A Guide to Proactive Internal Threats Assessments
- Marketing Team

- Oct 22, 2025
- 13 min read
Updated: Dec 24, 2025
For too long, companies have treated internal threats assessments as a reactive measure—a painful cleanup operation following a data breach or compliance failure. This reactive mindset is not just costly and disruptive; it's a fundamental business liability. A modern assessment flips the script entirely. It's not a technical audit or a hunt for "bad employees"; it's a strategic necessity for proactively defending your revenue, reputation, and regulatory standing.
Shifting From Reactive Investigations to Proactive Prevention

Few scenarios are more damaging for a business leader than the aftermath of an insider incident. The traditional response—a cumbersome forensic investigation—drains resources, erodes employee morale, and ultimately confirms what you already suspected: sensitive data has been compromised, and compliance has been breached.
This old model is fundamentally broken because it focuses on assigning blame after the fact instead of fortifying the systemic weaknesses that allowed the incident to occur. Reports consistently show that a significant percentage of insider incidents are caused by simple negligence—mistakes, carelessness, or a momentary lapse in judgment, not malicious intent. This reveals a massive disconnect. If the problem is often systemic, the solution must be preventive and systemic, too.
The True Cost of Waiting
Relying on reactive investigations traps you in a cycle of predictable risk and escalating costs. Each breach is treated as a one-off event, leaving underlying operational gaps wide open for the next incident. This approach is financially unsustainable and operationally disruptive. To grasp the full business impact, it's crucial to understand the true cost of reactive investigations and why prevention is the only viable strategy.
A forward-thinking internal threats assessment is not about intrusive employee surveillance. It’s about understanding the weak points in your organization's most fundamental components:
Processes: Where do workflows lack the necessary checks and balances, creating opportunities for error or exploitation?
Controls: Are access rights and security protocols configured correctly and consistently enforced, or do they exist only on paper?
Training: Do employees truly understand their security and compliance obligations, or is it a forgotten annual exercise?
By focusing on why an incident could happen, rather than just who might cause it, you build organizational resilience from the ground up. This preventive posture strengthens corporate governance and protects the entire enterprise.
This guide outlines how an ethical, proactive approach to risk management identifies these vulnerabilities before they can be exploited. It establishes a new standard for managing human-factor risk—one that is EPPA-aligned, reinforces a culture of security, and protects your organization from the inside out.
What Internal Threats Assessments Really Mean
Let's clarify a critical point: a modern internal threats assessment is not about policing your team or fostering a culture of distrust. Far from it. Think of it as a structural integrity analysis for the human element of your business—the most critical component of your security posture.
Imagine your organization is a complex bridge. A traditional, reactive investigation is what happens after a collapse. Investigators sift through the wreckage to find the single point of failure. A proactive assessment, in contrast, is the engineering inspection that happens while the bridge is fully operational. It’s designed to spot stress points, areas of wear, and design flaws long before they lead to a catastrophic failure. The goal is not to blame a single component but to strengthen the entire structure.
These assessments systematically uncover the "why" behind human-factor risks like data exfiltration, compliance breaches, and fraud. They identify gaps in your company’s operational DNA—the workflows, training protocols, and access controls that create opportunities for incidents, whether accidental or intentional.
Shifting Focus From Individuals To Systems
A common misconception is that these assessments are designed to identify "risky" employees. The reality is that the vast majority of insider incidents stem from non-malicious negligence. This points to a critical truth: the problem is often systemic, not personal.
A modern assessment zeroes in on fundamental systemic questions:
Process Vulnerabilities: Are there workflows with insufficient oversight that invite exploitation?
Access Control Gaps: Do certain roles have permissions so broad they create an outsized risk profile, even if those permissions are not required for daily tasks?
Training Deficiencies: Is your security training effective and regularly reinforced, or is it a check-the-box exercise that fails to impact behavior?
By focusing here, you move away from a reactive, blame-focused model and start building genuine organizational resilience. For a deeper dive into these principles, this guide on modern banking risk assessment offers a valuable framework.
Reactive Investigations vs. Proactive Assessments
The strategic and financial advantages of a proactive approach become clear when compared to legacy, after-the-fact investigations. The objective is to prevent damage entirely, not merely document it post-mortem.
Here’s how the two models compare:
Aspect | Reactive Investigations | Proactive Assessments |
|---|---|---|
Timing | Post-incident, after the damage has already occurred. | Pre-incident, with a sharp focus on prevention. |
Objective | Assign blame and contain immediate fallout. | Identify and mitigate systemic vulnerabilities to prevent future incidents. |
Cost | Extremely high (legal fees, fines, remediation, reputational damage). | A controlled, predictable operational expense that reduces liability. |
Impact on Morale | Negative; fosters a culture of distrust and fear. | Positive; reinforces a culture of shared security ownership and trust. |
Business Impact | Disruptive, halting operations and diverting resources. | Strategic, integrating seamlessly into risk management and governance. |
As you can see, the difference is night and day.
Ultimately, an effective internal threats assessment provides a clear, actionable roadmap of your human-related vulnerabilities. It empowers leadership to allocate resources strategically to fix foundational weaknesses—long before they can be exploited. This protects both the organization and its people in an ethical, EPPA-aligned way.
A Framework for Modern Internal Threats Assessments
An effective internal threats assessment is not a vague exercise. It is a structured analysis built on a practical and repeatable framework. This allows organizations to systematically deconstruct human-factor risk without resorting to intrusive or unethical methods.
This modern framework is built on three core pillars: People, Processes, and Technology.
By evaluating these three interconnected areas, leadership gains a holistic view of where systemic vulnerabilities exist. The approach shifts focus from scrutinizing individuals to strengthening the organizational structures that guide their actions. The goal is to build resilience, not to assign blame.
This infographic illustrates how these three pillars support a preventive security objective.
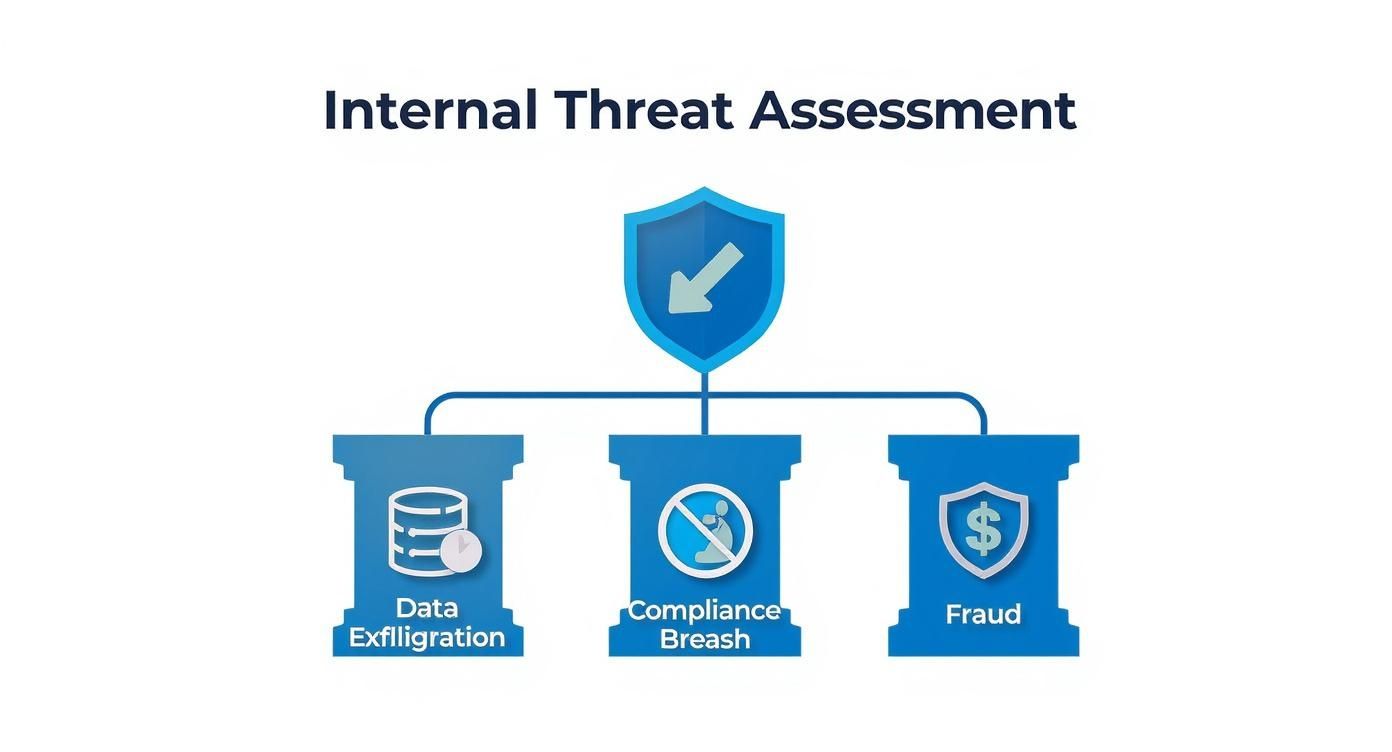
As you can see, a unified security concept is broken down into manageable pillars. Each one addresses a distinct area of potential risk, such as data exfiltration or fraud, providing a clear path to mitigation.
Pillar 1: People
The People pillar is often the most misunderstood. In a modern, EPPA-compliant framework, this is not about evaluating an employee's character or intentions. Instead, it’s a risk-based analysis of roles, responsibilities, access levels, and permissions. The assessment answers critical, objective questions.
For example, does an employee in finance really need administrator-level access to the entire customer database? Or was that permission a holdover from a previous role? This pillar is about spotting systemic risks created by mismatched permissions and responsibilities.
An ethical, AI-driven platform provides significant advantages here. It can flag that 75% of users in a department have excessive system permissions that are rarely, if ever, used. This is not a judgment on any individual; it is a clear indicator of a systemic risk—a vulnerability waiting to be exploited, accidentally or intentionally. The solution is simple and preventive: right-size access controls based on the principle of least privilege.
Pillar 2: Processes
The second pillar, Processes, examines the workflows and security protocols that govern daily operations. Even with the best team and technology, flawed or outdated processes can create significant gaps an insider could easily exploit. Think of this part of the internal threats assessment as reviewing the blueprints of your operational security.
Here, the focus is on identifying choke points, blind spots, and procedural inconsistencies. Key areas to evaluate include:
Data Handling Protocols: How is sensitive data managed, transferred, and destroyed? Are procedures clear and consistently followed?
Onboarding and Offboarding: Are access rights granted promptly upon hiring and, more importantly, revoked immediately upon termination? Lingering "ghost" accounts are a common and dangerous vulnerability.
Change Management: When systems are updated or roles change, are there formal processes to review and adjust access permissions accordingly?
A process gap, like a lack of dual authorization for large financial transfers, is a silent threat. It creates an opportunity that exists regardless of who is in that role, making it a prime target for preventive controls.
Pillar 3: Technology
The third pillar is Technology. This involves assessing how your security tools, controls, and platforms align with your human workflows. Technology is not a silver bullet; if it's poorly configured or creates excessive friction, employees will find ways to circumvent it, creating new risks.
This assessment evaluates whether your security stack supports your goals or inadvertently creates vulnerabilities. For instance, if a data loss prevention (DLP) tool is so restrictive it impedes legitimate business activities, employees might resort to unauthorized personal devices or third-party cloud services. Suddenly, you have a shadow IT problem that undermines your security posture.
The key is to ensure your technological controls are practical and integrated into how people actually work. This pillar analyzes the real-world effectiveness of your security infrastructure in the context of human behavior, ensuring your technology investments deliver genuine risk reduction.
Together, these three pillars provide a comprehensive, actionable, and ethical framework for any modern internal threats assessment.
Using AI for Ethical and Effective Risk Detection

Traditional internal threats assessments suffer from a critical flaw: they are often a snapshot in time—a periodic review that is outdated the moment it's completed. Modern technology changes this dynamic, transforming a static checklist into a continuous, near-real-time risk management function.
Artificial intelligence provides the capability to analyze vast amounts of operational data without being invasive. An ethical, AI-driven platform focuses on impersonal, systemic patterns by analyzing data points generated by day-to-day business operations—it is not a surveillance tool.
This reinforces technology's proper role: it's an objective tool for fixing systemic problems, not a magnifying glass for scrutinizing individuals. The goal is to identify and mitigate organizational vulnerabilities before they can be exploited.
How AI Pinpoints Systemic Risk Without Surveillance
An AI-powered system can identify subtle anomalies in operational data that are invisible to human teams. It connects seemingly unrelated events to reveal weaknesses in processes or controls. It’s all about the what and the how, not the who.
Consider these real-world examples:
Process Deviations: An AI platform might notice that a critical security protocol, like dual authorization for large financial transfers, is consistently bypassed by an entire department. This isn't about blaming one person; it’s a clear indicator that a process is broken or that the team requires better training.
Access Control Gaps: It could flag that a group of employees in a non-technical role are repeatedly accessing a sensitive development server late at night. The system flags this as an operational risk based on their roles and typical work hours, prompting a necessary review of access controls.
Data Movement Anomalies: The AI could detect an unusual pattern of large data transfers from a secure internal server to a less-secure endpoint. Even if initiated by an authorized user, the pattern itself highlights a potential data handling policy that needs reinforcement.
By focusing on these systemic indicators, security and HR teams can stop chasing countless false positives from legacy tools. Instead, they can dedicate their time to fixing broken workflows and strengthening controls—addressing the root cause of the risk.
The Growing Need for Advanced Internal Security
The need for smarter internal security is becoming more urgent, especially as new technologies are adopted at lightning speed. The 2025 Thales Data Threat Report highlights this, with 69% of respondents identifying the fast-moving tech ecosystem as their biggest concern regarding GenAI security risks. As companies integrate these powerful tools, the potential for internal vulnerabilities multiplies, making AI-driven assessments a critical component of governance.
This proactive, data-driven approach is fully aligned with EPPA principles. It avoids any form of lie detection or psychological evaluation, focusing strictly on objective, operational data. You can learn more about this ethical approach in our guide on detecting insider threats with ethical AI.
Ultimately, AI-driven internal threats assessments offer a scalable, ethical, and highly effective way to manage human-factor risk. They give organizations the power to continuously monitor their risk posture, pinpoint vulnerabilities with precision, and implement preventive measures that strengthen the entire enterprise. It's an approach that protects both the organization and its people by building a culture of security based on sound processes, not suspicion.
Connecting Internal Gaps to Global Security Challenges
It's a mistake to view internal vulnerabilities as isolated problems—a weak password policy here, a gap in access controls there. In reality, those small, internal gaps are the very entry points that sophisticated external threat actors actively seek.
An oversight in internal security can become a gateway for state-sponsored groups or transnational criminal organizations. This elevates an internal threats assessment from a routine compliance task to a critical pillar of your overall security strategy. These adversaries consistently seek the path of least resistance, which often leads directly through your people and processes.
Whether it involves a malicious employee or a negligent one, an insider can become the vector for a major security incident. A single compromised credential or an unmonitored data transfer is all it takes for an external group to gain a foothold. This is the hard business case for robust internal assessments; they are your first and best line of defense.
When Internal Weaknesses Meet External Threats
The link between internal gaps and external exploitation is not theoretical. The 2025 Annual Threat Assessment from the U.S. Intelligence Community makes it clear that criminal and terrorist groups are adept at exploiting systemic weaknesses. The same logic applies to corporate security—that internal control gap is precisely the opening an adversary needs. You can read the full official U.S. intelligence community assessment to understand these persistent risks.
Strengthening your internal security is not just about protecting your assets. It’s about ensuring your organization does not become the weak link in a larger security chain.
Consider these common scenarios:
Data Exfiltration for Foreign Entities: An insider—either coerced or acting willingly—steals intellectual property that ends up in the hands of a foreign competitor or government.
Exploitation by Criminal Syndicates: A gap in financial controls is identified and exploited by a criminal organization to launder money, using an unsuspecting employee as cover.
Unintentional Access: A careless employee clicks a phishing link, allowing an external threat actor to bypass perimeter defenses and gain access to your network.
Proactively identifying and closing these internal vulnerabilities is a direct and powerful way to reduce your organization's attractiveness as a target for external adversaries.
Building Resilience with a Global Mindset
To counter these blended threats, you must adopt a security mindset that connects internal controls to global risks. This means fully integrating your internal threats assessments with your broader security and compliance frameworks.
Viewing internal risk through this lens transforms the function from a simple compliance task to a strategic security operation. Understanding how your internal processes measure up against global standards is a critical piece of this puzzle. You can learn more about this in our guide on ISO 27001 and AI-powered risk detection.
Every vulnerability you close internally makes your organization—and the entire ecosystem it operates in—safer and more resilient.
Linking Cyber Vulnerabilities to Financial Impact
An internal threats assessment is not just an IT exercise; it is one of the most powerful tools for protecting your company’s bottom line. Too often, conversations about internal risk remain focused on technical protocols, overlooking the direct, tangible financial impact of getting it wrong.
Every internal weakness, whether it's inconsistent credential management or outdated access controls, is a potential trigger for a massively expensive cyber attack. These are not minor gaps; they are the vectors that lead to devastating ransomware and data breach incidents. The line is frighteningly direct: a preventable internal mistake creates the opening, and a sophisticated attacker walks right through.
The fallout is not a theoretical risk. It’s a painful cascade of regulatory fines, protracted legal battles, and reputational damage that can cripple a business.
From Small Gaps to Catastrophic Costs
Think of your internal controls as the locks on your digital doors. An employee with unnecessary permissions is like leaving a master key under the doormat. A weak password policy is like using a flimsy lock anyone can pick. These aren't just technical issues; they are significant financial liabilities waiting to be exploited.
Time and again, data shows that high-profile security disasters often begin with simple, preventable internal failures. The costs extend far beyond the immediate cleanup.
Regulatory Fines: A breach violating regulations like GDPR or HIPAA can trigger fines running into the millions.
Legal Liability: Class-action lawsuits from customers whose data was exposed can lead to settlements that dwarf the initial cost of the breach.
Operational Disruption: A ransomware attack that originates from an internal vulnerability can shut down business operations for days or weeks, leading to massive revenue loss.
Reputational Harm: The loss of customer trust is an intangible but incredibly damaging cost that can hamstring revenue for years.
The ROI on a proactive internal threats assessment is crystal clear. The cost of identifying and fixing these weak spots is a fraction of what it takes to manage the fallout from a single major breach.
A Global Perspective on Internal Risk
The financial stakes are only getting higher. Cyber attacks are becoming more frequent and sophisticated globally. For example, recent data shows the Asia-Pacific region was hit hardest in 2024, accounting for 34% of all incidents. Attackers relied heavily on malware, ransomware, and unauthorized server access, with credential harvesting as a primary goal.
The 2025 IBM X-Force Threat Intelligence Index reinforces how these trends make internal assessments critical for hardening defenses against global threats. You can discover more insights from the IBM report to see exactly how these threats are evolving.
This global context underscores why a proactive, ethical approach to risk management is no longer optional. By focusing on systemic vulnerabilities instead of policing individuals, you can build a resilient security posture that protects your financial stability. An AI-driven, EPPA-compliant assessment pinpoints where the real risks lie—in flawed processes and controls. This allows you to make targeted, cost-effective improvements that deliver a measurable return. It’s about spending smarter to prevent a crisis, not spending more to clean one up.
It’s Time to Take Proactive Steps to Secure Your Organization
Waiting for an insider incident to happen is not a strategy—it's a massive gamble with your organization's future. If the constant cycle of data breaches and compliance failures has taught us anything, it's that proactive, ethical internal threats assessments are non-negotiable for any modern business.
This is about protecting your operational integrity, financial stability, and reputation. The old, reactive model of cleaning up the mess after the damage is done is a failed approach. The modern standard is prevention, focusing on fixing systemic weaknesses in processes and controls rather than policing individuals.
Moving from Awareness to Action
Understanding the need for a proactive posture is the first step, but implementation is what builds resilience. It’s time to evolve your risk management program beyond periodic audits and manual checklists. For a broader view of how this fits into your overall defense, you can explore resources on robust organizational security strategies to see how internal diligence strengthens your entire security posture.
The goal is to foster a security culture that is both effective and ethical, one that aligns with EPPA standards and respects employees. An AI-driven, non-intrusive platform gives you the capability to identify human-factor risks long before they escalate into a crisis.
An investment in proactive internal threat detection is an investment in business continuity. It shifts resources from costly, disruptive post-incident cleanups to strategic, preventive measures that strengthen the entire enterprise.
This modern approach provides decision-makers in Compliance, Risk, Security, and HR with the intelligence needed to fortify the organization from within. It replaces ambiguity with data-driven insights, allowing you to address vulnerabilities with precision.
Your Path to a More Resilient Organization
Whether you are ready to explore a platform independently or prefer a strategic discussion about your unique needs, a clear path forward exists. The time to act is now, before a preventable incident forces your hand.
We invite you to see how an advanced, AI-driven platform can transform your approach to managing human-factor risk. Take the next step to build a more resilient and secure organization from the inside out, protecting your assets and your people with an ethical, forward-thinking framework.
At Logical Commander Software Ltd., we provide the tools to build a proactive and ethical defense against internal risks. Our AI-driven, EPPA-compliant platform helps you identify and mitigate threats before they cause financial, legal, or reputational damage—without invasive surveillance.
Ready to mature your internal risk management program?
%20(2)_edited.png)
