A Practical Guide to Risk Assessment for Security
- Marketing Team
- 2 days ago
- 16 min read
A risk assessment for security is the methodical process of spotting, analyzing, and sizing up potential security threats to your organization's most critical assets. Think of it like a strategic home inspection; you don't just admire the paint. You check the foundation for cracks, scope out the neighborhood for potential trouble, and get a realistic appraisal of what everything inside is worth.
Getting this right is the absolute first step in building any security program that actually works.
What Is a Security Risk Assessment

At its heart, a security risk assessment goes way beyond simple checklists. It’s a proactive, systematic way to understand the complete threat picture by asking the right questions and connecting the dots between what you value, what can harm it, and where you're exposed. This isn’t just a task for the IT department; it's a core business function.
A proper assessment gives leaders the context they need to make smart decisions, channeling money and people toward protecting what truly matters. Without it, security spending is just a guessing game, leaving dangerous blind spots that adversaries are more than happy to exploit.
The Three Pillars of Security Risk
Every solid security risk assessment is built on three fundamental pillars. To really grasp the potential for harm, you have to understand how these three components feed into one another.
We can break down these core components in a simple table.
The Three Pillars of Security Risk Assessment
Component | Description | Example Question to Ask |
|---|---|---|
Assets | The valuable resources—tangible or intangible—that your organization needs to protect. | What data, systems, or intellectual property would cause the most damage if compromised or lost? |
Threats | Any potential event or circumstance that could cause harm to your assets, from cyberattacks to human error. | Who or what could realistically target our assets, and what methods might they use? |
Vulnerabilities | The weaknesses or gaps in your defenses that a threat could exploit to cause damage. | Where are our security controls weakest? An unpatched server? Untrained staff? |
Seeing how these three elements connect is the key. A threat actor exploiting a vulnerability to compromise an asset is the basic formula for every security incident.
A security risk assessment isn't a one-time project you complete and file away. It's a continuous cycle of discovery, evaluation, and adaptation—absolutely essential for navigating a world of ever-changing threats.
Expanding the Scope Beyond Technology
In the past, risk assessments were often stuck in silos. One team would handle cyber threats while another worried about physical security. But modern threats couldn't care less about those boundaries. A truly effective assessment has to look at the interconnected nature of cyber, physical, and insider risks as a single, unified problem.
The human element, especially, has moved front and center. Insider threats have surged, with some data showing a stunning 44% increase in incidents over just a two-year period. These risks, whether they stem from a malicious employee or just an honest mistake, prove why a holistic view is no longer optional. You can read more about the evolving security landscape at Securitas.com.
This unified approach ensures that a stolen ID badge isn't just seen as a physical breach, but as a potential key to a catastrophic data breach.
Connecting Cyber, Physical, and Insider Risks
Security threats don’t care about your org chart. They don’t respect departmental boundaries. That’s why a genuinely effective risk assessment for security has to tear down the old-school silos separating different risk domains and see them for what they are: a single, interconnected ecosystem. Thinking about these threats in isolation creates dangerous—and often predictable—blind spots.
To build a security program that can actually hold up under pressure, we have to explore three critical, overlapping areas of risk.
The Three Intersecting Risk Domains
Each domain brings its own unique challenges to the table, but their real danger is in how they feed off one another. Let's break them down:
Cyber Risk: This is the one everyone knows. It covers everything from malware and phishing scams to sophisticated data breaches and denial-of-service attacks. These threats are aimed squarely at your digital assets—your data, your networks, and your systems.
Physical Risk: This involves threats to your tangible assets and physical locations. Think someone gaining unauthorized access to an office, stealing equipment like laptops or servers, or even vandalism that shuts down your operations.
Insider Risk: This is the human element, and it's easily the most complex and unpredictable piece of the puzzle. It includes everything from a disgruntled employee acting maliciously to simple, unintentional human error, like an accountant falling for a phishing email.
The real "aha!" moment in modern security is realizing these aren't separate problems. They are just different doors that all lead to the same potential catastrophe. A physical breach can easily become the spark that ignites a major cyber fire.
How a Stolen ID Card Becomes a Data Breach
Picture this: a disgruntled employee is terminated, but their access badge isn't immediately deactivated. Right there, that’s a procedural vulnerability—an insider risk failure. That person could use the badge to walk right into the office after hours, which is a clear physical security breach.
Once they're inside, they might log into a workstation they still have access to, planting malware or walking out with sensitive customer data. What started as a simple HR and physical security lapse has now exploded into a full-blown cyber incident, one that could cost millions in damages and destroy public trust.
This chain reaction is precisely why a unified view is non-negotiable. A fragmented assessment sees a lost ID card, a network anomaly, and a disgruntled employee as three separate issues. A connected approach sees them as one coordinated threat pathway.
When you're thinking through the physical side of your security risks, exploring different access control mechanisms like magnetic locks for doors can be a key part of your assessment. The goal is to see how one vulnerability can be chained to another. For a deeper dive into the human factor, you might be interested in learning more about what insider threats are and how they show up.
The global threat landscape proves this interconnected view is the only one that matters. Cyber incidents have exploded, with reports showing a huge jump in weekly attack volumes across major markets. This surge makes it painfully clear that we need proactive, ethical ways to connect the dots before they escalate into a full-blown crisis.
Understanding this convergence is the first step toward building a security posture that doesn't just react to damage but actually anticipates threats before they ever materialize.
How to Conduct a Security Risk Assessment
Knowing that security threats are tangled together is one thing; doing something about it is another. Let's shift from theory to action with a practical, step-by-step method for conducting a security risk assessment. This isn’t some complex ritual reserved for specialists. It’s a repeatable framework any leader can use to get clarity and make smarter decisions.
This five-step process takes risk assessment from an abstract concept and turns it into a powerful tool for building real resilience.
As the diagram below shows, cyber, physical, and insider risks don’t stay in their own lanes. They flow into one another, creating complex and often unexpected ways for things to go wrong.
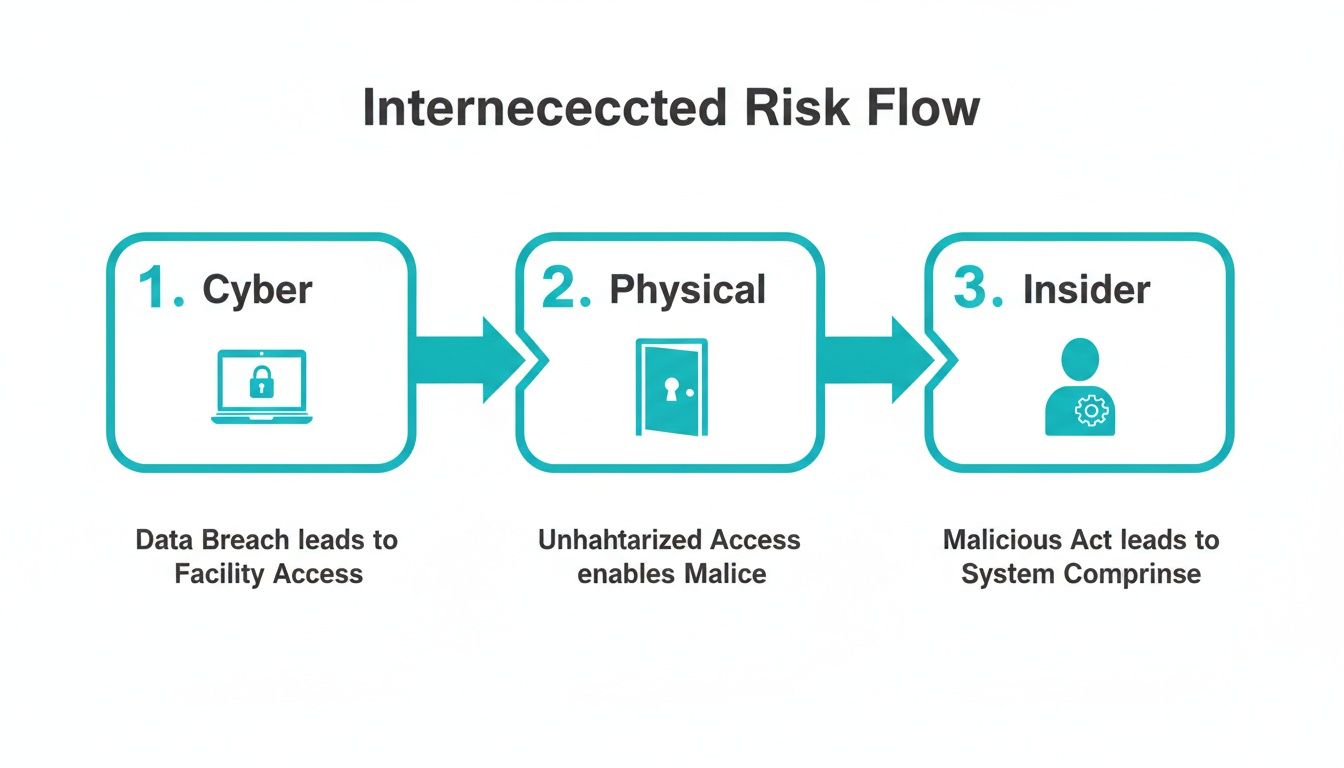
A failure in one area can easily create an opening for a breach in another, which is why a unified assessment process is non-negotiable.
Step 1: Identify and Value Your Assets
The first step in any meaningful risk assessment for security is to know what you’re protecting. And this goes way beyond a simple list of servers and laptops. Your most valuable assets are often the ones you can’t touch, and failing to identify them creates massive blind spots in your security strategy.
Get people from different departments together to build a complete asset inventory. Make sure it includes:
Digital Assets: Customer databases, proprietary source code, financial records, and sensitive employee information.
Physical Assets: Office buildings, data centers, manufacturing equipment, and critical infrastructure.
Intangible Assets: Brand reputation, intellectual property, customer trust, and even employee morale.
Once you have your list, assign a value to each asset. This isn't always a clean dollar amount. You have to consider the cost of replacement, the financial hit from downtime, regulatory fines from a data breach, and the long-term damage to your brand. An asset's value is simply what you stand to lose if it's compromised.
Step 2: Pinpoint Threats and Vulnerabilities
With a clear inventory of what you need to protect, the next job is to figure out what could harm those assets. This means looking for both threats (the "who" or "what" that could cause harm) and vulnerabilities (the weaknesses a threat could exploit).
Think of a threat as the storm and a vulnerability as the crack in the window. The storm itself can’t do much damage if the window is sealed tight.
Threat Identification: Brainstorm where the trouble could come from. This includes external actors like hackers and organized crime, but also internal risks like employee error or a malicious insider. Don't forget about natural disasters and supply chain disruptions, either.
Vulnerability Scanning: Now, look for the cracks. This could be unpatched software, a lack of employee security training, weak physical access controls, or policies that nobody actually follows.
This step requires an honest, critical look at your current defenses. It's about finding the gaps before an adversary does.
Step 3: Analyze the Potential Impact
Okay, time to connect the dots. For each threat-and-vulnerability pair you've identified, you need to analyze what would actually happen if that threat successfully exploited that weakness. This is where you figure out the real-world consequences of a security event.
The goal is to move from a messy list of risks to a structured understanding of their potential damage.
A common way to do this is by scoring risks on two key factors: likelihood (how probable is it that this will happen?) and severity (how catastrophic would the impact be if it did?).
For example, a phishing attack (threat) targeting untrained employees (vulnerability) to steal customer data (asset) might have a high likelihood but a moderate initial impact. On the other hand, a sophisticated state-sponsored attack on your core infrastructure may have a low likelihood, but its impact would be catastrophic.
Step 4: Evaluate and Prioritize the Risks
Not all risks are created equal. You have limited time, budget, and people, so you can't fix everything at once. This step is about using your analysis from Step 3 to rank your risks, which lets you focus your efforts where they'll have the biggest effect.
A risk matrix is a simple but powerful tool for this. By plotting each risk based on its likelihood and impact scores, you can visually separate the minor annoyances from the critical, drop-everything threats.
Risks that land in the high-likelihood, high-impact quadrant are your top priorities. These are the existential threats that demand immediate attention. Those in the low-likelihood, low-impact corner can probably be accepted or dealt with later.
Step 5: Develop Your Mitigation Plan
Finally, with a prioritized list of risks in hand, you can build an actionable plan to deal with them. For each high-priority risk, you have to decide on a course of action. Generally, there are four ways to handle a risk:
Avoid: Stop the activity that creates the risk in the first place.
Transfer: Shift the financial burden of the risk to a third party, usually through insurance or by outsourcing the function.
Mitigate: Implement security controls to reduce the likelihood or the impact of the risk. This is where most of your effort will go.
Accept: Formally acknowledge the risk and choose to do nothing, typically for low-priority items where the cost to fix exceeds the potential loss.
Your mitigation plan should be a concrete document. It needs to outline the specific controls to be implemented, assign responsibility to a team or individual, and set a clear timeline for getting it done. This is what transforms your risk assessment from a diagnostic exercise into a strategic roadmap for a stronger, more resilient security posture.
Choosing the Right Risk Assessment Framework
Trying to run a risk assessment for security without a framework is like trying to build a house without blueprints. You might end up with something that looks like a house, but it won't be structurally sound, repeatable, or easy for anyone else to understand. Frameworks give you the structure, the common language, and the methodology you need to get the job done right.
Navigating the alphabet soup of security frameworks, however, can feel a bit overwhelming. Each one brings a different philosophy to the table, designed for specific goals and organizational needs. The real secret isn't finding the one "best" framework, but picking the one—or the right combination—that actually aligns with your business goals, industry rules, and where you currently stand with your security maturity.
The Core Philosophies: Build, Prove, or Calculate?
Three of the biggest names you'll hear are the NIST Cybersecurity Framework (CSF), ISO/IEC 27001, and FAIR (Factor Analysis of Information Risk). These aren't mutually exclusive; in fact, mature organizations often weave them together. But their core approaches are fundamentally different.
NIST Cybersecurity Framework (CSF): Developed by the U.S. National Institute of Standards and Technology, the NIST CSF is a flexible set of guidelines and best practices. Think of it as a roadmap. It’s built to be adaptable for any organization, giving everyone a common language to talk about security posture and goals. NIST is all about building a solid program.
ISO/IEC 27001: This is an international standard that spells out the requirements for an Information Security Management System (ISMS). Unlike the flexible guide from NIST, ISO 27001 is a formal specification your organization can actually get certified against. ISO 27001 is about proving compliance.
FAIR (Factor Analysis of Information Risk): FAIR is a quantitative risk model. Its whole purpose is to help you understand and measure information risk in cold, hard financial terms. It gives you a structured way to think about risk factors and how they connect. FAIR is about calculating the financial impact.
Matching the Framework to Your Needs
So, which path is right for you? It all comes down to context. A company facing intense regulatory scrutiny has very different needs than a startup trying to build its first real security program from the ground up. Often, an integrated risk management solution needs to pull principles from all three to be truly effective.
The goal is to choose a path that delivers real, measurable value—not just compliance paperwork. The right framework should make your organization more secure and resilient, not just busier.
To help you figure out which approach might be the best fit, here's a high-level comparison to help you select the framework that best fits your needs.
Comparing Popular Security Risk Assessment Frameworks
Framework | Best For | Primary Focus | Key Benefit |
|---|---|---|---|
NIST CSF | Organizations of any size seeking a flexible, adaptable starting point for their security program. | Programmatic risk management and communication across the organization. | Provides a common language and roadmap for improving security posture without rigid requirements. |
ISO/IEC 27001 | Companies needing to demonstrate security compliance to customers, partners, or regulators. | Formal certification of an Information Security Management System (ISMS). | Delivers a globally recognized certification that builds trust and meets contractual obligations. |
FAIR | Businesses wanting to prioritize risks based on financial impact and justify security investments to executives. | Quantitative risk analysis and financial modeling of potential losses. | Translates complex technical risks into clear business language (dollars and cents) for better decision-making. |
In the end, many mature organizations don't just pick one. They create a hybrid approach. They might use the NIST CSF to structure their overall security program, get ISO 27001 certified to satisfy market demands, and then use FAIR to quantify their top five risks for the board of directors.
This combined strategy ensures that their risk assessment for security is not only thorough but also speaks the right language to every stakeholder in the business.
It's Time to Shift to Proactive and Ethical Security
Yesterday’s security playbook is failing. For too long, organizations have leaned on reactive, often invasive surveillance methods that only succeeded in creating a culture of mistrust. These old-school tactics, obsessed with catching people doing something wrong, aren't just ineffective—they’re becoming a massive liability in a world governed by strict privacy laws like GDPR.
The blunt instruments of the past simply don't work anymore.
This reality is forcing a critical evolution in how we approach a risk assessment for security. The future isn't about more surveillance; it's about smarter, more ethical prevention. It demands a fundamental shift from a mindset of suspicion to one of proactive support, where security and employee dignity aren't opposing forces but essential partners.
Adopting an "Ethical by Design" Philosophy
A modern security program has to be built on an "ethical by design" foundation. This approach hardwires privacy and respect directly into the risk assessment process from the very beginning. Instead of waiting for an incident and then hunting for someone to blame, this model focuses on identifying early, objective risk indicators.
The core idea is to separate the signal from the intent. Great security doesn't require knowing what's in someone's head. It requires recognizing objective actions or procedural gaps that create risk, regardless of why they occurred.
This means the focus moves away from monitoring employees and toward monitoring processes. For instance, instead of tracking keyboard strokes, an ethical system flags when an employee gains access to a sensitive file share that falls outside their job description. That’s a clear procedural violation that creates risk, whether it was accidental or intentional.
From Invasive Monitoring to Objective Indicators
This shift from subjective judgment to objective fact is the cornerstone of ethical security. It empowers teams across the organization—from HR and Legal to Security and Compliance—to intervene constructively before a minor issue becomes a major crisis.
Here’s how this proactive approach is worlds apart from outdated methods:
Focus on Governance Gaps: It flags when policies aren't being followed, like when an employee’s access permissions are not revoked in a timely manner after changing roles.
Identify Procedural Violations: It highlights deviations from established workflows, such as an unusual pattern of data downloads or attempts to bypass security controls.
Detect Conflicts of Interest: It can recognize situations where an individual's personal interests might conflict with their professional duties, based on structured data, not suspicion.
By concentrating on these verifiable signals, the risk assessment becomes a tool for improvement, not an instrument of accusation. When making this shift, bringing in outside expertise can be invaluable; consider exploring professional cyber security services to help guide the transition.
Empowering Teams with Data, Not Accusations
The true power of this ethical framework is that it provides decision-makers with the data they need to act early and fairly. When a risk indicator is flagged, it doesn't trigger an automatic punishment. Instead, it kicks off a structured, fair process of verification managed by the right department.
This allows HR to address a potential training gap, Legal to clarify a compliance misunderstanding, or Security to fix a vulnerability in a system. The conversation starts with objective evidence, which preserves employee dignity and ensures any intervention is supportive rather than punitive. For those interested in this approach, learning about ethical AI for early internal risk detection can offer deeper insights into how technology can support this model.
Ultimately, this proactive and ethical approach transforms the entire purpose of a risk assessment for security. It’s no longer just about stopping bad things from happening. It’s about creating a more transparent, fair, and resilient organizational culture where security is a shared responsibility, built on a foundation of mutual trust and respect.
Building a Culture of Continuous Risk Awareness
A security risk assessment isn’t a project you simply finish and file away. It's a living program you have to breathe every single day. The most detailed report in the world is completely worthless if it just collects dust on a shelf. The real goal is to move way beyond periodic reviews and weave risk management into the very fabric of your company culture.
This shift in mindset transforms risk awareness from an annual checklist item into a constant state of vigilance. It cultivates a proactive culture where managing risk becomes a shared responsibility, baked into everything from high-level strategic planning to daily operations. When that happens, security is no longer just another department—it’s a core business value.
Creating the Foundation for a Risk-Aware Culture
Building this kind of culture has to start at the top. Without genuine buy-in from the executive suite, any effort to promote continuous awareness will stall out. Leaders can't just sign off on the budget; they have to actively champion the importance of security as a strategic enabler for the business.
Once leadership is on board, the next move is to tear down the internal silos. A truly successful program demands seamless collaboration between departments that, let's be honest, often operate in their own separate worlds.
Human Resources: HR is central to managing insider risk, handling everything from vetting new hires to ensuring offboarding procedures promptly and completely revoke access.
IT and Security: These teams are the technical backbone, managing security controls, monitoring the systems, and responding when incidents inevitably happen.
Legal and Compliance: This group ensures every risk management activity aligns with regulatory requirements and privacy laws, shielding the organization from serious legal trouble.
Fostering this kind of cross-functional partnership ensures that the risk assessment for security is a holistic effort, not just another problem for IT to solve. It creates a unified front where different teams share crucial insights and coordinate their actions effectively.
The Role of Technology and Training
Technology is the central nervous system that makes a culture of continuous awareness possible. Modern platforms like Logical Commander’s E-Commander are designed to turn scattered data points from all these different departments into centralized, actionable intelligence. Instead of trying to piece together a story from fragmented spreadsheets, these tools provide a single source of truth for risk signals.
By translating isolated events into structured operational insight, technology empowers teams to act early and ethically. It makes risk visible, traceable, and manageable in real time, shifting the organization from a reactive to a proactive posture.
This technological foundation must be supported by consistent, engaging employee training. Security awareness can't be a one-and-done session during onboarding. Regular, relevant training keeps security top-of-mind and helps every employee recognize their personal role in protecting the organization’s most valuable assets.
By combining strong leadership, deep interdepartmental collaboration, the right technology, and ongoing education, an organization can build a genuinely resilient culture. In this kind of environment, every team member understands their contribution, turning risk management from a periodic duty into a collective, continuous mission.
Your Questions, Answered
When you're working to get a security risk assessment framework off the ground, a few key questions always come up. Let's dig into the most common ones we hear from leaders trying to move from theory to real-world practice.
How Often Should My Organization Conduct an Assessment?
While a full, deep-dive assessment should happen at least once a year, the real goal is to treat risk management as a continuous process, not a one-time event. Think of it less like an annual check-up and more like constant health monitoring for your organization.
You’ll want to trigger an immediate update whenever something significant changes—major system updates, new business operations, a novel threat on the horizon, or right after a security incident. Modern platforms can help automate this continuous monitoring, turning the risk assessment for security from a periodic chore into a living, breathing business function.
What Is the Biggest Mistake Companies Make?
By far, the most common and damaging mistake is treating risk assessment as a purely technical, IT-focused task. Walling it off in a silo creates massive—and often predictable—blind spots that adversaries are more than happy to exploit.
A genuine risk assessment has to bring together physical security, human factors, and insider risks. That means getting IT, HR, Legal, and operations in the same room to see the full picture. Ignoring the human element is a critical failure.
How Can We Assess Insider Risk Without Violating Privacy?
This is a central challenge, but it's one that modern, ethical-by-design strategies are built to solve. Instead of resorting to invasive surveillance, the focus shifts to structured, objective indicators tied to things like procedural violations, conflicts of interest, or gaps in your governance.
These systems are designed to spot risk signals without ever trying to judge a person's intent, ensuring you stay fully compliant with privacy regulations like GDPR. This approach lets your organization intervene constructively while preserving employee dignity and trust, turning a deeply complex problem into a manageable process.
Ready to move from reactive measures to proactive, ethical risk management? Logical Commander Software Ltd. provides a unified platform that centralizes risk intelligence and empowers your teams to act fast without invasive surveillance. Discover how E-Commander can transform your security culture at https://www.logicalcommander.com.
%20(2)_edited.png)
