire spectrum of human-factor risk. It’s a major misstep to focus only on malicious intent when simple human error can cause just as much, if not more, financial and reputational damage.
This is why any modern framework for managing internal risk must account for the reality of human behavior in a complex business environment. It starts and ends with people, not technology.
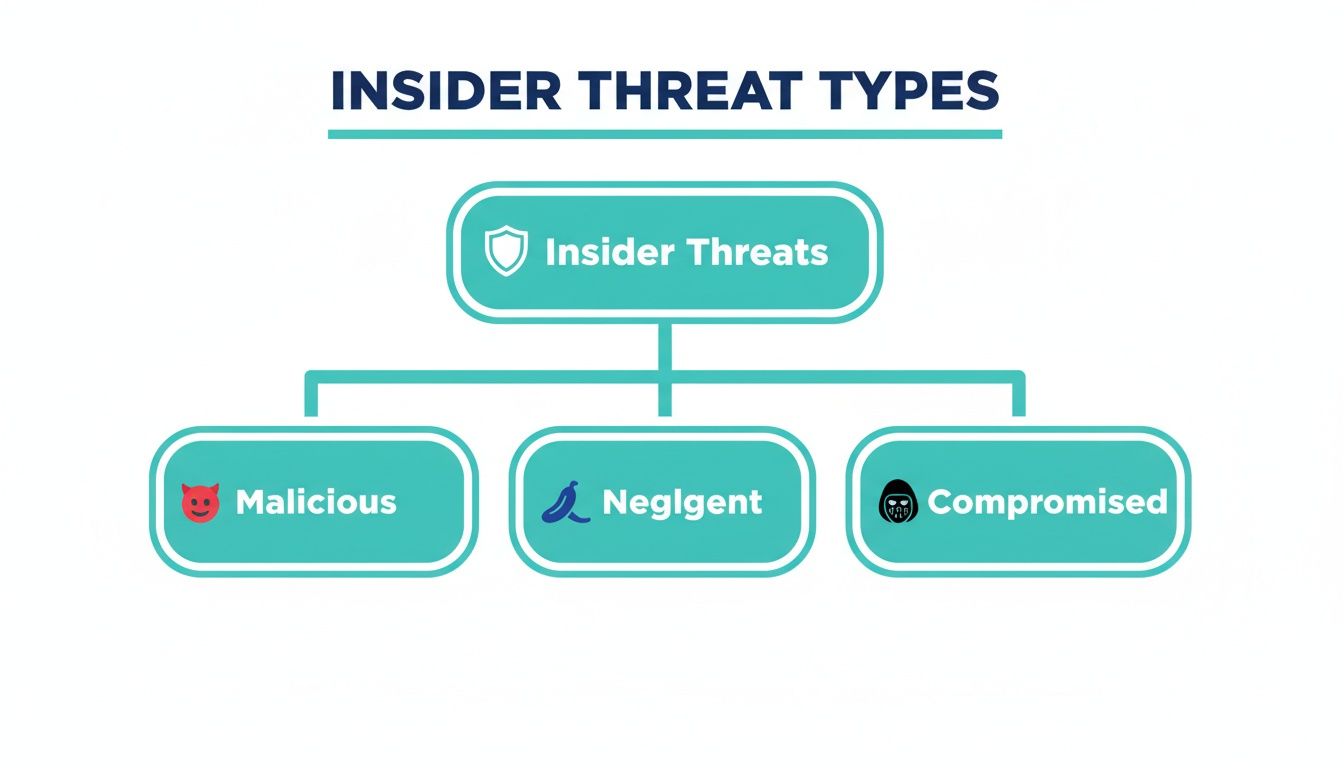
The Three Pillars of Insider Threats
To manage internal risk effectively, you have to understand its three primary forms. Each is driven by a different human factor, but all can lead to catastrophic outcomes like data breaches, financial fraud, or major compliance violations.
Here’s a simple breakdown of the three types of insider threats, their drivers, and their business impact.
Understanding the Core Insider Threat Types
Threat Type | Primary Driver | Business Impact Example |
|---|---|---|
Malicious Insider | Intentional Harm (Revenge, Espionage, Financial Gain) | A disgruntled sales manager downloads the entire client database to take to a new competitor. |
Negligent Insider | Unintentional Error (Mistake, Lack of Awareness) | A finance employee clicks on a sophisticated phishing email, giving attackers access to the company's banking systems. |
Compromised Insider | Stolen Credentials (External Attack) | An attacker steals an IT administrator's login credentials and uses them to disable security controls and exfiltrate sensitive data. |
As you can see, the business impact is what matters, not just the intent. This human-centric view is critical because it shifts your entire strategy from reactive, blame-focused investigations to proactive, preventive risk management.
Authoritative bodies like CISA and NIST explicitly include unintentional acts in their definitions for this very reason. They recognize that what ultimately harms the business is the outcome.
Research consistently shows that negligence is the most frequent source of incidents. The Ponemon Institute found that negligent insiders account for 55% of all incidents, costing organizations an average of $8.8 million annually. You can learn more about the business impact of insider threats from Proofpoint's findings.
Understanding these distinctions is the first step toward building an effective and ethical prevention strategy. It allows your organization to address the root causes of risk—whether they’re process gaps, training needs, or behavioral indicators—without resorting to invasive surveillance that destroys employee trust and creates massive legal liabilities. The goal is to build resilience by understanding the human element, not by policing it.
Differentiating Malicious, Negligent, and Compromised Insiders
Not all insider threats are created equal, and a one-size-fits-all approach to prevention is guaranteed to fail. To build a risk management strategy that is effective, ethical, and EPPA-aligned, leaders in HR, Legal, and Compliance must first understand the different human motivations behind each threat. Any insider threats definition is incomplete without this crucial context.
Applying the same heavy-handed response to an employee who made an honest mistake as you would to one engaged in corporate espionage isn’t just inefficient—it’s a recipe for destroying morale and inviting legal trouble. Real prevention requires a nuanced understanding of the human-factor risks at play.
The Malicious Insider: The Willful Saboteur
When most decision-makers think of an insider threat, this is the profile they picture. The malicious insider is someone who intentionally misuses their authorized access to harm the organization, often driven by revenge, ideology, or personal financial gain. Their actions are calculated and deliberate, which makes them particularly dangerous.
Common examples of malicious insider actions include:
Corporate Espionage: Stealing intellectual property, trade secrets, or client lists to sell to a competitor.
Financial Fraud: Abusing system access to embezzle funds, alter financial records, or create bogus transactions.
Data Sabotage: Intentionally deleting critical data, disrupting operations, or planting malicious code out of spite after being terminated.
Understanding the deliberate nature of these actions, especially malicious data theft, underscores the need for effective data leak prevention strategies. Malicious insiders are a direct risk, but surprisingly, they are not the most common source of insider incidents.
The Negligent Insider: The Unintentional Risk
The largest and often most costly category is the negligent insider. These are not bad actors trying to cause harm. They are trusted employees who make unintentional mistakes, usually due to a lack of awareness, a gap in processes, or simple human error.
While there is no malicious intent, the business impact can be just as severe. In fact, research consistently shows that negligent insiders are responsible for the majority of all insider-related incidents. Some studies attribute as many as 55% of all incidents to this group.
Examples of negligent actions include:
Sending an email with sensitive customer data to the wrong person.
Falling for a sophisticated phishing attack and giving up their credentials.
Misconfiguring a cloud storage bucket, leaving confidential documents exposed to the public.
Using weak, easily guessed passwords for critical business systems.
These incidents point to a failure in process, training, or controls—not a failure of character. An effective risk management program focuses on shoring up these operational weak spots proactively, not punishing employees after the fact.
The Compromised Insider: The Unwitting Pawn
Finally, there's the compromised insider. This is an employee whose credentials have been stolen by an external attacker. In this scenario, the employee is not the perpetrator; they are the victim. The attacker then uses those legitimate credentials to masquerade as a trusted insider, moving undetected inside your network.
This type of threat is particularly tricky for traditional security tools to catch. Because the attacker is using valid credentials, their activity often looks legitimate. This allows them to bypass perimeter defenses and access sensitive systems without setting off immediate alarms.
The attacker's goal is often data exfiltration, deploying ransomware, or establishing a persistent foothold in the organization's network. The compromised insider essentially becomes a gateway for external threats to operate from within.
Differentiating these three types is the foundation of modern, ethical risk management. By tailoring prevention strategies to the specific risk—whether it's a behavioral indicator, a process gap, or a credential compromise—organizations can move from a reactive, punitive posture to a proactive and protective one. For a deeper dive into this approach, explore our guide on using behavioral assessments for human risk management.
Why Traditional Security Tools Fail to Stop Internal Risk
Many organizations operate under the dangerous assumption that their existing security stack has internal risk covered. It’s a costly mistake. The truth is, traditional tools were engineered to stop external attacks—to build a fortress wall. They were never designed to understand the complex, nuanced world of human-factor risk.
Their entire design is misaligned with the challenge. Solutions like Data Loss Prevention (DLP) and User Activity Monitoring (UAM) simply cannot grasp the full insider threats definition, which includes malicious, negligent, and compromised individuals. They are reactive by nature and often rely on invasive surveillance methods that introduce significant legal risk.
These tools operate on a flawed premise, watching for specific violations like emailing a "confidential" file. But they lack context for intent, making it nearly impossible to differentiate a malicious act from an honest mistake. This creates a flood of false positives, draining valuable resources and ensuring critical alerts get lost in the noise.
The Problem with a Reactive 'Policing' Mindset
The biggest failure of old-school tools is that they are completely reactive. They are designed to flag an issue only after it has happened—after data has been downloaded, a phishing link has been clicked, or a fraudulent transaction is in motion. This is like installing a fire alarm that only goes off after the building has burned down.
This outdated model is broken. It struggles to differentiate between the core categories of insider threats, let alone prevent them proactively.
As you can see, the root causes of internal risk are varied, yet the outcome is often the same: business disruption and financial damage. A system focused only on endpoint activity will always miss the crucial pre-incident indicators tied to human behavior and operational context.
High Costs and Legal Liabilities of Surveillance
By the time a reactive tool flags a serious incident, the organization is already playing defense. The damage is done. The focus immediately shifts to costly, disruptive forensic investigations. According to IBM, it takes an average of over two months just to contain an insider incident, paralyzing business operations the entire time.
This surveillance-based "policing" mindset also comes with significant legal and ethical baggage.
Employee Privacy Violations: Constant, invasive monitoring of employee communications and activities can easily cross legal lines and create a culture of distrust.
EPPA Non-Compliance: Many surveillance-based tools operate in a legal gray area that conflicts with regulations like the Employee Polygraph Protection Act (EPPA), which strictly prohibits using methods that resemble lie detection or create psychological pressure.
Damaged Morale: Treating employees like potential suspects is the fastest way to destroy psychological safety and drive your best people away.
The old model of reactive forensics is broken. It is expensive, disruptive, and legally risky. It forces organizations to wait for damage to occur before they can act—a strategy that is no longer viable.
This failure highlights the urgent need for a new standard in ethical, proactive risk prevention. Organizations need modern internal threat detection tools that can identify risk indicators before they escalate, all without resorting to invasive surveillance. It’s about shifting from suspicion to proactive, ethical risk management that protects both the company and its people.
The Growing Financial and Reputational Cost of Insider Incidents
Any insider threats definition that doesn’t start with the real-world business cost is missing the entire point. Internal incidents aren't a theoretical security problem; they are an escalating financial and operational liability. The costs go far beyond the direct losses from a single act of fraud or a data breach, creating a ripple effect that can cripple an organization for years.
Understanding the true price tag is the key to making the business case for shifting from a reactive posture to a proactive prevention strategy. The numbers paint a clear and urgent picture of a problem that is growing in frequency, velocity, and financial impact every single year.
The Direct and Hidden Financial Drain
When an insider incident hits, the initial financial damage is just the opening act. The immediate costs of containment and remediation are quickly dwarfed by a cascade of secondary expenses that are often far more damaging in the long run.
These costs aren't just one-time hits; they're a long-term drain on your resources:
Regulatory Fines: Getting caught out of compliance with data protection laws like GDPR or HIPAA can lead to crippling financial penalties.
Expensive Legal Battles: The organization may face lawsuits from affected customers, partners, or even the insiders themselves.
Lost Customer Loyalty: A breach of trust is incredibly difficult to repair. A single high-profile incident can trigger mass customer churn and tarnish your brand for years.
Declined Productivity: Internal investigations disrupt normal business operations, pulling key personnel away from their core responsibilities and damaging employee morale across the board.
The speed and volume of these incidents have exploded. According to 2023 data, a staggering 71% of companies experienced between 21 and 40 insider threat incidents annually. The number of incidents studied surged from 3,269 in 2018 to an expected 7,868 in 2025—a massive 140% increase. To make matters worse, insider-related breaches take an average of 292 days to identify and contain, creating huge windows of vulnerability. You can discover more insights about these alarming insider threat statistics at BrightDefense.
The Time-to-Containment Liability
The massive delay in detecting and containing an internal incident is one of the biggest factors driving up costs. A reactive approach, which waits for an alarm to sound, guarantees that the damage is already done by the time an investigation begins. This delay isn't just an inconvenience; it's a massive financial liability.
Every day an incident goes undetected, the potential for financial loss, data exfiltration, and reputational harm multiplies. This extended dwell time is a direct consequence of relying on outdated, reactive tools that were never designed to understand human-factor risk.
Waiting for an incident to happen before you act is a failed strategy. For a deeper look into the expenses and operational drag of this outdated model, read our analysis on the true cost of reactive investigations. This data makes a powerful business case for shifting investment from reactive clean-up to proactive, ethical prevention, showing a clear ROI by avoiding catastrophic financial and reputational damage before it ever occurs.
Adopting a New Standard for Proactive Risk Prevention

The old model of managing internal risk is broken. It was built on a reactive foundation: wait for something to go wrong—a data breach, an ethics violation, a compliance failure—and then launch a disruptive and costly investigation to figure out who to blame. This approach is a relic.
A modern insider threats definition demands a new standard of risk management—one that is ethical, non-intrusive, and EPPA-aligned. This new standard, embodied by Logical Commander's E-Commander and Risk-HR platform, flat-out rejects invasive surveillance, employee monitoring, and any method that resembles lie detection. The focus is on preserving employee dignity and building organizational resilience.
Our AI-driven platform identifies critical human-factor risk indicators before they escalate into incidents. By analyzing contextual patterns, this approach gives you the foresight needed to manage risk without ever crossing ethical or legal lines.
Empowering Teams with Actionable Intelligence
This proactive approach completely changes how HR, Legal, and Compliance teams operate. Instead of getting dragged into emergency clean-up operations after a breach, they are empowered with actionable intelligence to mitigate risks early.
This is about fostering a culture of security, not suspicion. It enables leaders to address a process gap, offer targeted training, or provide support to an employee before an unintentional mistake leads to catastrophic consequences. The method respects privacy while ensuring solid governance.
The goal is to stop fires before they start, not just get better at putting them out. This preventive posture is the only sustainable way to manage the complexities of human-factor risk.
The Clear Contrast: Proactive Prevention Over Reactive Forensics
The difference between the old, reactive model and this new, proactive standard is stark. One waits for failure and assigns blame; the other anticipates risk and builds resilience. For any organization serious about protecting both its assets and its people, that distinction is everything.
A forward-thinking strategy doesn't just catch problems—it prevents them. You can explore our detailed guide on the benefits of proactive insider risk prevention to see how this modern approach works.
Reactive Forensics Versus Proactive Prevention
The table below highlights the fundamental differences between old, invasive methods and the new ethical standard for managing internal risk.
Attribute | Traditional Reactive Investigations | Logical Commander's Proactive Prevention |
|---|---|---|
Timing | Post-incident; acts only after damage has occurred. | Pre-incident; identifies risk indicators before they escalate. |
Focus | Assigning blame and conducting costly forensic analysis. | Addressing root causes and mitigating risk early. |
Method | Relies on invasive surveillance and employee monitoring (legally risky). | Utilizes non-intrusive, ethical, and EPPA-aligned AI analysis. |
Employee Impact | Creates a culture of distrust and damages morale. | Preserves employee dignity and fosters a culture of security. |
Cost | Extremely high due to investigations, fines, and business disruption. | Low, with a clear ROI by preventing costly incidents. |
Legal Risk | High potential for privacy violations and EPPA non-compliance. | Fully compliant, minimizing legal and ethical liabilities. |
This new standard isn't just a better way to manage risk—it's the only way to get ahead of it. By shifting from a reactive "policing" mindset to a proactive prevention framework, organizations can finally address the full spectrum of internal threats effectively and ethically.
Adopting this modern approach allows your organization to move with confidence, knowing you have the tools to protect against preventable harm without sacrificing the trust and integrity of your workforce.
Your Questions on Insider Risk, Answered
When it comes to managing internal threats, leaders in Compliance, HR, and Security have pressing questions. It’s a complex issue, and the old playbooks no longer work. Let's clarify how a modern, ethical approach can protect your business.
Getting these fundamentals right is the first step in moving away from a reactive, clean-up-the-mess model and toward a strategy that genuinely safeguards your organization from the inside.
Is an Employee Making an Honest Mistake Really an Insider Threat?
Yes, absolutely. A complete insider threats definition must include unintentional acts, because the business impact is often the same. Industry data consistently shows that simple negligence is the root cause of most insider incidents, far outpacing malicious intent.
Accidentally emailing sensitive data to the wrong person or misconfiguring a cloud server can lead to the same massive financial and reputational fallout as deliberate sabotage. That’s why a real prevention strategy must address human error and process gaps, not just hunt for bad actors.
How Can You Identify Risk Without Monitoring Employee Activity?
This is the critical distinction between our new standard and outdated surveillance. Effective risk prevention has nothing to do with invasive monitoring. Instead of reading private emails or tracking keystrokes—practices that are legally toxic and destroy employee trust—our AI-driven platform analyzes contextual risk indicators and operational patterns tied to job functions and access levels.
By focusing on the "what" and "why" of a potential risk rather than the "who" in a punitive sense, we identify crucial warning signals in a completely ethical and EPPA-compliant manner. This non-intrusive approach protects employee privacy while giving the organization the foresight it needs to prevent incidents.
This method preserves employee dignity while delivering powerful, proactive insights. It’s the new standard for ethical risk management.
How Does an AI Platform Support HR and Compliance Teams?
An AI-driven risk platform like Logical Commander transforms internal risk management from a scattered, manual burden into a proactive, strategic function. It gives HR and Compliance teams centralized, actionable intelligence, finally replacing the siloed spreadsheets and missed signals that leave organizations vulnerable.
Instead of spending months investigating a disaster after the fact, our platform delivers early-stage alerts on potential conflicts of interest, fraud risks, or compliance gaps. This empowers your teams to step in constructively and neutralize a risk before it spirals out of control.
Every step is documented for governance and audit purposes, ensuring your process is consistent and defensible. This proactive capability frees your teams from costly clean-up mode and allows them to focus on what really matters: strategic prevention that protects both the organization and its people.
Ready to adopt the new standard in proactive, ethical risk prevention?
Logical Commander offers an EPPA-aligned, AI-driven platform that identifies internal human-factor risks without surveillance. Protect your organization from the inside out and move from reactive investigations to proactive prevention.
Request a demo or get platform access to see the E-Commander / Risk-HR platform in action.
Become an Ally by joining our PartnerLC program for B2B SaaS resellers and consulting firms.
Contact our team for a confidential discussion about enterprise deployment.
%20(2)_edited.png)
