A Practical Guide to Regulatory Compliance Risk Management
- Marketing Team

- Dec 17, 2025
- 17 min read
Regulatory compliance risk management is the structured process of finding, analyzing, and dealing with potential losses that come from not following laws, regulations, and internal standards. This isn't just about avoiding fines; it’s a core strategic function that protects a company’s reputation, keeps operations running smoothly, and secures its future.
Navigating the Complex World of Regulatory Compliance Risk
Think of your company as a large ship sailing through treacherous waters. The open ocean is your market, but it’s full of hidden reefs (regulations), shifting sandbars (new rules), and unpredictable tides (changing enforcement). Without a skilled navigator and a reliable map, you’re just asking to run aground, facing expensive repairs and losing the trust of your passengers and crew.
This is the very essence of regulatory compliance risk management. It’s the disciplined art and science of charting a safe course through a complex legal sea.
It is absolutely not a passive, "check-the-box" chore that gets pawned off on the legal department. Instead, it's a dynamic, forward-looking business function that is essential for survival and success. A failure here can trigger severe consequences that go far beyond a simple financial penalty.
The True Cost of Non-Compliance
When you overlook compliance risk, the impact ripples through every part of the business, creating a domino effect of negative outcomes:
Financial Penalties: These are the most obvious costs, with fines that can easily run into the millions or even billions of dollars, depending on the violation.
Reputational Damage: In an age of instant information, a single compliance failure can destroy customer trust, brand loyalty, and public goodwill—assets that take decades to build and only moments to lose.
Operational Disruption: Regulatory investigations or sanctions can grind business operations to a halt, freeze assets, or force costly overhauls to core processes, leading to significant downtime and lost revenue.
Legal and Remediation Expenses: The costs tied to legal battles, internal investigations, and implementing corrective actions can be absolutely massive.
A crucial part of navigating this world involves understanding data privacy policies. These aren't just legal documents; they are a public promise to handle data ethically, which is a cornerstone of modern rules like GDPR and CCPA.
The Four Pillars of Compliance Risk Management
To build a solid program, you need to focus on four core pillars. Each one serves a distinct function but works together to create a resilient and defensible framework that protects the entire organization.
Pillar | Core Function | Business Impact |
|---|---|---|
Identification | Proactively discovering and cataloging potential compliance risks across all business units and processes. | Prevents blind spots and ensures that emerging regulatory threats are spotted before they become major issues. |
Assessment | Analyzing the likelihood and potential impact of each identified risk to prioritize mitigation efforts. | Focuses resources on the most critical threats, avoiding wasted effort on low-impact compliance issues. |
Mitigation & Controls | Designing and implementing policies, procedures, and controls to reduce or eliminate identified risks. | Creates a defensible system that actively prevents violations and demonstrates due diligence to regulators. |
Monitoring & Reporting | Continuously tracking the effectiveness of controls and providing clear, actionable reports to leadership. | Ensures the compliance program remains effective over time and gives decision-makers the visibility they need. |
Together, these pillars transform compliance from a reactive, defensive chore into a proactive, strategic function that strengthens the entire business.
A Roadmap for Mastery
An effective compliance risk management program turns this potential liability into a real strategic advantage. By building a robust framework, your organization can operate with confidence, innovate more freely, and build deeper, more meaningful trust with every stakeholder.
This guide will give you a clear roadmap, starting with the foundational principles and moving all the way to advanced strategies and the technology that powers them. We’ll explore the complete compliance lifecycle—from spotting risks to putting controls in place and making the most of modern tools. This journey will arm you with the practical knowledge to turn regulatory hurdles into opportunities for building a more resilient and ethical company.
Let's begin by charting the course.
The Five Stages of the Compliance Risk Management Lifecycle
Effective regulatory compliance risk management isn't a one-and-done task; it’s a living, breathing cycle. Think of it like a captain steering a ship through unpredictable seas. The captain is constantly scanning the horizon for storms (identification), judging their severity (assessment), adjusting the sails (mitigation), watching the radar for new developments (monitoring), and updating fleet command on the ship's status (reporting).
In the same way, your organization needs to navigate the five distinct stages of the compliance lifecycle to stay on a safe and strategic course. This structured approach is what transforms compliance from a reactive fire drill into a predictable, manageable, and genuinely value-driven function.
Let's walk through each stage, using the example of a fintech company getting ready to launch a new mobile payment app.
Stage 1: Identification — Finding the Hidden Risks
The first step is all about proactive reconnaissance. You have to find potential compliance risks before they find you. This is the discovery phase, where you map out every single process, system, and business activity that might bump up against a regulation. It means asking tough questions about every corner of the business.
For our fintech app, this goes way beyond the obvious.
Data Handling: How are we collecting, storing, and processing customer data? Are our practices fully aligned with GDPR or CCPA?
Financial Transactions: Are we buttoned up on Anti-Money Laundering (AML) and Know Your Customer (KYC) regulations?
Marketing Claims: Are our advertisements truthful and not misleading under consumer protection laws?
App Security: Does our code meet the cybersecurity standards demanded by financial regulators?
This process results in a comprehensive inventory of potential risks, which becomes the foundation for the entire lifecycle.
Stage 2: Assessment — Prioritizing What Matters Most
Once you’ve identified a list of risks, you can’t tackle them all at once with the same intensity. That would be a huge waste of resources. The assessment stage is all about smart prioritization. Here, you analyze each risk based on two critical factors: its likelihood of happening and its potential impact on the business if it does.
This is often visualized with a risk matrix, a simple but powerful tool that helps you separate minor headaches from company-ending disasters. For our fintech, a small bug in the app's user interface has a low impact. But a failure in the KYC verification process? That’s highly likely to attract regulatory heat and carries a massive financial and reputational punch. It’s an immediate top priority.
This simple flow chart captures the core stages of managing identified risks.
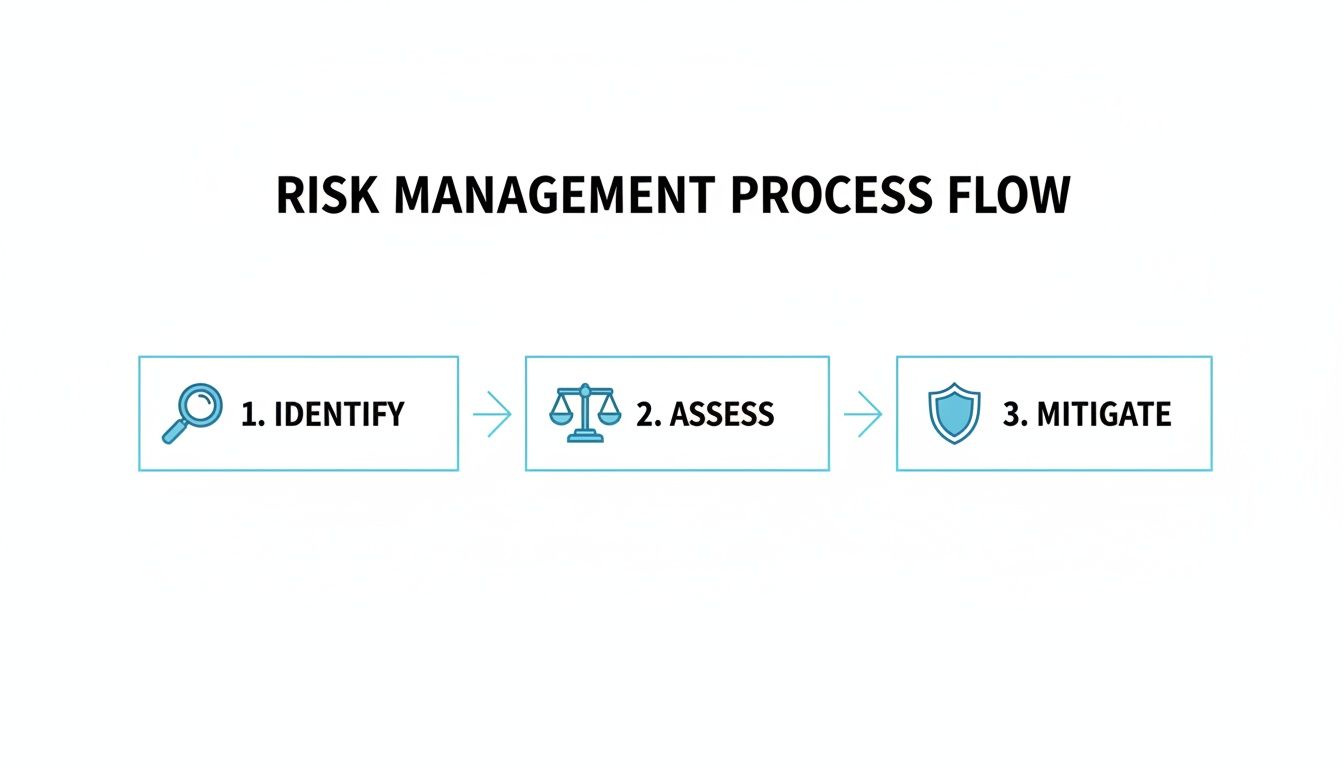
This highlights how effective risk management is a disciplined journey from discovery to action. To go deeper on this crucial second stage, check out our complete guide on conducting a thorough compliance risk assessment.
Stage 3: Mitigation — Implementing Protective Controls
With your risks properly prioritized, the next stage is mitigation—the part where you actually do something to reduce the likelihood or impact of each risk. This is where you design and implement controls, which are the specific policies, procedures, and technical safeguards that form your defensive line.
For the high-priority KYC risk in our fintech app, mitigation controls might look something like this:
Automated ID Verification: Implementing a third-party tool to automatically verify government-issued IDs.
Mandatory Training: Requiring all customer-facing staff to complete annual AML and KYC training.
Regular Audits: Conducting quarterly internal audits of the verification process to catch errors early.
These controls are the practical, on-the-ground actions that turn your risk management strategy into a reality.
Stage 4: Monitoring — Keeping a Watchful Eye
Regulations change, business processes evolve, and new threats are always emerging. The monitoring stage ensures your compliance program doesn't collect dust and become irrelevant. It involves continuously tracking the effectiveness of your controls and scanning the horizon for new regulatory developments.
This is no longer a purely manual effort. In fact, regulatory compliance has shifted from a cost center to a strategic function powered by technology. PwC’s 2025 Global Compliance Survey found that 49% of organizations use technology for 11 or more compliance activities, with top use cases being training (82%), risk assessment (76%), and transaction monitoring (75%).
For our fintech, this means using automated alerts to flag suspicious transaction patterns and subscribing to regulatory update services to stay ahead of new laws. It’s about keeping your finger on the pulse.
Stage 5: Reporting — Communicating with Stakeholders
The final stage is reporting, which is all about communication. This involves clearly articulating your organization's risk posture, the effectiveness of your controls, and any compliance incidents to key stakeholders. This audience can range from the board of directors and executive leadership to auditors and external regulators.
Clear, accurate, and timely reporting is what builds trust and demonstrates due diligence. For the fintech, this would include a quarterly risk report for the board, detailed audit trails for regulators, and immediate incident reports if a data breach occurs. This closes the loop, providing the crucial feedback needed to refine the risk identification process and begin the cycle all over again.
Laying the Foundation: Essential Frameworks and Controls for a Bulletproof Program
Knowing the lifecycle of compliance risk is one thing, but a process is only as strong as its foundation. To build a program that can actually withstand regulatory pressure and real-world threats, you need a proven blueprint—an established framework that provides the scaffolding for all your policies and procedures.
Think of it like building a skyscraper. You wouldn't just start stacking steel beams and hope for the best. You’d start with a detailed architectural plan to ensure every single component works together to create a stable, resilient structure. Compliance frameworks serve that exact purpose for your risk management program.
These aren't meant to be rigid, one-size-fits-all rulebooks. They’re guiding principles and best practices that you adapt to your organization's specific size, industry, and risk profile.
Choosing Your Architectural Blueprint
While tons of specialized frameworks exist, a few globally recognized standards provide an excellent foundation for any regulatory compliance risk management program. They give you a common language and a structured approach that regulators and auditors immediately understand and respect.
Two of the most influential are:
COSO Framework: Developed by the Committee of Sponsoring Organizations of the Treadway Commission, COSO is the gold standard for internal controls, risk management, and fraud deterrence. It’s a robust model for establishing solid governance and ethical oversight.
ISO 31000: This standard from the International Organization for Standardization offers a more universal set of guidelines for managing risk across any type of organization. Its big push is to weave risk management into every single business activity and decision.
Adopting a framework like COSO or ISO 31000 ensures your program is comprehensive, consistent, and—most importantly—defensible when it’s under a microscope.
The Three Lines of Defense
With your blueprint in hand, the next step is implementing controls. These are the specific mechanisms that bring your risk mitigation strategies to life. Think of them as the safety systems in your skyscraper—from fire sprinklers to reinforced windows. They aren't all the same; each one serves a different purpose at a different time.
The best way to understand controls is to group them into three distinct types. Each plays a vital role in protecting your organization.
"A mature compliance program doesn’t just react to problems; it anticipates them. The strategic layering of preventive, detective, and corrective controls is what separates a truly resilient organization from one that is merely compliant on paper."
This layered approach creates a defense-in-depth strategy. If one control fails, another is waiting to catch the issue.
Preventive, Detective, and Corrective Controls
1. Preventive Controls (The Guardrails)These are proactive measures designed to stop a compliance issue from ever happening. Their entire goal is to prevent errors or misconduct before any harm can be done.
Example: Implementing multi-factor authentication (MFA) to access sensitive customer data. This control stops an unauthorized user from ever getting in.
Example: Requiring mandatory pre-approval for all high-value financial transactions. This prevents an improper payment before it's even made.
2. Detective Controls (The Alarm System)These controls are built to identify and report on compliance issues after they’ve occurred. They won’t stop the initial event, but they give you the critical alert you need to respond quickly.
Example: Running daily audit logs that flag unusual access patterns to a critical database. The log doesn’t block the access, but it tells the security team a potential breach is happening.
Example: Conducting regular, unannounced financial audits to uncover fraudulent activities that slipped past your preventive controls.
3. Corrective Controls (The Response Team)Once a detective control sounds the alarm, these are the actions you take to fix the issue, remediate the damage, and stop it from happening again.
Example: Activating an incident response plan the moment a data breach is detected. This plan outlines the exact steps to contain the breach, notify affected parties, and restore systems.
Example: Updating a flawed internal policy and retraining employees after an audit uncovers a recurring compliance error.
By strategically weaving these three control types together, you create a dynamic and resilient system. For a practical guide on getting your controls ready for scrutiny, this comprehensive audit preparation checklist is a fantastic resource. A well-architected program doesn’t just pass audits; it builds lasting organizational integrity.
Common Challenges and How to Overcome Them
Even the sharpest regulatory compliance risk management program is going to hit some friction. Real-world operations are messy, and a few predictable hurdles can easily knock your efforts off track if you’re not ready for them. Let’s move past the theory and tackle these common challenges head-on with some proven strategies.
These aren't unique problems; they’re the most frequent points of failure we see in compliance programs across every industry. By getting ahead of them, you can build a far more resilient and effective system from the start.
Ditching Persistent Manual Processes
One of the biggest drags on any compliance program is a stubborn reliance on manual workflows. We’ve all seen it: the endless spreadsheets, the confusing email chains, and the paper checklists that are not just inefficient but are magnets for human error. A single misplaced decimal or a forgotten follow-up can easily snowball into a major compliance breach.
The fix isn't just about buying software; it's about making a rock-solid business case for automation. You have to focus the argument on tangible returns: lower error rates, faster audit prep, and freeing up your people for higher-value work. This reframes automation from a line-item cost into a direct investment in operational horsepower and risk reduction.
It’s an interesting paradox. Even as regulatory pressure seems to be cooling off in some areas, manual processes are still a huge source of risk. Research from Wolters Kluwer noted a drop in the “concern index” among U.S. lenders from 117 in 2023 to a projected 88 in 2025. But here’s the kicker: the same study found that 88% of respondents still use manual methods, calling them the single biggest obstacle to effective compliance. You can find more on this trend in the full regulatory and risk management survey.
Securing Adequate Budget and Resources
Let's be honest—compliance is often viewed as a cost center, a necessary evil that doesn't bring in revenue. That makes it a tough sell when budgets are being decided. To get the resources you need, you have to learn to speak the language of the business: risk and money.
Stop asking for a "compliance budget" and start presenting a risk-mitigation plan. Frame every request around specific, quantifiable outcomes.
Action: Calculate the potential cost of a data breach in your industry, including both the fines and the brand damage.
Action: Pitch your budget request as a small fraction of that potential loss—it’s an insurance policy against a catastrophic event.
Action: Tie your compliance initiatives directly to business goals, like breaking into new markets that have strict regulatory hurdles.
This simple shift changes the entire conversation from an expense to a strategic investment.
Keeping Pace with Rapid Regulatory Change
The regulatory world never sits still. New laws get passed, old ones are updated, and what regulators care about this year might be different next year. Trying to keep up with all of this manually is a surefire way to fall behind.
This is where technology isn’t just nice to have; it’s essential. Subscribing to regulatory intelligence feeds and using "horizon scanning" tools can put the whole monitoring process on autopilot. These services track changes from regulatory bodies all over the world and shoot you alerts tailored to your industry and where you do business.
The goal isn't just to react to new rules, but to see them coming. A proactive stance gives you time to adapt your controls and policies thoughtfully instead of scrambling to catch up after a new regulation is already on the books.
Fostering a True Culture of Compliance
At the end of the day, the toughest hurdle is often cultural. A compliance program is completely useless if employees see it as just another annoying obstacle getting in the way of their "real" jobs. For any of this to work, compliance has to be baked into the organization's DNA until it becomes a shared responsibility.
This means going way beyond those boring, click-through annual training modules. Think about more practical tactics to build a genuine compliance culture:
Gamified Training: Use interactive scenarios and quizzes that make learning engaging and sticky.
Leadership Buy-In: Make sure executives are consistently talking about the importance of compliance in their communications and, more importantly, in their actions.
Integrated Metrics: Weave compliance-related goals into performance reviews for key roles.
Clear Reporting Channels: Set up and promote a safe, anonymous way for employees to flag potential issues without any fear of blowback.
When everyone from the C-suite to the front lines understands their role in managing regulatory risk, compliance stops being a departmental chore and becomes a powerful organizational value.
Choosing and Implementing Compliance Technology Wisely
Let's be clear: in modern regulatory compliance, technology is no longer a "nice-to-have." It's the engine of survival. Trying to keep up with the sheer volume and speed of regulatory change using manual spreadsheets and checklists is a recipe for failure. It's slow, riddled with human error, and simply can't compete.
The right technology stack transforms compliance from a reactive cost center into a proactive, intelligent business function. But choosing those tools requires a thoughtful, strategic approach. A poorly chosen platform can create more chaos than it solves, locking you into clunky workflows or, worse, giving you a false sense of security. The goal is to find solutions that fit your organization’s unique risk profile and operational DNA like a glove.
Key Categories of Compliance Technology
The market for compliance tools is crowded, but most solutions fall into a few core buckets. Understanding what each one does is the first step toward building a tech stack that actually works for you.
GRC Platforms (Governance, Risk, and Compliance): Think of these as the central nervous system of your entire compliance program. A solid GRC platform gives you a single hub to manage policies, run risk assessments, map your internal controls to specific regulations, and generate the reports that leadership and auditors demand. It provides that crucial, holistic view of your entire risk landscape.
Automated Monitoring Tools: This category is all about specialized software built for specific, high-volume tasks. This includes things like transaction monitoring tools for anti-money laundering (AML) or horizon scanning platforms that automatically track and flag new regulatory updates from around the world before they catch you by surprise.
Policy Management Software: These tools are designed to streamline the entire lifecycle of your internal policies. They handle everything from creation and approval workflows to distribution, employee sign-offs (attestation), and scheduled reviews, ensuring everyone is always working from the most current and approved playbook.
The Rise of AI and RegTech
The biggest shift in compliance technology right now is the move toward Artificial Intelligence (AI), often called RegTech (Regulatory Technology). These tools go way beyond simple automation. They use machine learning to chew through massive datasets, spot subtle patterns, and predict potential risks before they ever blow up into a crisis. An AI-powered tool, for instance, can analyze thousands of communications to flag language that points to potential misconduct, sending an alert for human review.
This isn't a future trend; it's happening right now. A recent Moody’s survey found that AI adoption for risk and compliance shot up from around 30% in 2023 to a projected 50% by 2025. But this rapid adoption comes with a huge warning sign: the governance to manage this technology often lags way behind. Many companies are still wrestling with major concerns about AI accuracy, data privacy, and the lack of strong internal oversight. You can review the full findings of Moody's 2025 AI survey for more details.
The core lesson here is that technology is a powerful force multiplier, but it is not a substitute for sound judgment and strong governance. The most effective programs combine advanced tools with clear, human-led oversight and ethical principles.
A Practical Process for Technology Selection
Picking the right platform is a critical decision, not something to rush. Following a structured process will save you from expensive mistakes down the road.
Define Your Requirements: Before you even look at a single vendor, map out your specific pain points and goals. Are you drowning in manual risk assessments? Do you need a better, more defensible audit trail? Get it all down on paper and create a list of your absolute must-have features.
Assess Potential Vendors: Create a shortlist of vendors and stack them up against your requirements. Look past the flashy marketing claims. Insist on live demos, check real customer reviews, and verify their security and compliance certifications.
Plan a Phased Rollout: Whatever you do, avoid a "big bang" implementation where you flip the switch for everyone at once. Start with a smaller pilot program in a single department to work out the kinks and build momentum. A phased approach guarantees a much smoother adoption and minimizes operational disruption.
A huge piece of this puzzle is choosing tools built with privacy and ethics at their core. Platforms like E-Commander are specifically designed to provide those crucial early risk signals without resorting to invasive surveillance, ensuring your compliance program is both effective and auditable. For a curated list of top-tier platforms, check out our guide on the best compliance risk management software. This approach ensures your technology strengthens your ethical posture, rather than creating new complications.
Building a Lasting Culture of Compliance

Ultimately, even the best frameworks, controls, and technology are only half the battle. A truly resilient regulatory compliance risk management program is powered by people. The real goal is to build a culture where compliance stops being a siloed department and becomes a shared, organization-wide responsibility.
This isn’t something you can achieve with a once-a-year training module. It demands a deliberate, ongoing effort to weave ethical conduct and risk awareness right into the company’s DNA. When compliance is seen as everyone’s job, your entire organization becomes the first line of defense.
Turning Compliance into a Core Value
To build this kind of culture, you need to focus on two things: clear accountability and open communication. The "three lines of defense" model is a powerful way to structure this, assigning specific risk ownership to operational management, the risk and compliance functions, and internal audit. It creates unmistakable lines of responsibility.
Forget the passive presentations. Training has to be continuous, engaging, and directly relevant to what your employees do every single day. Think interactive scenarios and real-world case studies that make the consequences of non-compliance feel tangible.
The most critical component is creating a safe environment for employees to raise concerns without fear of retaliation. When people feel secure reporting potential issues, you gain invaluable early warnings that automated systems might miss.
Establishing transparent and accessible reporting channels is foundational. Organizations can learn more about fostering this environment by understanding the principles of a Speak Up Culture, which encourages proactive communication from the ground up.
Let's circle back to our ship analogy. A strong compliance culture is the skilled and vigilant crew. They’re the ones who spot the subtle changes in the water, adjust the sails proactively, and work together to keep the vessel safe. This transforms compliance from a regulatory burden into a sustainable competitive advantage, ensuring the ship not only weathers the storm but sails stronger because of it.
Your Questions, Answered
Even with a solid strategy, a few key questions always pop up when putting a regulatory compliance program into action. Let's tackle some of the most common ones we hear from leaders trying to get this right.
What Is the Difference Between Risk and Compliance?
It’s easy to use these terms interchangeably, but they represent two very different functions. Think of it this way: compliance is about following the rules. It’s the act of adhering to specific laws, regulations, and standards that apply to your business.
Risk management is a much broader discipline. It’s the strategic process of identifying, assessing, and neutralizing any potential threat to the organization—and the risk of non-compliance is just one of those threats.
Compliance asks, "Are we following Rule X?" Risk management asks, "What’s the real-world damage if we fail to follow Rule X, and what other icebergs are out there that we don't see?" The best programs don’t treat them as separate. They use risk assessment to figure out which compliance efforts matter most.
How Often Should We Conduct a Risk Assessment?
There's no magic number, but a risk assessment should never be a "one-and-done" exercise filed away in a cabinet. The business landscape changes too quickly for that. As a general rule of thumb, you should perform a comprehensive assessment at least annually.
That said, certain events should immediately trigger a fresh review. You can’t wait a year if something big changes. Plan for an assessment whenever you experience:
Major Regulatory Shifts: New laws like the GDPR or CCPA coming into force.
New Business Ventures: Launching a new product line or expanding into a new country.
Significant Incidents: A data breach, a major compliance failure, or a near-miss.
System or Process Overhauls: Implementing new core technologies or fundamentally changing how you operate.
Who Is Ultimately Responsible for Compliance Risk?
While your compliance department will lead the charge, the ultimate responsibility for regulatory compliance risk management sits with the board of directors and senior leadership. They are the ones who set the tone from the top and are accountable for ensuring an effective program is in place and properly resourced.
But operational ownership is everyone’s job. Every single employee who handles sensitive data, talks to a customer, or manages a financial transaction has a daily role in managing compliance risk.
A strong compliance culture makes sure this sense of accountability is felt at every level of the organization, not just in the C-suite. This distributed ownership is what separates a mature, resilient program from a simple box-checking exercise.
An effective regulatory compliance program requires a new approach that protects both the institution and the individual. Logical Commander Software Ltd. enables ethical, proactive risk management by identifying early signals of misconduct without invasive surveillance, preserving dignity and privacy. See how our AI-driven platform can help you build a compliant, auditable, and ethical workplace at https://www.logicalcommander.com.
%20(2)_edited.png)
