How to Prevent Employee Theft Without Invasive Surveillance
- Marketing Team

- Dec 11, 2025
- 14 min read
Updated: Dec 12, 2025
Preventing employee theft is not about catching individuals after the damage is done. For today's leaders in Compliance, Risk, and Security, it’s about architecting an ethical, EPPA-aligned framework that neutralizes human-factor risk before it materializes. This means abandoning outdated, intrusive surveillance and costly reactive investigations for a new standard: an AI-driven, proactive strategy focused on identifying and closing systemic vulnerabilities.
The ultimate goal is to protect your organization's assets, reputation, and bottom line without eroding the trust of your workforce.
The Real Cost of Employee Theft and Why Reactive Methods Fail
When business leaders think about how to prevent employee theft, their focus often lands on the immediate financial loss—the missing inventory or the fraudulent expense report. While these direct costs are significant, they represent only a fraction of the total business impact. The true cost of internal threats is a cascade of financial, operational, and reputational consequences that can destabilize an entire organization.
Understanding this full spectrum of liability is the first step toward building a preventive risk management strategy that actually protects the business.
The financial bleed from employee theft is staggering. In 2025, the annual cost in the US alone ballooned to nearly $50 billion, a massive jump from previous years. This data signals a clear failure: the conventional, reactive methods most companies rely on are not working. For more context on these trends, you can review key employee theft statistics on metrobi.com. This isn't a minor operational leak; it's a major financial drain that directly impacts profitability, growth, and organizational stability.
Beyond the Balance Sheet
The damage extends far beyond direct financial losses. The hidden costs of internal threats often inflict more lasting harm on the business.
Reputational Damage: A single incident of internal fraud can poison customer trust and tarnish a brand's reputation for years, eroding market value. This is especially damaging in regulated industries where governance and integrity are paramount.
Decreased Morale: When theft occurs, it injects an atmosphere of suspicion and distrust into the workplace. Honest employees feel devalued and demoralized, which inevitably leads to lower productivity and higher turnover.
Operational Disruption: Investigating theft is a massive resource drain. It pulls HR, Legal, and Security teams away from strategic, forward-looking initiatives and forces them into a reactive, backward-looking fire drill that offers zero ROI.
This is precisely why the traditional, reactive approach to managing insider risk is so fundamentally broken. Waiting for an incident to occur before taking action isn't a strategy; it’s a guaranteed business failure.
Reactive investigations are a costly exercise in damage control, not a solution. They happen after the financial loss has occurred, the trust has been shattered, and the reputational risk is already public. The goal must be to prevent the fire, not just put it out.
The Failure of the Old Standard
For decades, the standard response to suspected employee theft has been a reactive investigation. This script is predictable: gather evidence, conduct interviews, and take disciplinary action—all after the fact. This method is not only inefficient but also loaded with legal and ethical liabilities that modern compliance leaders can no longer afford to ignore.
Forensic accounting, legal consultations, and the operational downtime needed for a full-scale investigation can quickly spiral into tens or even hundreds of thousands of dollars for a single incident. As you can see in our guide to the true cost of reactive investigations, these expenses often dwarf the actual value of what was stolen.
Worse, traditional investigative techniques like surveillance or coercive interviews create significant legal risk. Methods that feel intrusive can violate regulations like the Employee Polygraph Protection Act (EPPA), opening the door to legal challenges, regulatory fines, and further reputational harm. The reactive cycle is a resource-intensive trap that fails to address the root cause of the problem, ensuring history will repeat itself. It’s time for a new standard—one focused on ethical, proactive prevention.
Reactive Investigations vs Proactive Prevention
The shortcomings of the old reactive model become crystal clear when you compare it to a modern, proactive approach. The difference isn't just about timing; it's a fundamental shift in philosophy, cost, and long-term business impact.
Metric | Reactive Investigations (Old Standard) | Proactive Prevention (New Standard) |
|---|---|---|
Timing | Post-incident; after the damage is done. | Pre-incident; identifies risks before they escalate. |
Focus | Assigning blame and recovering assets. | Understanding vulnerabilities and strengthening controls. |
Cost | High and unpredictable (legal, forensic, operational). | Lower, predictable investment in systems and culture. |
Cultural Impact | Creates suspicion, fear, and erodes trust. | Fosters integrity, transparency, and psychological safety. |
Legal Risk | High risk of violating employee rights (e.g., EPPA). | Low risk; designed to be ethical and legally compliant. |
Outcome | Damage control; a temporary fix for one problem. | Systemic improvement; reduces future incidents. |
Ultimately, the table shows a clear choice: organizations can remain trapped in an expensive cycle of cleaning up messes, or they can adopt an intelligent model that prevents those messes from happening. The latter is not only more cost-effective but also builds a stronger, more resilient organization.
Building Your Proactive Prevention Framework
If you're only dealing with employee theft after it happens, you've already lost. Moving from a reactive cleanup crew to a proactive prevention mindset is a fundamental shift in business strategy. It’s not about building higher walls or installing more cameras; it’s about creating a smarter, more transparent environment where the opportunities and motivations for misconduct are systematically dismantled at the human-factor level.
A truly robust prevention framework is your first and best line of defense against the kind of insider risk that can cripple a business. This starts with policies that are clear, accessible, and consistently enforced. Generic, legalese-filled documents collecting dust on an intranet portal are useless. Your policies must be woven into the daily operational fabric of your company.
Designing Policies That Actually Work
The real strength of your prevention strategy lies in its clarity. Employees need to understand not just the rules, but the business principles behind them. Your goal is to design policies that are incredibly easy to follow and incredibly difficult to bypass.
Here are a few key areas to lock down:
Asset Handling: Create specific, documented procedures for handling cash, inventory, and company equipment. Define exactly who has access, under what conditions, and what the verification process looks like at every stage. Eliminate gray areas.
Data Access Controls: Limit access to sensitive financial and operational data to only those who absolutely require it for their roles. Regularly audit these permissions to ensure they align with current job functions, not past ones.
Expense and Reimbursement Reporting: Implement a multi-level approval process for all expenses. Use software to flag anomalies—like duplicate submissions or unusually high claims—before a single dollar is ever paid out.
This diagram breaks down the fundamental differences between a reactive investigative process and a proactive prevention framework.
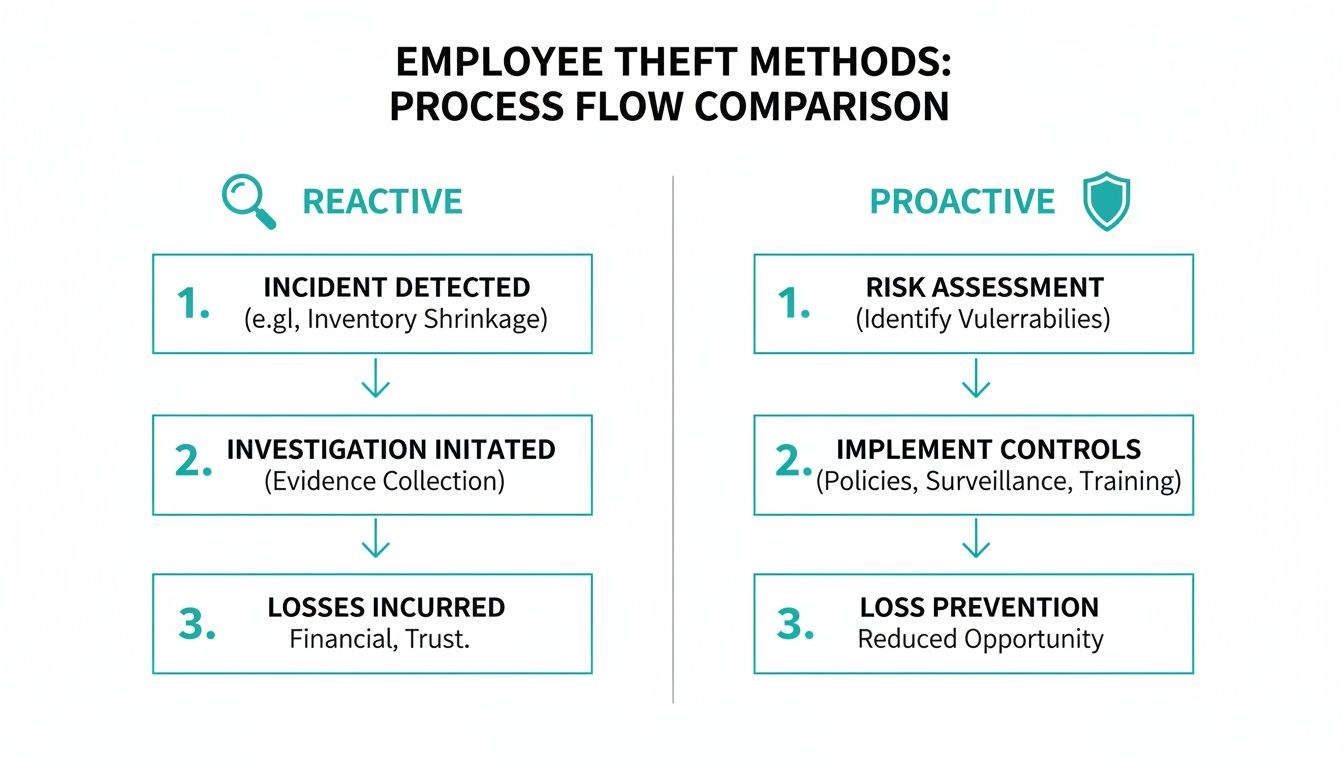
As you can see, a proactive approach identifies and addresses risk factors long before an incident occurs. Reactive methods are stuck responding to damage that's already been done.
The Role of Culture and Screening
Strong policies create barriers to theft, but a positive company culture removes the motivation. When employees feel valued, respected, and fairly compensated, the temptation for misconduct plummets. Transparency from leadership, clear communication channels, and equitable treatment are the cornerstones of a high-integrity workplace.
This proactive mindset must also extend to your hiring process. Compliant pre-employment screening is a critical step in identifying potential risks before they enter your organization. This isn't about looking for "bad apples." It’s about ensuring that candidates have a history consistent with the level of responsibility they’ll be given.
This is a key component of a comprehensive human capital risk management strategy, designed to protect your organization from the inside out. For a deeper dive, check out our guide on human capital risk management.
Building a culture of integrity is not a "soft" initiative; it's a hard-nosed business strategy. An environment of transparency is one of the most effective, yet often overlooked, tools for how to prevent employee theft.
The reality is that workplace theft is alarmingly common. Studies reveal that a staggering 75% of employees admit to stealing from their employer at least once, a figure that highlights a deeply rooted issue across all sectors. This isn't a problem confined to a few industries; it's a global challenge that directly contributes to nearly 30% of all business bankruptcies. The urgency here is undeniable, demanding a framework that addresses both systemic vulnerabilities and cultural factors simultaneously.
Using AI for Ethical and Non-Intrusive Risk Detection
To get ahead of employee theft, organizations must move beyond old-school surveillance and reactive investigations. The new standard in internal risk management is not about catching people after the fact; it’s about understanding systemic vulnerabilities before they lead to an incident. This means leveraging intelligent, AI-driven platforms to identify the early warning signs of risk—without resorting to invasive monitoring or legally questionable tactics that violate EPPA.
This isn't about watching employees. It's about gaining a clear, objective understanding of your organization's human-factor risk landscape. By analyzing behavioral risk indicators in a fully EPPA compliant manner, you gain early warnings that allow for supportive, corrective interventions. It’s a smarter way to work, protecting the business, strengthening governance, and upholding employee dignity.
This is what a modern, non-intrusive platform looks like. It provides a clear view of organizational risk without invasive surveillance.

The key here is that data can be ethically analyzed to reveal patterns and weak points, giving leaders the intel they need to make proactive decisions.
Moving Beyond Surveillance
Traditional methods like security cameras and keystroke logging create a culture of distrust and often fail to prevent sophisticated threats like embezzlement or data theft. They generate tremendous noise, are a nightmare to manage, and come with significant legal risks tied to privacy and compliance. Invasive surveillance technologies are the old, broken standard.
An AI-driven approach is fundamentally different. It operates on a foundation of ethical data analysis, focusing on what is happening at a systemic level, not who is doing it.
Here’s how this new standard actually works:
Non-Intrusive Analysis: It assesses risk indicators without monitoring personal communications or tracking individuals. The focus is purely on anomalies in processes and operational data.
Privacy-Respecting by Design: The technology is built from the ground up to comply with strict regulations like EPPA, ensuring it never crosses the line into prohibited lie detection or psychological evaluation.
Focus on Systemic Risk: Instead of targeting individuals, it identifies weaknesses in your internal controls, policies, and workflows that create opportunities for misconduct.
This is the very core of modern AI human risk mitigation. It gives leadership the intelligence needed to fortify defenses before a breach ever happens.
How E-Commander and Risk-HR Set a New Standard
Platforms like Logical Commander’s E-Commander, with its Risk-HR module, exemplify this forward-thinking approach. The system is engineered to detect patterns that signal elevated risk without ever needing to "spy" on employees. It provides a centralized view of internal threat intelligence, empowering HR, Compliance, and Security teams to act collaboratively and preemptively.
For instance, the platform can flag things like:
Anomalies in Financial Transactions: It can spot unusual patterns in expense reports or vendor payments that deviate from established norms, suggesting a potential breakdown in financial controls.
Irregularities in Data Access: It highlights when access permissions are misaligned with job roles or when sensitive data is accessed in a way that suggests heightened risk—all without reading the content itself.
Breakdowns in Operational Procedures: The system identifies deviations from standard operating procedures that could be exploited, whether intentionally or not.
The goal of this technology isn't to create a list of suspects. It is to provide actionable intelligence that allows you to strengthen your processes, refine your policies, and offer targeted training where it's needed most. It’s prevention, not policing.
For truly advanced risk detection, understanding how to apply machine learning fraud detection can be an incredibly powerful tool in your prevention strategy. This technology is brilliant at finding subtle patterns in massive datasets that a human analyst might miss, making it an essential part of a proactive defense.
By focusing on these systemic indicators, you can address vulnerabilities at their source. This method helps prevent everything from simple inventory theft to complex financial fraud, all while maintaining a culture of respect. It’s simply a smarter, more ethical way to secure your organization from the inside out. To learn more, explore our detailed guide on detecting insider threats with ethical AI.
Weaving Proactive Controls and Training into Your Culture
AI-driven insights provide a strategic roadmap to your biggest risks, but technology alone doesn't stop theft. The real business impact comes when you pair those intelligent systems with practical, on-the-ground measures that your team lives and breathes every day.
By implementing rock-solid internal controls and making training a continuous process, you turn abstract policies into real-world actions. It’s about building a framework where doing the right thing is simply the easiest and most logical path for every employee. This isn't about policing people; it's about designing out the opportunity for misconduct in the first place.
Fortifying Your Internal Controls
Weak internal controls are a wide-open invitation for internal threats. The goal is to create clear, documented, and consistently enforced procedures for your most vulnerable areas—inventory, cash handling, and intellectual property. A critical first step is establishing clear Standard Operating Procedures (SOPs) that leave no room for guesswork.
Focus on these key control points:
Inventory Management: Go beyond the annual audit. Implement regular, unannounced cycle counts and use automated systems to track stock from the moment it arrives to the moment it leaves. This creates an objective data trail that makes it much harder for inventory to simply vanish.
Cash Handling Procedures: This is non-negotiable. Enforce a strict separation of duties—the person handling cash receipts should never be the same person reconciling the books. Mandatory daily drawer reconciliations and secure deposit protocols are your best friends here.
Intellectual Property Protection: Your most valuable assets might be digital. Use access control systems to lock down sensitive data, ensuring only authorized personnel can access it. Regular audits of who accessed what, guided by your AI's anomaly detection, can flag a potential data leak long before it happens.
These controls aren't about creating bureaucratic headaches. They’re about building predictable, transparent processes that protect the company and, just as importantly, its honest employees.
Training That Goes Way Beyond the Onboarding Manual
A quick mention of the company theft policy on day one is not training; it’s a box-checking exercise that accomplishes nothing. Effective training isn't a one-time event. It’s an ongoing conversation that reinforces ethical conduct and demonstrates the real-world consequences of theft for the business and its employees.
An effective training program doesn’t just recite rules. It builds a shared understanding of why integrity is the bedrock of the company’s success and how each person’s actions directly contribute to a culture of security and prevention.
This is where insights from your AI risk assessments become a powerful tool. Forget generic, one-size-fits-all modules. You can now develop targeted programs that address the specific vulnerabilities your data has uncovered. If you see a higher risk in expense reporting, for instance, you can create workshops with specific, relevant scenarios for that department.
Time theft is a perfect example of a silent killer that targeted training can address. Shockingly, recent surveys show 67% of employees admit to some form of workplace theft, with time theft—like padding timesheets or taking extended breaks—being the most common. On average, employees inflate their work hours by around 4.5 hours every single week. This is a massive, often hidden, financial drain.
To build an educational framework that actually sticks, you need to go deeper. Our guide on integrity training courses offers a blueprint for creating content that resonates with employees and drives real behavioral change. When you connect policies to their real-world impact and provide continuous reinforcement, you transform your workforce from a potential risk into your greatest security asset.
Building a Culture of Integrity That Lasts
Preventing employee theft is not a one-and-done project. You can't just write a policy, file it away, and hope for the best. Real prevention comes from building a culture of integrity, and that effort has to be driven, visibly and authentically, from the very top.
A strong ethical culture is your organization's ultimate defense against internal threats. It’s a living, breathing part of your company that policies and controls can support but never replace. When your leadership team consistently models integrity—making tough, principled decisions and celebrating others who do the same—it sends a powerful message. It tells everyone that cutting corners isn't an option.

Give People a Safe Way to Speak Up
Even in the most positive work environments, employees need a safe way to flag a concern. Most will never report suspicious activity to their direct manager for fear of being labeled or facing retaliation. That’s why setting up confidential reporting channels isn't just a good idea; it’s absolutely essential for effective governance.
An effective system should offer multiple options, so people can choose what feels safest:
An Anonymous Hotline: Preferably run by a third party to guarantee impartiality and give employees confidence their identity is protected.
A Dedicated Email Address: Monitored by a small, trusted group in HR, Legal, or a dedicated compliance role.
A Designated Integrity Officer: A senior leader who is widely known and respected across the company.
The whole point is to create psychological safety. Your team needs to see that reports are taken seriously and that they can raise a red flag without any fear of blowback. This trust is built through consistent action, not just words on a poster.
Audit Your Processes, Not Your People
Your business is constantly evolving, which means the policies and controls you put in place last year may already have gaps. Regular, non-invasive process audits are your best tool for keeping defenses tight. These aren't surprise inspections designed to catch someone doing wrong. They are collaborative check-ins aimed at finding and fixing systemic weaknesses before they can be exploited.
A process audit isn't about looking for culprits; it's about finding vulnerabilities. The goal is to strengthen the system for everyone, making it harder for anyone to fail or fall into temptation.
Think of it as routine maintenance for your company’s integrity. By periodically reviewing high-risk areas like expense approvals, vendor payments, or inventory counts, you can spot vulnerabilities before they become problems. This proactive approach to governance and reputation protection demonstrates a real commitment to doing things the right way and reinforces the idea that the company is watching its processes fairly and ethically.
Empowering Partners to Build Resilient Organizations
Building this kind of deep-rooted organizational integrity is a heavy lift, and many organizations need an expert guide. That's exactly why we created the PartnerLC program. It's designed specifically for B2B SaaS companies, consultants, and advisory firms that share our vision for ethical risk management.
By joining our partner ecosystem, you can bring a new standard of proactive, non-intrusive internal threat prevention to your own clients. We provide access to our AI-driven platform and methodologies, empowering you to help other organizations build stronger, more ethical, and more profitable businesses. This is about working together to shift the entire industry away from reactive, punitive tactics and toward a future of intelligent prevention. Partnering with us means you can offer a truly different solution to one of the most stubborn challenges in business today.
Take the Next Step in Proactive Risk Prevention
Waiting for an incident to occur before you act isn't a strategy—it's a liability. Every reactive investigation, forensic audit, and reputational crisis is a sign that your preventive strategy has failed.
For leaders in Compliance, Risk, HR, and Internal Audit, sticking with that outdated, reactive model is no longer a viable option. The future of organizational protection is a proactive, ethical approach that safeguards the bottom line while reinforcing the trust you’ve built with your people and the market.
An AI human risk mitigation platform allows you to see and neutralize systemic vulnerabilities before they turn into seven-figure problems. It's time to move to a forward-thinking, EPPA compliant strategy. The message is clear: prevention is far more valuable than the cleanup.
Ready to lead the change and implement a new standard of internal risk prevention?
Request a demo to see how our E-Commander platform can transform your internal risk management.
Get platform access to start a free trial and explore our capabilities firsthand.
Join our PartnerLC program if you're a B2B SaaS company or consultant looking to deliver this new standard to your own clients.
Contact our team for a confidential discussion about enterprise deployment.
Don't wait for the next incident to prove the cost of doing nothing. Take the first step toward building a stronger, more secure organization and schedule a demo with our team today.
Your Questions on Preventing Employee Theft, Answered
When discussing a modern, ethical approach to internal risk, several key questions consistently arise from leaders in Compliance, HR, and Security. Here are the answers to the most common ones.
Is an AI-Driven System EPPA Compliant?
Absolutely. This is the most critical question, and the answer is an unequivocal yes. A modern AI human risk mitigation platform like ours is built from the ground up to strictly align with the Employee Polygraph Protection Act (EPPA).
It is designed to be completely non-intrusive. The system never functions as a lie detector or a tool for psychological evaluation, as that would be a direct violation. Instead, it analyzes systemic risk indicators found in operational data, not an individual’s personal behaviors or private beliefs. This focus on process vulnerabilities is key to an ethical risk management approach.
How Does This Differ from Surveillance?
The difference is fundamental. Surveillance technologies watch individuals, creating a culture of distrust and generating a mountain of noisy data that is nearly impossible to analyze effectively. It's the old, reactive way.
An ethical AI approach, a form of Risk Assessments Software, looks at anomalies in processes—such as financial transactions, data access patterns, or procurement irregularities.
It’s the difference between pointing a camera at an employee versus analyzing a financial ledger for irregularities. The former monitors people; the latter audits the system. This proactive method identifies systemic weaknesses before they can be exploited by any human factor.
Can This Approach Replace Internal Investigations?
A proactive system dramatically reduces the need for reactive investigations, but it doesn't eliminate them entirely. Its primary function is prevention—strengthening your controls and flagging risks long before they escalate into full-blown incidents.
By providing these early warnings, the platform enables you to intervene and resolve a process issue before it leads to loss. In many cases, this completely avoids the costly and damaging process of a formal investigation.
However, if an incident does occur, the data provides your team with a clear, objective starting point. It makes any necessary investigation faster, more focused, and far less disruptive. This is a core part of effective, ethical internal threat detection.
%20(2)_edited.png)
