A Guide to Risk Management Enterprise Governance
- Marketing Team

- Dec 27, 2025
- 15 min read
Updated: Dec 29, 2025
For years, enterprise risk management was seen as a defensive function—a compliance department tucked away in a back office, focused on ticking boxes. That era is over. Today, it’s a core strategic driver for resilience and growth, a top-down approach that weaves risk awareness into the very fabric of the business, from C-suite strategy all the way to daily operations.
Why Modern Risk Management Is a Strategic Imperative

In our interconnected world, treating risk in isolated silos is a recipe for disaster. A cybersecurity breach isn't just an IT problem; it's a reputational crisis, an operational shutdown, and a financial liability rolled into one. The old way of managing risks department-by-department leaves dangerous gaps where threats can fester and multiply.
This is where a modern risk management enterprise framework is so essential. Think of it as upgrading from a loose collection of neighborhood watch groups to a fully integrated, city-wide emergency response system. Instead of each department just guarding its own turf, a unified strategy creates a central nervous system that sees and responds to threats holistically. This is the only way to build genuine organizational resilience.
The High Cost of a Reactive Stance
Waiting for a risk to explode before you act is like installing a smoke detector after the fire has already started. The consequences are almost always severe, ranging from crippling financial penalties to irreparable damage to your brand. Inaction isn't a neutral choice; it's an active decision to accept potentially catastrophic outcomes.
Just look at the modern threat landscape. Cyber incidents have held the top spot as the number one global business risk for four years running. The financial toll is staggering—cybercrime costs are projected to hit $8.2 trillion annually, disrupting supply chains and grinding core operations to a halt worldwide.
This trend is forcing a major shift. Forrester reports that 37% of enterprise risk managers now see information security and cyber risk as their primary concern, especially since nearly 75% of enterprises were hit by at least one critical risk event last year.
An effective enterprise risk management program transforms risk from a purely negative concept—something to be avoided—into a source of strategic intelligence. It provides the foresight needed to turn potential vulnerabilities into opportunities for strengthening the organization.
Shifting to Proactive Prevention
The most resilient organizations have moved far beyond mere crisis management. They’ve embraced a proactive, prevention-first mindset, powered by modern technology. This shift is fundamental. It means identifying the subtle, early warning signs of potential misconduct or operational weakness before they escalate into full-blown crises.
This forward-looking approach is the new gold standard for a few key reasons:
It Preserves Reputation: Preventing an ethical lapse is infinitely better than managing the public relations fallout from one.
It Strengthens Governance: A proactive model gives leadership the visibility needed for decisive, informed governance.
It Builds Trust: Employees, customers, and investors have far greater confidence in an organization that anticipates and neutralizes threats effectively.
Ultimately, a robust framework for risk management enterprise governance isn't just about avoiding losses. It’s about building a durable, trustworthy, and agile organization that’s truly prepared for the challenges of tomorrow. To dive deeper, explore our comprehensive guide on modern enterprise risk management solutions.
2. Mapping the Landscape of Internal Enterprise Risks
While external threats like cyberattacks and market swings tend to grab the headlines, any seasoned leader knows the most dangerous vulnerabilities often come from within. A truly effective risk management enterprise program understands this. Your organization is a complex ecosystem where human behavior, daily operations, and ethical lines intersect, creating fertile ground for risk if you’re not paying attention.
Imagine your company as a sophisticated biological system. Its policies, procedures, and governance are the immune system, designed to keep things healthy and fight off threats. In this model, internal risks show up in two very different but equally damaging ways.
Malicious Insiders as Pathogens
The first type of risk comes from malicious insiders—people who deliberately use their access and know-how for personal gain or to hurt the company. These are the pathogens, actively trying to infect and weaken the system from the inside.
A recent study drove this point home, finding that insider-related incidents cost organizations an average of $16.6 million per event. These aren't just isolated IT security issues; they cover a wide spectrum of misconduct.
Financial Fraud: An employee in the finance department could be tweaking invoices or padding expense reports, quietly siphoning off funds over months or even years.
Data Theft: A sales executive on their way out the door might download the entire customer database to take to a competitor, walking away with your most valuable intellectual property.
Sabotage: A disgruntled IT admin could intentionally misconfigure a critical server, triggering operational shutdowns and costing the company a fortune in lost revenue.
These are calculated attacks designed to bypass the organization's defenses. A rock-solid approach to insider risk is the only way to spot these threats before they cause widespread damage. We cover this in much more detail in our complete guide to insider risk management.
Unintentional Errors as Autoimmune Responses
The second, and often more common, internal risk is born from unintentional mistakes. Think of this as an autoimmune response—the system accidentally attacks itself because of blind spots, negligence, or broken processes. The intent isn’t malicious, but the results can be just as destructive.
These vulnerabilities are often hiding in plain sight, woven into the fabric of everyday operations and team dynamics.
The greatest internal risks are often not the result of a single catastrophic failure, but the slow erosion of integrity and diligence over time. Neglecting these seemingly small gaps can lead to systemic collapse.
Consider a few real-world scenarios:
Conflicts of Interest: A manager hires their cousin's company for a big project without disclosing the relationship, opening the door to overinflated costs and subpar work.
Ethical Blind Spots: A marketing team, thinking they’re just being “competitive,” launches a campaign with misleading claims. The result? Hefty regulatory fines and a major hit to the brand’s reputation.
Procedural Negligence: An HR team member forgets to follow the proper offboarding checklist, leaving a former employee’s system access active for weeks—creating a gaping security hole.
A Unified Perspective is Essential
Treating these incidents—from deliberate fraud to unintentional ethical lapses—as isolated events is a huge mistake. They're all symptoms of deeper weaknesses in your company's internal risk posture. A conflict of interest that goes unchecked today could easily escalate into intentional fraud tomorrow if the cultural and procedural gaps aren't fixed.
This is why a holistic, unified view is non-negotiable for leaders in HR, Compliance, and Security. An effective risk management enterprise strategy means breaking down the departmental silos to see the complete picture. By mapping this internal landscape, you can start building a resilient and ethical framework that protects your organization from both targeted attacks and self-inflicted wounds.
Shifting From Reactive Detection To Proactive Prevention
For far too long, the standard approach to internal risk has been a bit like a smoke detector—it only sounds the alarm after a fire has already started. This traditional, reactive culture is built around detection and investigation. And while that’s necessary, it's a fundamentally limited model. It forces you into a post-mortem, analyzing the damage after a major breach of policy, ethics, or security has already happened. The organization is always on the defensive, stuck in a costly cleanup mode.
This reactive stance means you're perpetually one step behind. By the time an issue is big enough to trigger a formal investigation, the real damage is often done. Financial losses might be unrecoverable, your reputation could be tarnished, and employee trust may be permanently broken. A truly effective risk management enterprise strategy has to make a crucial pivot.
The goal is to move from a culture of "detect and respond" to a much more powerful mindset of "prevent and anticipate." This is all about seeing the faint smoke signals long before they erupt into a full-blown crisis.
The Power Of Knowing First And Acting Fast
Modern platforms give organizations the power to adopt a "Know First, Act Fast" philosophy. This entire approach is built on identifying the subtle, early indicators of potential risk that would otherwise fly completely under the radar. It's the difference between hearing a faint tremor and waiting for the earthquake to hit. By catching these early signals, leaders can intervene ethically and constructively, protecting both the organization and its people from preventable harm.
To see how this works, it’s important to understand the two different types of risk signals.
Preventive Risk Signals: These are the earliest, most subtle indicators. Think of a minor procedural gap, a small conflict of interest that needs clarification, or a slight inconsistency in a report. They don't signal definite wrongdoing, but they do represent an opportunity for an early, low-stakes intervention.
Significant Risk Signals: These are much more direct indicators pointing to a potential breach or misconduct that requires immediate verification. They are serious enough to trigger a formal, structured response according to your organization's governance protocols.
This distinction is the key to building a proactive culture. Instead of waiting for a major incident, the system flags minor deviations that can be addressed through guidance, training, or a simple process fix. This kind of proactive risk management strategy in your enterprise helps reinforce an ethical culture from the ground up.
From Post-Mortem To Proactive Intervention
Imagine a manager who consistently approves expense reports for a direct report that are just under the threshold requiring a second signature. A reactive system wouldn't notice a thing until a formal audit reveals a pattern of fraud months later. By that point, thousands of dollars could be gone for good.
A proactive system, on the other hand, would flag this procedural anomaly as a preventive risk signal. It isn't an accusation; it's just an objective data point. This allows HR or Compliance to have a supportive conversation with the manager, clarify the expense policy, and reinforce the importance of proper scrutiny. The issue gets resolved before it ever escalates into fraud, protecting both the company's assets and the manager's career from a major misstep.
The infographic below shows how these internal risks are all interconnected across people, systemic threats, and overall integrity.
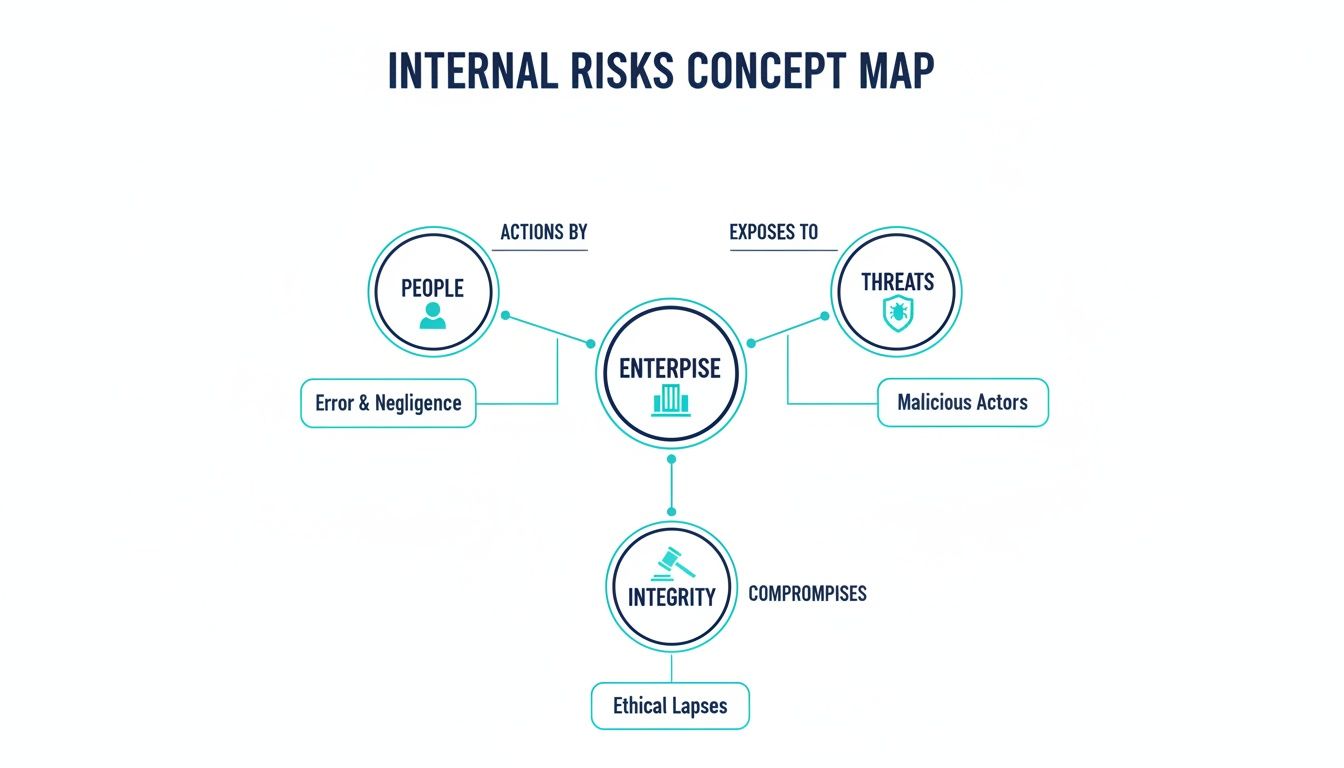
The map makes it clear: a single organization is vulnerable to interconnected risks stemming from its people, its exposure to threats, and its commitment to ethical integrity, demanding a unified prevention strategy.
This fundamental shift in thinking is best understood by comparing the two models side-by-side.
Reactive Detection vs Proactive Prevention
Attribute | Reactive Detection (Traditional Approach) | Proactive Prevention (Modern Approach) |
|---|---|---|
Timing | Post-incident, after damage has occurred. | Pre-incident, identifying early warning signs. |
Focus | Investigation, assigning blame, and damage control. | Intervention, guidance, and risk mitigation. |
Data Signals | Major violations, whistleblower reports, audit findings. | Subtle anomalies, procedural gaps, minor deviations. |
Outcome | Costly investigations, legal fees, reputational harm. | Early resolution, process improvement, cultural reinforcement. |
Mindset | "Catch and punish." | "Identify and support." |
The contrast is stark. One model is stuck in a perpetual cycle of crisis management, while the other builds institutional resilience from the inside out.
Proactive prevention isn't about predicting the future with a crystal ball. It’s about creating a system so attuned to your organization's operational health that it can detect the earliest signs of trouble, allowing you to act with precision and care.
This strategic shift completely redefines the purpose of risk management. It moves the function from being a reactive, enforcement-driven body to a proactive, strategic partner in preserving the organization's integrity and strength. By focusing on prevention, you build a stronger, more ethical, and more durable enterprise.
Building an Ethical and Compliant ERM Framework
Bringing any new technology into your risk management strategy isn’t just a technical decision—it comes with a heavy dose of ethical responsibility and strict regulatory duties. Modern tools can't just be dropped into a workflow and be expected to work. They have to be built on a bedrock of trust, transparency, and total adherence to the law.
The goal is to create a system that is 'Ethical by Design,' meaning it operates firmly within established legal and moral lines. This flips the script entirely, turning compliance from a frustrating hurdle into a core strategic asset. Instead of seeing regulations as red tape, a well-built framework uses them as guardrails that keep technology serving its purpose with integrity.
You don’t need invasive or coercive tactics to manage risk effectively. In fact, those methods often create more liability than they prevent.
Navigating Global Regulatory Guardrails
Key global frameworks draw clear, non-negotiable lines in the sand for how technology can be used in the workplace. Knowing these rules isn't just a good idea; it's the first step to building a program that won't land you in legal hot water.
Regulations like Europe’s General Data Protection Regulation (GDPR) and the Employee Polygraph Protection Act (EPPA) in the United States aren't just suggestions. They are legally binding standards designed to protect individual dignity and privacy.
These frameworks explicitly forbid several practices that have absolutely no place in a modern, ethical ERM system:
Lie Detection or Polygraph Logic: Any system used to determine truthfulness or deception is completely off-limits. This falls squarely outside what is legally and ethically permissible.
Psychological or Behavioral Profiling: You cannot make assumptions about an employee’s mental state, personality, or future actions based on data. That's a huge overstep.
Covert Surveillance or Monitoring: Hidden tracking or monitoring of employee activities without their knowledge and consent is a direct violation of their fundamental right to privacy.
Advanced solutions are engineered from the ground up to respect these rules, ensuring every function operates in full compliance.
The Role of Objective Indicators, Not Judgments
Here’s the key to using AI ethically in risk management: it must be a decision-support tool, not a decision-maker. An ethical platform gives you structured, objective risk indicators without ever making a judgment about someone's intent, character, or guilt.
Think of it like the instrument panel in an airplane cockpit. It gives the pilot clear, factual data—altitude, fuel levels, airspeed—but it doesn't tell them how to fly the plane.
For example, the system might flag a potential conflict of interest based on structured data from a disclosure form. It isn’t accusing anyone of wrongdoing. It's simply highlighting a procedural issue that needs a human review, based on the company's own governance policies.
Effective risk management empowers human experts with clear, objective information. It never replaces their judgment. The process must always remain auditable, transparent, and centered on human decision-making.
This approach keeps due process front and center. The technology’s job is to turn scattered information into organized intelligence, which helps HR, Compliance, and Legal teams act faster and more consistently on credible signals.
Turning Compliance Into a Strategic Advantage
The market for risk management enterprise solutions is booming, with projections expecting it to hit $23.7 billion by 2028. But even with that growth, maturity in the field is lagging behind. Only 35% of financial leaders say they have comprehensive ERM processes in place.
This gap represents a massive opportunity for organizations that build their programs on a strong ethical and compliant foundation. By integrating specific guidelines, such as dedicated risk management and compliance frameworks for enterprise AI systems, you do more than just mitigate risk.
You build a program that strengthens stakeholder trust, attracts top talent, and protects the one thing you can’t buy back: your reputation. In the end, a compliant framework is a resilient one.
Weaving Together Your Operational Risk Workflow

When it comes to managing risk, siloed departments and scattered spreadsheets aren't just inefficient—they're downright dangerous. The moment HR, Legal, Compliance, and Security start operating in their own worlds, critical information gets lost, response times grind to a halt, and accountability vanishes. This fractured approach is a breeding ground for blind spots.
A modern risk management enterprise strategy tears down those walls by building a unified operational workflow. Think of it as installing an "operational backbone" for your entire organization. It’s a central, shared system that finally gets these critical functions speaking the same language and acting on a single, undisputed source of truth.
This isn't just about getting more organized. It's about fundamentally rewiring how your company sees and acts on risk, turning a mess of disjointed data points into structured, actionable intelligence.
Forging a Common Operational Language
The first huge win of a unified workflow is creating a consistent language for risk. In a siloed company, every department has its own jargon and metrics. What Security calls a "Level 2 Incident," HR might log as a "Code of Conduct Violation," while Legal sees it as a "Potential Litigation Risk." Sound familiar?
That kind of inconsistency creates confusion, delays, and completely misaligned responses. A unified platform solves this by bringing every risk-related event under one clear framework.
Standardized Case Management: Every potential issue, from a conflict of interest disclosure to an insider threat signal, follows the same playbook.
Consistent Terminology: All teams use the same definitions for risk severity, status, and outcomes. No more translating between departments.
Traceable Actions: Every single step in the mitigation process is documented in one place, creating a perfect, auditable trail from signal to resolution.
This common language strips away ambiguity. When a risk pops up, every stakeholder immediately understands what it means and what their role is.
The Power of a Single Source of Truth
With a unified backbone in place, those scattered spreadsheets, messy email chains, and isolated databases finally become relics. A central platform becomes the single source of truth for all risk-related activity, and the practical advantages are immense.
For leadership, this means getting a real-time, holistic view of the company’s risk landscape. No more trying to stitch together conflicting reports. Instead, they get a clear, consolidated picture that supports sharp, informed governance. This is crucial, especially when business interruption is a top global risk. In fact, nearly 75% of enterprises faced at least one critical event last year, with 60% of organizations naming cyber-related interruptions as their biggest worry.
For example, managing the human fallout from critical events, often addressed through practices like Critical Incident Stress Debriefing, becomes a much more integrated part of the operational workflow.
A unified workflow ensures that risk management is no longer a series of disconnected reactions. It becomes a synchronized, traceable, and intelligent process that strengthens the entire enterprise.
Accelerating Collaboration and Response
When a risk signal is flagged on a unified platform, the right people from HR, Legal, and Security can be pulled into the loop instantly. The system is built for seamless collaboration, letting teams share information, assign tasks, and coordinate their response in real time.
Picture this scenario:
Signal: A potential conflict of interest gets flagged from an employee disclosure form.
Collaboration: The signal automatically notifies the Compliance officer and the employee's HR business partner.
Action: They can review the case file at the same time, add notes, and decide on next steps—like a clarifying conversation—right inside the platform.
Resolution: The entire process is documented, from the initial flag to the final outcome, leaving an unshakeable audit trail.
You simply can’t get this level of synchronized action with a disconnected, manual approach. By building a unified operational workflow, an organization elevates its risk management from a scattered, reactive chore into a proactive, cohesive, and powerful strategic asset. This operational backbone doesn't just connect departments; it reinforces the integrity and resilience of the entire enterprise.
Your Enterprise Risk Management Questions, Answered
As leaders in HR, Compliance, and Security start building or fine-tuning their enterprise risk management strategy, the same core questions always surface. Getting the answers right is the key to creating a framework that’s not just effective, but ethical and built to last. Let's dig into some of the most pressing questions we hear from organizations moving toward a modern ERM program.
What Is the First Step in Building an Enterprise Risk Program?
The foundational step has nothing to do with technology. It’s about getting the right people in the same room to agree on a shared language for risk.
Before you even think about a platform, you have to break down the silos. This means pulling key stakeholders from HR, Legal, Compliance, and Security together to define a common framework for identifying, assessing, and neutralizing internal threats. This initial alignment is where you agree on internal governance policies and pinpoint the specific risks you need to manage—things like human capital risk, insider misconduct, and integrity violations.
Only after that strategic foundation is poured can a central platform serve as the operational backbone. It ensures every department is working from the same data and procedures, turning a fragmented process into a unified, powerful strategy.
How Can AI Enhance Risk Management Without Violating Privacy?
This is the most critical question, and the answer is simple: you use AI that is 'Ethical by Design.'
Ethical AI enhances risk management by focusing on structured, objective indicators, not invasive surveillance or behavioral profiling. A tool that is fully compliant with strict regulations like GDPR never performs secret monitoring, analyzes employee sentiment, or makes judgments about individuals. That’s a legal and cultural minefield.
Instead, it identifies predefined risk signals based on factual, organizational data—like flagging a potential conflict of interest from a submitted disclosure form. This approach delivers critical decision-support, not automated conclusions. The system surfaces potential procedural issues for human review, ensuring that dignity, privacy, and due process are always at the forefront.
An ethical AI platform doesn't replace human judgment; it refines it. By surfacing objective, structured data points, it allows leaders to focus their expertise on mitigation and support, rather than getting lost in manual data sifting.
This distinction is fundamental. The system acts as an expert assistant, organizing information so your human experts can make the final, nuanced decisions needed to protect the organization.
How Do You Measure the ROI of Proactive Risk Management?
Measuring the return on a proactive program requires a mental shift—from tallying the "cost of incidents" to calculating the "value of prevention." It's all about quantifying the disasters that didn't happen. A unified platform provides the hard data you need to track these KPIs and prove tangible, long-term value.
Key metrics for demonstrating ROI include:
Reduction in Incident Frequency and Severity: Track a measurable drop in internal fraud cases, compliance breaches, or other policy violations over time. This shows the direct impact of getting ahead of problems.
Improved Response Time: Measure the time from when a risk signal is first flagged to when it’s successfully resolved. Faster resolution means less exposure and lower potential costs.
Enhanced Auditability and Lowered Fines: Demonstrate a clear, traceable process for every risk case. This robust documentation can dramatically reduce regulatory fines and legal heat during audits.
Lower Investigation Costs: By stopping small issues from becoming major crises, you avoid the massive costs of formal, resource-draining investigations.
Reputation Protection: This one is harder to quantify, but it’s priceless. Preventing a single major ethical failure or data breach protects brand value—an asset that, once lost, is incredibly difficult to win back.
By tracking these metrics, you can reframe the conversation around risk management from a cost center to a strategic driver of value. Proactive prevention becomes a clear, measurable investment in your organization's resilience and integrity.
Ready to shift from a reactive stance to proactive prevention? Logical Commander Software Ltd. provides the unified operational platform to help you know first and act fast. Our E-Commander platform centralizes risk intelligence and enables ethical, privacy-preserving risk management across your entire enterprise. Discover how to build a more resilient organization by visiting our website.
%20(2)_edited.png)
