A Modern Data Breach Response Plan Is Your Best Defense
- Marketing Team

- Oct 21, 2025
- 17 min read
Updated: Jan 15
A solid data breach response plan is your organization's crisis playbook. When an incident hits, this formal strategy guides your team through every critical step—from detection to resolution. In an era where data breaches are not a matter of if but when, a slow, chaotic response can cause catastrophic financial and reputational damage. The challenge is that most breaches involve human risk factors, making traditional, reactive plans obsolete. Logical Commander solves this by integrating ethical, AI-powered internal risk detection into your response framework. Our solutions help you Know First. Act Fast. by identifying human risk indicators before they escalate, ensuring your response is proactive, coordinated, and effective.
The High Stakes of a Breach
Let's be blunt: the financial and reputational bleeding from a data breach can be catastrophic. But the real damage often comes from a slow, chaotic response that lets the costs spiral and customer trust evaporate. Today’s threats demand more than a simple checklist; they require a proactive, well-oiled machine.
A meticulously crafted response plan is no longer a "nice-to-have." It’s a core necessity for survival. Without one, teams scramble, crucial evidence gets lost, and regulatory deadlines fly by. This leads to severe penalties and a loss of confidence that can take years to win back, if ever.
To put it into perspective, a well-rehearsed data breach response plan is often the only thing standing between a controlled incident and a business-ending catastrophe. It’s what transforms panic into process.
The Financial and Human Cost
The numbers don't lie. While the global average cost of a data breach sits at a staggering $4.44 million, that figure hides a much harsher reality in the United States. Here, a 9% surge pushed the average to a record $10.22 million.
But here’s the kicker: research shows that 60% of all breaches involved the human element, whether from an accidental click or malicious insider actions. The data also reveals a solution. Organizations that used security AI and automation were able to shut down breaches 80 days faster, saving nearly $1.9 million on average. You can dig into more of these data breach statistics on Secureframe.
This is exactly where Logical Commander’s AI-powered solutions come into play. We help you prepare and respond faster by zeroing in on the most common root cause: human risk indicators.
Actionable Insights for Proactive Defense
Building resilience isn’t about what you do during a crisis—it’s about the work you put in long before one ever happens. Here are a few practical ways to strengthen your defenses right now:
Focus on Human Capital Risk: Since most breaches start with people, you need tools that give you an early warning. Platforms like Logical Commander's **Risk-HR** use ethical, EPPA-compliant AI to spot subtle behavioral risks, giving you a chance to intervene before a mistake becomes a disaster.
Unify Cross-Departmental Workflows: A breach is a business crisis, not just an IT headache. Your response must involve Legal, HR, Compliance, and Security from the very beginning. Our **E-Commander** platform gives every department a unified dashboard, ensuring everyone is on the same page for fast, coordinated action.
Map Data and Identify Critical Assets: You can't protect what you don't know you have. Conduct a thorough data mapping exercise to identify where your most sensitive information resides. This allows you to prioritize protection efforts and understand the potential impact of a breach in specific areas.
By preparing for the human element and ensuring your teams can collaborate seamlessly, you build a response capability that is both strong and agile.
Ready to see how ethical AI can fortify your defenses? Request a demo to learn more.
Assembling Your Cross-Functional Response Team
When a data breach hits, it’s an all-hands-on-deck crisis. One of the biggest mistakes organizations make is treating it purely as an IT problem. That’s a guaranteed path to failure. The most resilient organizations understand that an effective data breach response plan is built on a unified, cross-functional team where every single member knows their role and can execute it flawlessly.
This isn't about just listing names on a document that gets filed away. It's about building a cohesive unit that can act decisively under immense pressure. Without that collaboration, even the best technical containment can be completely undermined by regulatory missteps, poor communication, or just plain internal chaos.
Defining Core Roles and Responsibilities
A well-structured team ensures every angle of the crisis is managed at the same time. While your IT and security teams are on the front lines containing the technical threat, other departments absolutely must execute their own playbooks in parallel. This coordinated effort is what separates a managed incident from a full-blown catastrophe.
Here are the key players you need at the table:
Executive Leadership: The CEO or a designated executive sponsor provides visible leadership, signs off on critical decisions, and is the final authority on major strategic moves, like public disclosure.
Team Lead/Incident Coordinator: Think of this person as the quarterback. They direct the entire response, keep communication flowing between departments, and make sure the plan is actually being followed.
IT and Security: This is your technical crew. They’re responsible for detecting, analyzing, containing, and eradicating the threat. Digital forensics and system recovery fall squarely on their shoulders.
Legal Counsel: Absolutely essential. They help you navigate the incredibly complex web of breach notification laws (like GDPR and CCPA), manage legal risks, and advise on any interactions with law enforcement.
Human Resources: HR’s role is crucial for managing all internal communications. They address employee concerns and handle any personnel issues tied to the breach, especially if it points to an insider.
Communications/Public Relations: This team crafts and controls every external message that goes out—to customers, partners, the media, and the public. Their job is to protect the organization's reputation.
Compliance: This role ensures every action you take during the response adheres to industry regulations and your own internal policies. They help prevent costly compliance failures that can come back to bite you later.
A Real-World Scenario: Employee Error Escalates
Imagine this: a well-intentioned marketing employee accidentally uploads a customer list with sensitive personal information to an unsecured, public-facing cloud server. The mistake is only discovered when a security researcher finds the data and posts about it online. Suddenly, chaos erupts.
Without a cross-functional team, the response is completely disjointed. IT scrambles to secure the server, but no one has told Legal. By the time the legal team learns about the incident from the news, critical regulatory deadlines for notification have already been missed.
Meanwhile, HR is fielding frantic questions from employees who saw the story on social media, but they have no official information to share. The communications team, caught completely off guard, issues a vague statement that only fuels more speculation and immediately erodes customer trust. This scenario underscores a key differentiator: effective response requires cross-department collaboration.
Fostering Seamless Collaboration
This is where having a unified platform becomes a game-changer. Logical Commander’s E-Commander provides cross-departmental dashboards that create a single source of truth during a crisis. Instead of fragmented email chains and confusing conference calls, every team member sees the same real-time information—from technical containment status to legal notification checklists.
This unified view enables the rapid, coordinated action needed to turn chaos into control. It ensures that when IT isolates a threat, Legal is simultaneously preparing the required notifications and HR is equipping managers with approved talking points. For a deeper look into the human factors at play, explore Your Guide to Insider Risk Management to understand how you can proactively address these risks.
By assembling a dedicated, cross-functional team and giving them the right tools, you build a response capability that is not only prepared but truly resilient. This approach embodies our core principle of cross-department collaboration, turning siloed functions into a powerful, unified defense.
The Four Pillars of an Effective Response Plan
A solid data breach response plan isn't just a checklist you dust off when things go wrong. It’s a living, four-part strategy that guides your team from the first hint of trouble all the way through to the final "all clear." Having these pillars in place prevents the knee-jerk panic that so often leads to expensive mistakes.
By breaking the response into clear phases, your teams can focus, act with purpose, and shift from a reactive scramble to a position of control. The four pillars are Detection and Analysis; Containment; Eradication and Recovery; and Post-Incident Activity. Each one builds on the last, creating a workflow that minimizes the blast radius and gets you back to business faster.
This infographic gives a great high-level view of how that process flows, from the initial alert to a secure recovery.
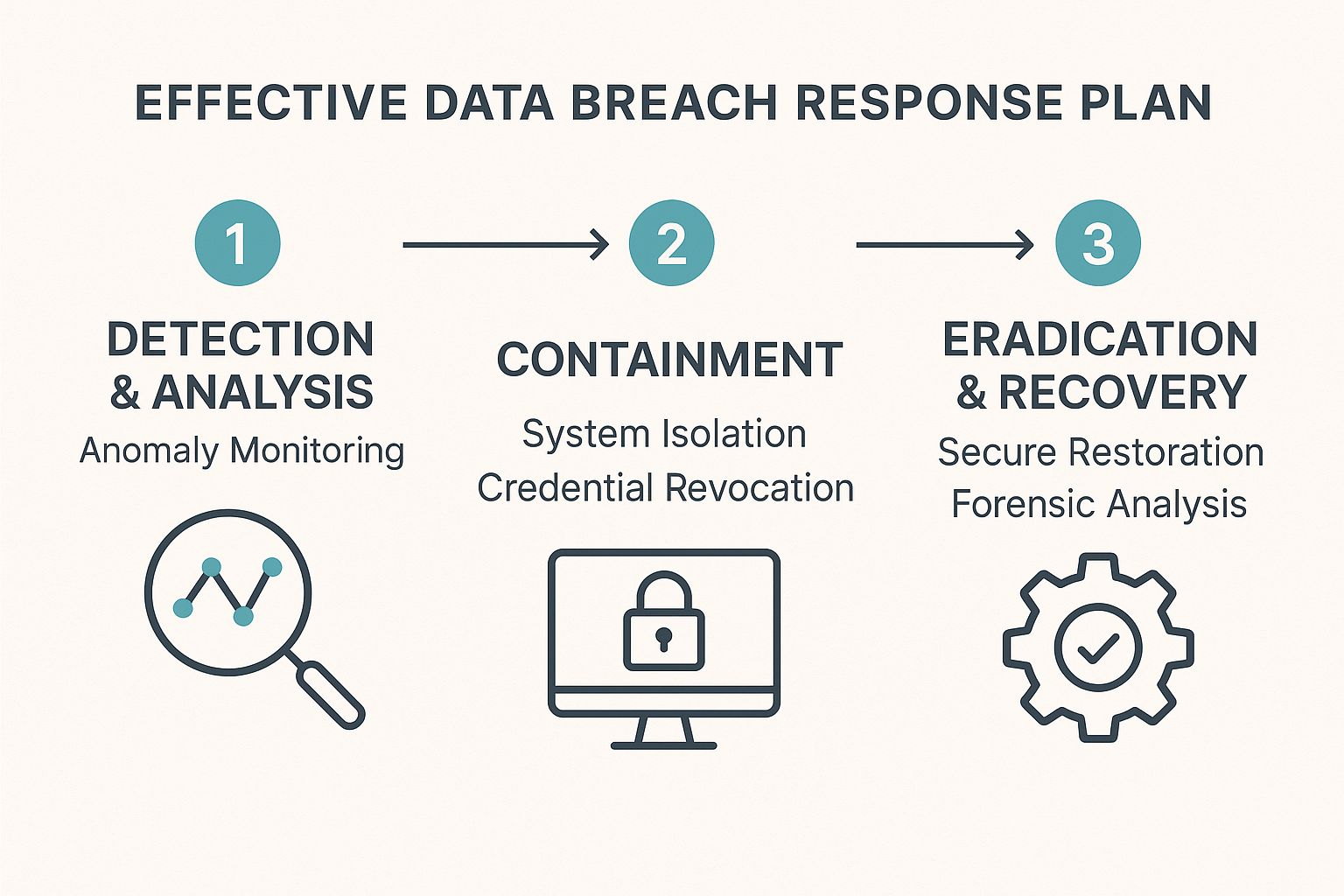
It really drives home the importance of a logical progression. Think of each pillar as a critical link in the chain—if one fails, the whole response can fall apart.
Pillar 1: Detection and Analysis
You can't fight an enemy you can't see. This first phase is where your response truly kicks off. It’s all about spotting an incident as it happens and quickly figuring out its scope, nature, and potential impact. Speed and accuracy here are everything; the first few hours of a breach often dictate the final cost and damage.
In this stage, your team is digging through alerts from security tools, connecting the dots between events, and sorting the real threats from the false alarms. You need answers to critical questions, fast: What happened? When did it start? Which systems are hit? And is our sensitive data exposed?
Actionable Insight: The single biggest hurdle here is alert fatigue. Modern security stacks can scream out thousands of alerts a day, making it dangerously easy for a real threat to get lost in the noise. To cut through it, you need a pre-defined severity matrix that ties alerts to specific business assets. This focuses your team's energy where it actually matters.
This is also where AI can be a game-changer. A solution like Logical Commander's **Risk-HR** is built to spot the subtle risk indicators in human behavior that often show up before a breach occurs. By analyzing patterns of ethical consistency and flagging anomalies, our EPPA-compliant platform can surface internal risks long before they blow up, letting you Know First. Act Fast.
Pillar 2: Containment
Once you know you’re under attack, the priority shifts immediately to containment. The mission is simple but urgent: stop the bleeding. You have to isolate the compromised systems to keep the attacker from moving laterally through your network and doing more damage.
Containment isn't a one-size-fits-all move. It's usually a mix of short-term and long-term actions. You might pull a server offline, lock out compromised user accounts, or block malicious IPs at the firewall.
Your Immediate Containment Checklist:
Isolate Affected Systems: Unplug compromised devices, servers, or entire network segments from the rest of your network.
Revoke Compromised Credentials: Immediately disable or reset passwords for any user accounts you suspect are compromised. No exceptions.
Block Malicious Connections: Push updates to your firewall rules and network access controls to block all traffic from attacker-controlled infrastructure.
Preserve Evidence: This is crucial. Take forensic images of affected systems before you wipe anything. That evidence is vital for the investigation and any potential legal action down the road.
It's a tricky balancing act. You have to be decisive enough to shut the attack down but careful enough not to trample all over the digital crime scene.
Pillar 3: Eradication and Recovery
With the threat contained, it’s time to surgically remove it from your environment. That's the Eradication phase. This involves hunting down and eliminating the root cause of the breach—whether it's malware, a hijacked account, or an unpatched vulnerability. Just restoring from a backup without closing the door the attacker used is asking for a repeat performance.
Once you’re confident the threat is gone for good, the Recovery phase begins. This is where you carefully restore affected systems and data, making sure everything is brought back online securely.
Key steps in this pillar include:
Root Cause Analysis: Get your forensics team to pinpoint exactly how the attacker got in and what they did.
Threat Removal: Delete malicious files, patch the vulnerabilities they exploited, and harden system configurations to block re-entry.
Secure Restoration: Restore your data from clean, verified backups. You absolutely have to be sure the backups themselves weren't compromised.
Validation and Monitoring: After everything is back online, watch those systems like a hawk for any sign of unusual activity. This confirms the eradication was successful.
Pillar 4: Post-Incident Activity
The fire is out, but the job isn't done. This final pillar, Post-Incident Activity, is arguably the most important for building future resilience. This is where you learn from what happened and communicate with total transparency.
Actionable Insight: Hold a "lessons learned" meeting within two weeks of the incident's resolution. Get every member of the response team in the room and have a brutally honest conversation about what worked and what didn't. The goal isn't to point fingers; it's to identify specific, actionable ways to improve your data breach response plan.
This is also where you manage all your communications—internal and external—along with any regulatory notifications and customer support. Your legal and compliance teams will be your guide here, navigating the reporting timelines required by regulations like GDPR or CCPA. How you handle this final phase has a massive impact on your company's reputation and customer trust.
By building your response around these four pillars, you create a process that's repeatable and reliable. This framework, especially when supported by ethical, privacy-first technology, transforms your organization from a potential victim into a resilient defender.
Ready to build a more proactive and resilient defense? **Request a demo** of our E-Commander platform to see how our AI-powered, cross-departmental dashboards can unify your response efforts.
How to Test and Refine Your Response Plan
A data breach response plan gathering dust on a shared drive is just a document. It only becomes a real asset when you put it under pressure. An untested plan is nothing more than a collection of assumptions, and assumptions fail spectacularly in a real crisis.
This is why testing isn't some optional follow-up. It's an essential, ongoing process that turns theory into a battle-ready strategy. The goal is simple: find the cracks in your plan before an attacker does.
Simulated exercises are where the magic happens. By walking your team through a realistic crisis, you expose communication bottlenecks, unclear lines of authority, and procedural gaps—all in a controlled, low-stakes environment.

Conducting Effective Tabletop Exercises
A tabletop exercise is a guided discussion where your response team walks through a simulated breach. This isn't about technical skill; it's about decision-making when the pressure is on.
Actionable Insight: Don't use vague scenarios. Frame your exercise around a specific, high-impact threat relevant to your industry, like a ransomware attack targeting sensitive customer data. Specific simulations produce practical, hard-hitting lessons.
Let’s run through a scenario I've seen play out dozens of times.
Real-World Scenario: A Simulated Ransomware Attack
Imagine it's 2 AM on a Saturday. Your CISO gets an alert. Multiple critical servers are encrypted, and a ransom note is demanding a seven-figure payment in crypto. The clock is officially ticking.
The facilitator kicks things off and starts probing the team:
Initial Activation: Who is the very first person the CISO calls? Is their contact info right there in the plan and up-to-date? What if they don't answer—who's the backup?
Team Assembly: How fast can the full team (IT, Legal, HR, Comms) get on a call? Does everyone know what their first move should be? Honestly, the first failure point is often just getting the right people on a conference bridge.
Decision-Making Authority: The CEO, now awake, asks the big question: "Are we paying?" Who actually has the authority to make that call? Does Legal have external counsel on speed dial to advise on the massive ramifications of paying up?
As the scenario unfolds, the facilitator throws in a curveball. The attackers now claim they stole sensitive HR data and are threatening to leak it. Suddenly, HR and Legal are in the hot seat. Do they know the specific notification rules for employee data under GDPR or CPRA?
This is where a plan's weaknesses become painfully obvious. Maybe Communications drafts a public statement, but Legal hasn't seen it, creating internal friction. Or maybe IT successfully isolates the infected network but forgets to preserve forensic evidence, crippling the investigation before it even starts.
From Simulation to Refinement
The real work begins after the exercise. A detailed post-mortem is where you turn those painful observations into real improvements.
Key Takeaway: The goal of a tabletop exercise isn't to "win." It's to learn. Document every single friction point, every moment of confusion, and every procedural gap. These failures are the raw material for building a stronger, more resilient data breach response plan.
The Qantas Airways breach is a stark reminder of why this matters. When hackers released the personal details of 5.7 million customers, the airline's response went far beyond just technical recovery. They had to manage investigations, provide 24/7 support, and offer identity protection, proving a modern plan has to account for long-term customer fallout.
Integrating Technology for Realistic Drills
To make these drills even more powerful, integrate real-time data from your security tools. During an exercise, you can use dashboards from a platform like E-Commander to simulate the actual flow of information. This trains your team to interpret what they would see in a live incident and act on it fast.
Actionable Insight: Use technology to measure your response. During the exercise, track key metrics like Time to Assemble, Time to Contain, and Time to Notify. This shows the measurable ROI of a well-tested plan by proving how practice slashes containment time and costs. To make sure your proactive measures are truly battle-ready, consider the importance of regular effective disaster recovery plan testing.
For companies seeking specialized guidance, our PartnerLC network includes seasoned professionals who can facilitate these drills. They bring an objective, outside perspective to help you find and fix weaknesses you might have missed. Refining your plan is a continuous loop—test, learn, and improve. That's how you build true cyber resilience.
The Role of AI in Modern Incident Response
Let's be honest: traditional incident response often feels like you're playing catch-up. An alert fires, and your team is left scrambling to piece together what happened after the damage is done. A modern data breach response plan has to flip this script, shifting from a reactive firefight to a proactive strategy. The engine driving that change? Ethical AI.
AI-powered platforms completely change the game. They analyze immense datasets in real time, picking up on the subtle risk indicators and anomalous patterns that human teams, no matter how skilled, would almost certainly miss. This is how your organization can finally move from just reacting to breaches to actually preempting them.

This gets to the heart of our philosophy: Know First. Act Fast. Instead of waiting for a catastrophic failure, you can identify and shut down risks at their earliest, most manageable stages.
From Manual Analysis To Real-Time Detection
The core advantage of AI is its sheer speed and scale, something humans just can't match. While your security teams are drowning in alert fatigue, an AI system can correlate thousands of disparate data points to find that one, meaningful signal hidden in the noise.
This is especially critical for spotting internal risks. Take the recent Mars Hydro breach, which exposed a staggering 2.7 billion records. The root cause was a simple, misconfigured database—a perfect example of how easily systemic security failures can lead to massive exposure. You can get more insights on how basic oversights can cause major breaches from PKWARE's analysis. While AI isn't a magic wand for configuration errors, it excels at detecting the unusual activity that almost always follows such an oversight.
At Logical Commander, our platform is built on a few key differentiators that set our approach apart:
Ethical & Non-intrusive AI: Our system is fully EPPA-compliant. It focuses on risk indicators and ethical consistency, not invasive employee surveillance.
Privacy-First Design: We are ISO 27001/27701 certified and operate under strict GDPR and CPRA principles. Your data is always handled responsibly.
Real-Time Detection and Measurable ROI: Our AI doesn't just look at past events. It delivers live signals that enable immediate intervention, giving you a clear and quantifiable return on investment by reducing incident response times and costs.
How AI Stacks Up: A Quick Comparison
To really see the difference, it helps to put the old and new approaches side-by-side. The table below shows how AI and automation dramatically improve each stage of the incident response lifecycle, turning slow, manual processes into fast, efficient actions.
Response Stage | Traditional Approach (Manual) | AI-Powered Approach (Logical Commander) |
|---|---|---|
Preparation | Static plans, periodic manual risk assessments. | Dynamic risk modeling, continuous threat intelligence updates. |
Detection | Relies on signature-based alerts, often leading to high false positives. | Real-time anomaly detection, behavioral analysis spots novel threats. |
Analysis | Analysts manually correlate logs and data from multiple systems. | Automated correlation of thousands of data points, surfaces root cause faster. |
Containment | Manual steps to isolate systems, often slow and prone to error. | Automated orchestration to isolate affected assets in seconds. |
Eradication | Manual removal of malware and patching of vulnerabilities. | Guided remediation and automated patch deployment. |
Recovery | Manual system restoration from backups. | Orchestrated recovery processes to minimize downtime. |
Post-Incident | Manual report generation, lessons learned meetings. | Automated incident reporting, AI-driven insights for future prevention. |
As you can see, the AI-powered approach doesn't just do the same things faster—it enables a fundamentally smarter and more effective response at every single step.
A Scenario: Spotting A Sophisticated Insider Threat
Imagine a disgruntled employee is planning to steal sensitive intellectual property. They're smart. They won't download thousands of files at once, because that would trigger every alarm in the building. Instead, they play the long game.
Over weeks, they access a few files here and email a small document to a personal account there. They slightly alter their login times. Each action, on its own, is minor—small enough to fly completely under the radar of traditional security tools.
An AI-driven platform, however, sees the bigger picture. It recognizes this "low-and-slow" pattern as a significant deviation from the employee’s normal baseline. It correlates these subtle actions into a clear signal of an emerging threat, allowing HR and Security to step in before any real data loss occurs.
This is the power of proactive, AI-driven risk management. For a deeper dive, check out our guide on detecting insider threats with Ethical AI.
Actionable Insights For Your Response Plan
Bringing AI into your incident response isn't just about plugging in new technology; it's about shifting your mindset.
Shift Focus to Pre-Incident Indicators: Your plan needs to evolve. Update it to include processes for responding to AI-driven alerts about potential human risks, not just technical exploits. This means getting HR and Compliance involved much earlier in the process.
Use AI to Augment Your Team: Let your AI tools handle the initial triage and analysis of alerts. This frees up your security analysts to focus their expertise on high-priority, validated threats, which helps reduce burnout and dramatically speeds up containment.
Our E-Commander platform provides the cross-departmental dashboards needed to make this collaboration seamless. When an AI-driven alert is raised, you can be sure the right people can act on it immediately.
Your Blueprint for Cyber Resilience
Your data breach response plan is a living system that needs the right technology, people, and processes working in harmony to be effective. In today’s threat landscape, a proactive strategy enhanced with ethical AI is the new standard for resilience. This is about preventing a crisis, not just reacting to one. The key is integrating privacy-first solutions that address the human element before it becomes a liability. Don’t wait for a breach to expose your weaknesses. Protect your organization with the leader in AI-powered internal risk management.
Request a demo of E-Commander today.
Know First. Act Fast. Ethical AI for Integrity, Compliance, and Human Dignity.
Common Questions About Data Breach Response Plans
When you're in the weeds building a data breach response plan, a few questions always come up. Getting these right is often the difference between a plan that just sits on a shelf and one that actually works when you need it most.
How Often Should We Really Test Our Plan?
Look, a plan is only as good as its last test. As a rule of thumb, you should run through tabletop exercises at least once a year. For the more intense, full-scale simulations that really put your team through its paces, aim for every 18–24 months.
But here's the critical part most people miss: your data breach response plan is a living document. It's not a one-and-done project. Any time something big changes in your business—you bring in a major new technology, key people on the response team leave or join, or new regulations hit your industry—you need to update and re-test immediately. Don't wait for the annual review.
What's the Biggest Mistake People Make in Their Response Plans?
Easy. The single biggest point of failure I see is a plan that lives in an IT silo. A purely technical plan is doomed.
I've seen it happen: the tech team does a brilliant job containing the breach, but the company's response is a complete disaster. Why? Because they failed to build in genuine cross-departmental collaboration from the very beginning. Without Legal, HR, and Communications looped in from minute one, you're guaranteed to miss regulatory notification deadlines, send confusing and damaging messages to employees, and burn through customer trust you might never get back.
A response plan has to be a business-wide strategy, not just an IT checklist. If it isn't, it will fail.
Can AI Actually Help with Breaches Caused by Human Error?
Absolutely, but it has to be the right kind of AI. The goal isn't surveillance; it's proactive support.
This is where ethical AI platforms like Logical Commander's **Risk-HR** come in. They're designed to spot subtle behavioral patterns that often show up before a human-error breach happens. Think of employees who might need more training on security protocols, or others who are showing signs of disengagement or distraction that could lead to a careless mistake.
By flagging these human capital risks early, the AI gives you a chance to intervene in a positive way—with more training, better support, or a simple conversation. It’s about preventing the mistake from ever being made, which is always the best way to strengthen your first line of defense.
%20(2)_edited.png)
