Insider Threat Detection Software A Practical Explainer
- Marketing Team

- Dec 21, 2025
- 15 min read
Updated: Dec 22, 2025
Insider threat detection software is, at its heart, a specialized security tool built to watch over an organization's digital environment from the inside. It’s designed to spot and flag behaviors that just don't fit the normal patterns of your employees, contractors, and partners—the people who already have legitimate keys to the kingdom. Its entire job is to protect your most sensitive information from being misused or stolen by those you trust.
Understanding Your Internal Security Blind Spots
Think of your company’s security as a medieval fortress. You've spent a fortune on high walls (firewalls) and sharp-eyed gatekeepers (antivirus software) to keep invaders out. But what happens when the threat isn't storming the gates? What if it's a trusted knight already inside the walls?
This is precisely where insider threat detection software comes in. It’s your watchtower crew, the ones who know the daily rhythm of the entire castle. They know which blacksmiths are supposed to be in the armory, which scribes handle royal scrolls, and the hours they typically keep.
By establishing this baseline of normal, everyday activity, the software can instantly spot when something’s wrong—like a guard trying to sneak into the royal treasury in the middle of the night. It's this deep, contextual understanding that separates it from tools that only watch the perimeter.
And make no mistake, this isn't some theoretical problem. Insider threats, whether they're born from malice or simple mistakes, are a huge driver of security breaches. In fact, studies show they're behind as many as 34% of all incidents in major markets. The growing awareness of this vulnerability is why the global insider threat protection market hit USD 3.81 billion in 2022 and is climbing fast. You can explore the full market analysis on insider threat trends to really grasp the scale of this challenge.
The Three Faces of Insider Risk
Insider threats aren't a monolith; they come in a few distinct flavors. Each is driven by completely different motivations and circumstances. Getting a handle on these types is the first real step toward building a defense that actually works.
Here’s a quick breakdown to help you distinguish between the different kinds of internal threats you might face.
Threat Type | Primary Driver | Example Scenario |
|---|---|---|
The Malicious Insider | Intentional Harm (Revenge, financial gain, espionage) | A disgruntled developer who was just fired downloads proprietary source code to sell to a competitor on their way out. |
The Accidental Leaker | Unintentional Mistake (Carelessness, lack of training) | A well-meaning HR employee accidentally emails a spreadsheet with every employee's salary to the entire company instead of just the finance team. |
The Compromised User | External Attack (Stolen credentials, phishing) | A cybercriminal steals an accountant's login details through a phishing scam, then uses their access to wire funds to an offshore account. |
While it’s easy to focus on the drama of a malicious insider, the sheer volume of accidental and compromised incidents makes them an equally urgent problem for any modern organization.
Breaking it down further, here’s what each type looks like in the real world:
The Malicious Insider: This is the classic villain—a disgruntled employee or contractor who abuses their access on purpose. They might be seeking revenge, looking for personal financial gain, or even engaging in corporate espionage. Think of someone stealing intellectual property to sell or deliberately sabotaging a critical system out of spite.
The Accidental Leaker: This is the well-meaning but careless employee. They’re not trying to cause harm, but their actions still lead to a data breach. They might accidentally email a sensitive client list to the wrong person, lose a company laptop, or click on a phishing link that unleashes malware.
The Compromised User: This person is an unwilling pawn in someone else's game. An external attacker has stolen their credentials and is now masquerading as a legitimate employee. From the system's perspective, their initial actions look completely normal, allowing the attacker to move through the network undetected to steal data or escalate their privileges.
The greatest danger is often the one you don't expect. While malicious insiders cause direct harm, the sheer volume of accidental and compromised incidents makes them an equally pressing concern for modern organizations.
How Modern Detection Software Works
Think of modern insider threat detection software like a credit card fraud prevention system. Your bank knows your typical spending habits—where you shop, how much you spend, and when. If a strange charge suddenly appears from another country, they flag it instantly.
These security platforms do the same thing, but for digital activity. They learn the normal rhythm of a workday, tracking who accesses which files, when emails are sent, and what applications people use.
At the heart of these systems is User and Entity Behavior Analytics (UEBA). It’s a sophisticated approach that builds a baseline of normal behavior for every individual and group, which becomes the benchmark for spotting dangerous anomalies.
Key Detection Approaches
When someone's actions deviate from their personal baseline—like an HR manager suddenly trying to download sensitive accounting records for the first time—machine learning algorithms flag the event immediately. This is far more effective than old-school methods that just scanned for keywords, which often led to a flood of false alarms.
UEBA uses statistical models to tell the difference between a minor change in routine and a genuine threat. It analyzes network traffic to spot unusual data transfers and monitors file access for irregular downloads or copies from sensitive folders.
Here’s how it breaks down:
Behavior Analytics constantly observes user actions to build a reliable picture of what’s normal.
Statistical Modeling automatically adjusts risk thresholds as workflows and behaviors naturally evolve.
Machine Learning gets smarter over time, refining risk scores based on data from past incidents.
Risk Scoring assigns a numerical value to each flagged event, helping security teams prioritize the most severe alerts first.
Many of the advanced techniques used here are also powerful in tackling other security challenges, like using algorithms for AI fraud detection.
The moment behavior drifts too far from the norm, security teams get a real-time alert. This shifts the entire security posture from being reactive to proactive, giving teams a chance to stop a threat before real damage is done.
Want a deeper dive into how these models learn and improve their accuracy? Check out our guide on behavioral analytics platforms.
Visualizing Insider Threat Types
It’s important to remember that not all insider threats are the same. This map breaks them down into three main categories: malicious, accidental, and compromised. Each one has different motivations and, therefore, requires different signals to detect them effectively.
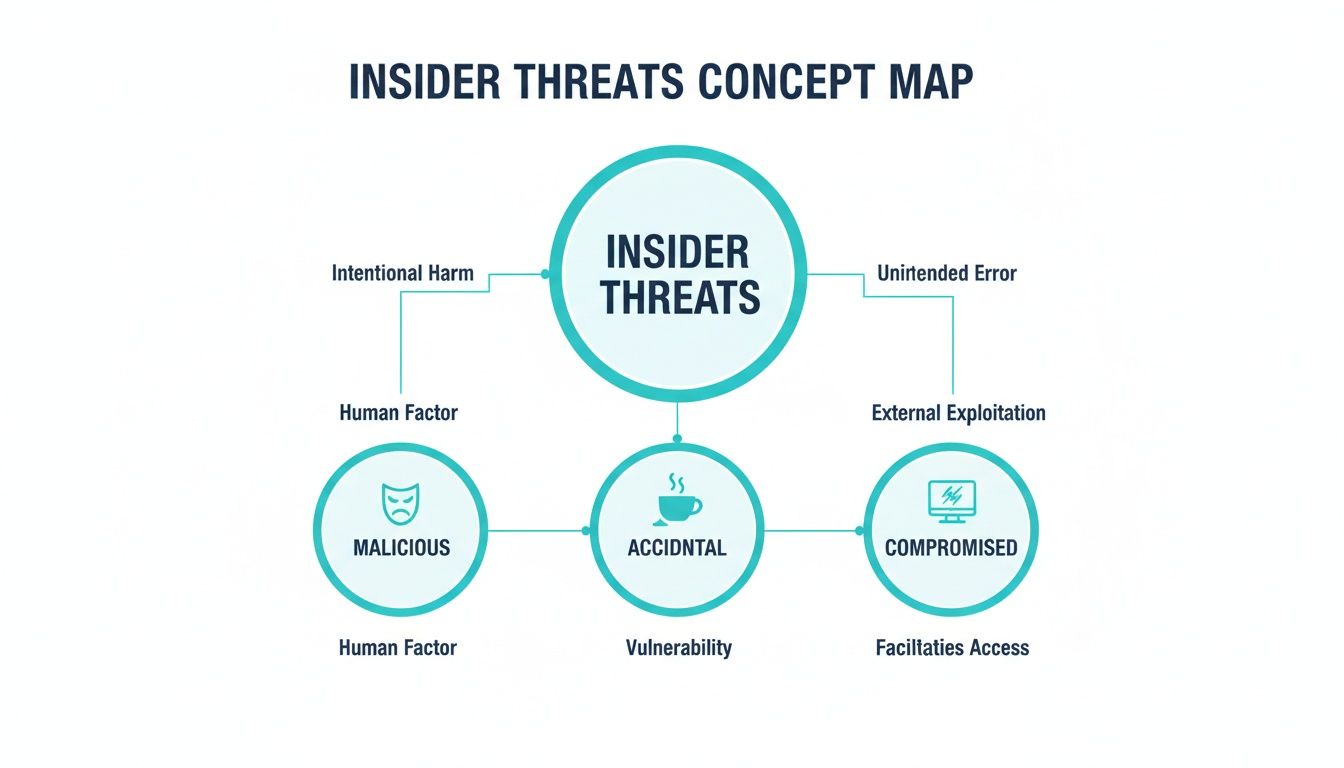
This distinction is crucial. The signs of a disgruntled employee intentionally stealing data look very different from an employee who accidentally clicks on a phishing link. A smart detection system has to be tuned to spot both.
Navigating Privacy and Building Trust

When you roll out any kind of monitoring software, you immediately hit a critical question: how do you protect the company without making your employees feel like they’re constantly being watched? That line between security and surveillance can feel razor-thin. If you cross it, you risk creating a culture of suspicion that poisons morale and actually makes you less secure.
The only way to get this right is to build your insider risk strategy on a foundation of transparency, ethics, and a deep respect for privacy.
This isn’t just a feel-good culture issue; it’s a legal minefield. Regulations like GDPR in Europe and CCPA in California have incredibly strict rules about how you can collect and process employee data. A single misstep can lead to crippling fines and a PR nightmare, making compliance a non-negotiable part of the plan.
Differentiating Security from Surveillance
Let’s be clear: the goal of modern insider threat detection software isn’t to spy on people. It's to protect sensitive company data by understanding how it’s being used.
Think of it like a security guard at a museum. The guard’s job isn’t to listen to every visitor's private conversations. Their job is to protect the priceless art. They only pay attention when someone gets too close to a painting or tries to enter a restricted area. The focus is on the interaction with the asset, not the person.
That’s the exact principle behind an ethical program. It shifts the focus from monitoring people to monitoring data.
Surveillance-Based Tools (The Old Way): These tools often use keystroke logging, screen recording, or email scanning. This approach is incredibly intrusive, captures a ton of personal information, and makes employees feel like Big Brother is always watching.
Ethical-by-Design Tools (The New Standard): These platforms focus on metadata and context. They track which user account accessed a sensitive file, when they did it, and from where—without ever reading the content of their personal messages. You get the security signals you need without blowing up privacy.
Adopting an ethical-by-design tool aligns your security goals with a culture of trust. For a deeper dive into the legal specifics, understanding privacy considerations is essential before you implement any system.
Building Trust Through Transparency
The most effective insider risk programs are the ones employees actually understand and support. Secrecy just breeds fear and resentment. Transparency, on the other hand, creates a shared sense of responsibility for keeping the organization safe.
Fostering a culture of trust is not just a 'nice to have'—it is a powerful security measure in itself. When employees feel respected and see themselves as partners in protecting the organization, they are more likely to follow security protocols and report suspicious activity.
Your usage policies need to be written in plain English, not dense legalese. Every single employee should know exactly what’s being monitored, why it's being monitored, and how that data is used to protect both the company and their own jobs. This clarity kills ambiguity and shows your people that you respect them.
To explore this topic further, you can find valuable insights on detecting insider threats with ethical AI, which highlights a prevention-focused model.
Ultimately, a well-designed program proves that security and privacy aren't enemies. By choosing the right tools and communicating with total honesty, you can build a system that’s both incredibly effective at stopping risk and deeply respectful of the people who make your business run.
How to Choose the Right Software
Picking the right insider threat detection software feels like a high-stakes decision, because it is. You're not just buying a tool; you're bringing in a new capability to protect your company's crown jewels. With a market full of vendors all claiming to have the magic bullet, you need a clear, methodical way to cut through the noise and find what actually works for your business.
The first move is to look past the flashy dashboards and get to the heart of the matter: the detection engine. How smart are its behavioral analytics? A truly effective solution goes way beyond simple, rigid rules. It uses machine learning to build a living, breathing baseline of what’s normal for every user, which is the only way to spot the subtle shifts in behavior that signal a real threat—instead of just drowning your security team in false alarms.
Define Your Core Requirements
Before you even agree to a vendor demo, you need a crystal-clear picture of what you actually need the software to do. A solid set of requirements will be your north star, making sure you pick a platform that solves your real-world problems, not just one that looks good in a presentation.
Start by asking a few fundamental questions:
What are we actually trying to protect? Is it your intellectual property, customer PII, or critical financial data? Knowing what matters most dictates the level of scrutiny you’ll need.
What’s already in our security stack? The right tool has to play nice with your existing systems, like your SIEM or Identity and Access Management (IAM) platforms. Seamless integration creates a unified defense, not another data silo.
Where will this live? Do you need an on-premise solution for total control, a cloud-based platform for flexibility, or a hybrid model that gives you a bit of both?
Answering these questions honestly will help you build a shortlist of vendors that are a genuine fit. For a more detailed framework, you can explore our complete guide to insider risk management.
Compare Different Detection Approaches
Not all insider threat platforms are created equal. Far from it. Understanding the deep philosophical and technical differences between them is the key to making a choice that aligns with your company's values, especially around employee privacy.
The market for these tools is expanding fast. Analysts predict the Insider Threat Management Software market will hit $2.5 billion in 2025 and climb all the way to $8 billion by 2033. This growth is being driven by cloud platforms and AI analytics that claim to predict risky behaviors with 85-90% accuracy. You can read more about these market projections and technology trends to get a feel for the landscape.
To help make sense of it all, here's a look at the main detection methods you'll come across.
Comparison of Insider Threat Detection Approaches
The way a platform identifies threats says everything about its philosophy. Some are built like digital watchtowers, while others focus on protecting the data itself. This table breaks down the core differences so you can see what aligns with your organization's risk appetite and culture.
Detection Approach | Primary Focus | Pros | Cons | Best For |
|---|---|---|---|---|
Traditional DLP | Data in motion/at rest | Great for stopping known data patterns (like credit card numbers) from leaving the network. | Lacks user context, triggers tons of false positives, and can be frustratingly rigid. | Organizations with highly structured data and strict compliance needs. |
UEBA (Surveillance) | User activity monitoring | Powerful for spotting anomalous behavior by tracking nearly everything a user does. | Can feel invasive, erode employee trust, and raises major privacy red flags. | Environments where deep user monitoring is a non-negotiable security requirement. |
Ethical-by-Design | Data interaction & policy | Protects data without personal surveillance; built to align with privacy laws like GDPR. | Requires clear policy definition upfront; focuses on prevention over pure reaction. | Companies that want to build a culture of trust while preventing data loss. |
Ultimately, the goal is to choose a method that not only secures your assets but also reinforces the type of work environment you want to foster.
The best choice isn’t always the one with the most features. It's the one that most effectively reduces your specific risks while reinforcing the culture of trust you want to build.
Ask Vendors the Tough Questions
Once you’ve got a shortlist, it's time to put vendors on the spot. Your goal is to understand not just what the software does, but how it does it. A vendor’s answers about their data collection methods and ethical framework will tell you everything you need to know.
Get a list of pointed questions ready for every demo. Make sure to include these:
What specific data do you collect, and where is it stored?
How does your platform tell the difference between an accidental mistake and malicious intent?
Can you show me exactly how your system helps us comply with GDPR, CCPA, and other privacy laws?
What’s the typical false positive rate, and what tools do you provide to help us tune it down?
Choosing your insider threat detection software is a critical move that will shape your security posture for years. By focusing on your core needs, comparing the different methodologies, and asking direct questions, you can find a partner that protects your assets and respects your people.
Best Practices for a Successful Rollout

Buying insider threat detection software is a big step, but it’s just the first one. The real value isn't in the software itself—it's in the strength of the program you build around it. A successful rollout is less like flipping a switch and more like weaving a new capability into the fabric of your organization’s culture and security operations.
This requires a strategic, people-first approach that turns a technical tool into a shared responsibility. Without a clear plan, even the most advanced software will fall flat, leading to confusion, poor adoption, and missed threats. A great rollout is a deliberate process designed to build momentum, prove value, and earn trust from day one.
Secure Executive Buy-In and Form a Cross-Functional Team
Before you even think about installing a single agent, your first move is to get unwavering support from the top. This isn't just about getting the budget signed off. You need a champion in the executive suite who can broadcast the program's importance from the highest level. That kind of backing sends a clear signal: managing insider risk is a core business priority, not just another IT project.
With that support locked in, it's time to build your team. Insider risk isn’t a problem you can solve from a security silo. To really succeed, you need a coalition of leaders who bring different perspectives and authority to the table.
Your core implementation team should have a seat for representatives from:
Human Resources to make sure the program aligns with employee policies and helps foster a positive work culture.
Legal and Compliance to navigate the maze of privacy laws and ensure every action is ethical and legally defensible.
IT and Security to handle the technical deployment, integrations, and the day-to-day management of alerts.
Department Leaders from high-risk areas like finance or R&D, who can provide the crucial operational context that turns data into insight.
This collaborative structure ensures decisions are balanced, policies are practical, and the program is built on a foundation of shared ownership.
Develop Clear Incident Response Playbooks
An alert from your new software is just a signal. It's what you do next that really counts. Without a clear, documented plan, security teams can stumble, leading to inconsistent responses, lost evidence, or even legal missteps. Incident response playbooks are your roadmaps for turning a digital alert into a decisive, structured investigation.
These playbooks need to outline the exact steps for different types of alerts, from accidental data exposure to suspected malicious activity. They answer the tough questions before a crisis hits: Who gets notified? What's the protocol for preserving evidence? At what point do you bring in HR or Legal?
A well-defined playbook removes guesswork when the pressure is on. It ensures every incident is handled consistently and fairly, protecting both the organization and the employee's rights. It’s what turns potential chaos into a controlled process.
Start with a Phased Deployment
Trying to deploy the software to the entire organization at once is a recipe for disaster. A phased rollout, starting with a smaller pilot group, is a much smarter play. This approach lets you work out any technical kinks, fine-tune alert settings, and gather real-world feedback in a controlled environment.
Start with a single department that handles sensitive data or has a higher risk profile. This focused deployment helps you score some early wins and build a powerful case study for the rest of the company. Success in the pilot phase creates momentum, making it much easier to get broader buy-in for the full rollout.
Finally, remember that training isn't a one-and-done event. It's not just for the security team learning the new software. Every employee needs to understand the program’s purpose and their role in keeping the organization secure. Continuous education fosters a culture of security awareness, turning every employee into a partner in protecting your most valuable assets.
The Future of Insider Risk Management
The whole conversation around insider risk is finally changing. For years, the default strategy was reactive—just setting up digital tripwires and waiting for an employee to stumble across one. But that old model, built on a foundation of surveillance-style monitoring, often created more problems than it solved. It buried security teams in an avalanche of false positives and bred a toxic culture of distrust by treating every employee like a potential suspect.
That entire approach is becoming obsolete. The future of managing insider risk isn't about catching people making mistakes; it's about preventing those mistakes from ever happening. This proactive philosophy marks a massive shift, moving away from a defensive crouch and toward a strategy of genuine enablement.
Prevention Over Surveillance
Modern insider threat detection software is being completely reimagined through an ethical-by-design lens. Instead of casting a wide surveillance net that vacuums up every keystroke and email, these forward-thinking platforms zero in on the interaction between users and sensitive data. The goal is no longer to watch people, but to protect information where it lives.
This new generation of tools is built on a principle of prevention. They help organizations set up clear, enforceable data handling policies and give employees real-time guidance right when they need it. For instance, if an employee tries dragging a sensitive file to an unsanctioned cloud drive, the system simply blocks the action and displays a pop-up explaining the policy. No drama, no investigation—just a simple, preventative guardrail.
The most effective security strategy is one that empowers people to do the right thing. By shifting from reactive surveillance to proactive prevention, organizations can build a resilient security culture based on trust, transparency, and shared responsibility.
Building a Culture of Trust and Compliance
This ethical approach does more than just stop data leaks; it builds a healthier and more secure organizational culture. When your teams understand that the security tools are there to help them protect company assets—not to spy on them—they become active partners in the security program.
This proactive, non-invasive model is also essential for navigating the tangled web of global privacy regulations. With mandates like GDPR and CCPA setting such a high bar for data protection, an ethical-by-design system is no longer a "nice-to-have." It’s a core requirement for proving compliance and respecting the fundamental rights of your employees.
Ultimately, the future of insider risk management lies in this more humane and far more effective strategy. It’s a call to action for leaders to find solutions that secure the organization's most valuable data while championing the dignity of its people.
Your Questions, Answered
When you're looking at solutions for insider risk, you’re bound to have questions. Let's dig into some of the most common ones we hear from decision-makers trying to get ahead of threats without creating a culture of distrust.
How Is This Different From Antivirus Or Firewalls?
Think of your security like protecting a castle. Your antivirus and firewalls are the high walls, the moat, and the gatekeepers. Their entire job is to stop external attackers—the invading army—from ever getting inside. They’re built to block known malware and unauthorized entry from the outside world.
An insider threat detection software, on the other hand, works like the royal guard inside the castle walls. It assumes people already have legitimate access. Its job is to spot when a trusted person—a knight, a courtier—does something highly unusual, like trying to access the treasury in the middle of the night. It focuses on internal behavior, not external attacks.
Will This Software Hurt Employee Morale?
This is a critical question, and the answer comes down to your approach. If you secretly deploy invasive, surveillance-style tools that monitor your team's every move, you will absolutely shatter trust and create a culture of suspicion.
However, an ethical approach built on transparency does the opposite.
When you're open with your team about why you’re implementing a program—explaining the goal is to protect sensitive company data, not spy on people—it fosters a sense of shared responsibility. The key is choosing an ethical-by-design tool that focuses on risky data interactions, not personal activity. A transparent, respectful program actually reinforces a culture of integrity.
How Should a Small Business Get Started?
For a small business, jumping straight into buying software isn't the right first step. The most powerful thing you can do is build a solid foundation.
Start by identifying your crown jewels. What information would be most damaging to the business if it were leaked or stolen? Once you know what you need to protect, create simple, clear data usage policies that every single employee can understand. This initial step costs very little, provides immense clarity, and is the highest-impact way to start managing insider risk before you ever look at a tool.
At Logical Commander Software Ltd., we believe security and trust go hand-in-hand. Our E-Commander platform offers an ethical-by-design approach to prevent insider risks without invasive surveillance, helping you protect your organization while respecting your people. Know first and act fast by exploring our solutions at https://www.logicalcommander.com.
%20(2)_edited.png)
