Mastering the Operational Risk Management Process
- Marketing Team

- 2 days ago
- 17 min read
Updated: 7 hours ago
An operational risk management process is the framework you build to see what’s coming. It’s how an organization systematically identifies, assesses, and controls the risks that come from broken internal processes, human error, and flawed systems—or from curveballs thrown by the outside world.
It’s about building a resilient organization that gets ahead of problems instead of just reacting to them. Done right, it becomes a core strategic advantage.
Why Your Old Risk Process Is Failing You
Let's be honest. Trying to manage operational risk with a bunch of static spreadsheets is like driving down the highway looking only in the rearview mirror. It’s a recipe for disaster. In a world of complex regulations, digital threats, and unpredictable human factors, a reactive approach just doesn't work anymore.
Your old process is likely failing because it’s siloed, sluggish, and completely lacks the foresight needed to actually protect your business.
This guide isn't about checking a compliance box. We're going to reframe the operational risk management process as a proactive, ethical foundation for building a trustworthy and successful organization—from the inside out.
The Problem with Static Approaches
Too often, risk management lives in isolated spreadsheets scattered across different departments. HR has their version, Legal has another, and Security and Compliance are tracking things their own way. This fragmentation creates massive, dangerous blind spots.
By the time someone manually pieces all that data together for a quarterly review, the risk landscape has already changed. The information is obsolete the moment you see it.
This static model guarantees a few critical failures:
Delayed Insights: Outdated information makes real-time decision-making impossible. It allows small issues to fester and grow into full-blown crises before anyone even notices.
Inconsistent Data: When every team uses different formats and criteria, getting a single, unified view of your company-wide risk posture is a nightmare.
No Collaboration: Siloed data actively kills the cross-functional teamwork you need to tackle complex internal risks that don’t fit neatly into one department’s box.
A reactive risk process is a history lesson; it documents what already went wrong. A modern, proactive operational risk management process is about knowing first. It gives you structured, objective signals so you have the foresight to act before an issue becomes a crisis.
Moving from Reaction to Prevention
The entire goal is to build a system that anticipates problems. This requires a fundamental shift in both culture and technology, moving toward a state of continuous improvement and learning. If your old risk process is failing, its inability to adapt is a primary reason. It's why fostering continuous professional development within your team is so critical to keeping your strategies sharp and effective.
A modern operational risk management process is dynamic and deeply integrated. It creates a common language and a single source of truth where all stakeholders can see the same data, track mitigation efforts in real-time, and make smart, collaborative decisions.
This approach transforms risk management from a passive, backward-looking chore into an active, forward-looking strategic function that drives true resilience. To see how this applies on a broader scale, you can explore a comprehensive view of risk management in the enterprise.
Building Your Internal Risk Radar

Before you can manage operational risk, you have to see it clearly. A truly effective operational risk management process starts with mapping your entire internal landscape to find vulnerabilities before they find you.
This is not a job for one department working in a vacuum. It demands a holistic view that no single person or team possesses. The first real step is to build a cross-functional risk identification team—not to add another meeting to the calendar, but to create a powerful, collaborative sensor network.
Assembling Your Cross-Functional Team
Your goal here is to bring together experts who see the organization from different, critical angles. Each one brings a unique perspective on potential threats and procedural gaps that others would almost certainly miss.
Your core team should have a seat at the table for:
Human Resources: They’re dialed into the human element—from hiring and employee relations to the behavioral red flags that can signal internal misconduct.
Legal and Compliance: These are your guardrails. They ensure every identification method is ethical and compliant with regulations like GDPR or other industry-specific rules.
IT and Security: This team sees the technical weak points, from shaky data access controls and system vulnerabilities to the potential for insider data theft.
Operations: These are the people on the ground floor. They live and breathe the day-to-day workflows and know exactly where the real-world failure points are.
This collaborative structure is designed to smash the information silos that allow risks to fester undetected. When these teams connect, they start to see a complete picture that was previously just a collection of isolated facts.
The most dangerous operational risks are often the ones that exist in the white space between departments. A cross-functional team is designed specifically to illuminate these blind spots, turning fragmented knowledge into a unified, actionable picture of your internal risk posture.
Moving Beyond Generic Checklists
Let's be honest: generic risk checklists are a start, but they rarely uncover the unique vulnerabilities hiding inside your specific operational workflows. To build a radar that actually works, you need to use more dynamic and interactive identification methods.
These techniques are designed to pull knowledge from your team and translate it into a structured list of potential risks. They move the process from a passive review into an active discovery mission.
One of the most powerful tools in your arsenal is the collaborative risk workshop. This isn't just another brainstorming session. It's a structured meeting where your cross-functional team systematically deconstructs a key business process, like vendor onboarding or expense approvals.
During the workshop, the team maps out each step and hammers it with critical "what if" questions:
What if an invoice is submitted from an unapproved vendor?
What if an employee approves a payment to a company they have a personal stake in?
What if sensitive customer data gets mishandled during a routine data transfer?
This line of questioning uncovers procedural gaps, conflicts of interest, and control weaknesses that a simple checklist would never find. Another great technique is process mapping, where you visually diagram workflows to spot bottlenecks, single points of failure, and areas that lack proper oversight.
Identifying Early Signals Ethically
A modern operational risk management process is all about spotting the early, objective signals of human capital risks—without crossing ethical lines. The focus must be on identifying structural vulnerabilities, like procedural loopholes or potential conflicts of interest, not on employee surveillance.
The key is to know first through structured, non-judgmental data. For example, instead of monitoring employee communications, an ethical system flags when a manager is solely responsible for approving their own expense reports—a clear procedural risk. For a deeper dive into how technology can assist, explore our guide on integrating a risk management API platform.
This approach gives you the foresight to act before a potential issue escalates, all while maintaining employee trust and dignity. By focusing on objective data points and auditable events, you build a radar that is both powerful and respectful of individual privacy.
How to Assess and Prioritize Real-World Risks

Once your cross-functional team has mapped out all the potential threats, the real work begins. You’re now looking at a raw, chaotic list of everything that could go wrong—from a sophisticated insider data breach to a minor compliance slip-up. The challenge is to bring order to this chaos and figure out which risks truly matter.
This is the assessment and prioritization stage of the operational risk management process. It’s where you transform that long list into a clear, actionable roadmap for your resources. You're making objective, data-informed decisions that focus your limited time and budget on the threats that pose the greatest danger to your business.
Using a Risk Matrix to Quantify Threats
The most effective way to cut through the noise is with a risk assessment matrix. This is a simple but incredibly powerful visual tool that helps you evaluate risks based on two key dimensions: the likelihood of an event happening and the potential impact it would have if it did.
Plotting each identified risk on this matrix forces you to move away from subjective guesswork and into a structured conversation. It prompts your team to ask the hard questions. For instance, is a disgruntled employee stealing client data more or less likely than a critical system failure during peak season? And which one would cause more financial or reputational damage?
This framework gives stakeholders from different departments a common language, ensuring everyone is evaluating risk using the same consistent criteria.
Defining Your Assessment Criteria
Before you can plot anything, your team has to agree on what "high impact" or "very likely" actually means in the context of your business. This calibration step is absolutely essential for consistency.
A common approach is a 5x5 matrix, which gives you a more detailed view than a simpler 3x3 model. Here’s a practical example of how you might define your scales:
Likelihood (Probability of Occurrence)
5 - Almost Certain: Expected to happen in most circumstances (>90% chance).
4 - Likely: Will probably happen in most circumstances (61-90% chance).
3 - Possible: Might happen at some point (41-60% chance).
2 - Unlikely: Could happen at some point (11-40% chance).
1 - Rare: May only happen in exceptional circumstances (<10% chance).
Impact (Severity of Consequences)
5 - Catastrophic: Threatens the survival of the business; massive financial loss; irreparable reputational damage.
4 - Major: Serious financial loss; significant customer and media attention; requires external intervention.
3 - Moderate: Noticeable financial impact; negative press; requires senior management involvement to resolve.
2 - Minor: Slight financial loss; contained operational disruption; managed by normal procedures.
1 - Insignificant: Minimal impact on operations or finances; resolved with little effort.
These definitions give you a solid foundation for a more objective compliance risk assessment, making sure that when one person says a risk is "major," everyone else knows exactly what that implies.
Turning Assessment into Prioritization
With your risks plotted on the matrix, you’ll have a clear visual hierarchy. Anything landing in that top-right corner (high likelihood, high impact) becomes an immediate priority. These are the critical threats that demand urgent attention and resource allocation.
Prioritization isn't just about tackling the biggest risks first. It's about creating a strategic action plan that systematically addresses threats based on their potential to disrupt your business objectives, ensuring you apply controls where they will have the most meaningful effect.
This data-driven approach is invaluable for getting leadership buy-in. Instead of handing them a long, intimidating list of worries, you can provide a prioritized heat map that shows exactly where the organization is most vulnerable and where mitigation efforts need to be focused.
The global risk landscape only reinforces the need for this kind of structure. Top global risk surveys consistently highlight operational challenges that demand this level of management. For example, cyber risk is ranked as the top threat for 2025 and is expected to hold that position through 2028, with business interruption and economic slowdowns right behind it. Reading up on these top global risk findings on Aon.com helps validate your internal assessments and ensures your operational risk management process is aligned with real-world threats.
Designing Controls That Actually Work

Once you’ve prioritized your biggest threats, the operational risk management process pivots from analysis to action. This is where you get your hands dirty, designing and implementing the controls that form the practical defense system for your entire organization.
The goal here isn't to build taller walls or try to eliminate every conceivable risk—that's a fool's errand. It’s about creating a smart, multi-layered set of controls that work together to prevent, detect, and correct issues before they can cause real damage.
The Three Pillars of Risk Control
Effective control design isn't a one-trick pony. It relies on three distinct types of measures that create a resilient, interlocking framework. Each one plays a specific role at a different stage of a potential incident.
Preventive Controls: These are your front-line defenses, the proactive measures you put in place to stop something bad from happening in the first place.
Detective Controls: Think of these as your tripwires. They are reactive measures designed to identify and alert you that an incident has occurred.
Corrective Controls: These are your cleanup crew. They kick in after an incident is detected to limit the damage, fix the underlying problem, and stop it from happening again.
A classic mistake is to lean too heavily on just one type, usually preventive controls. A truly robust system integrates all three. For example, a strong password policy is preventive, but automated alerts for multiple failed login attempts are detective.
Making Controls Practical and Ethical
A control that only exists on paper is completely useless. The best ones are woven seamlessly into daily workflows, making them easy for people to follow and difficult to circumvent. Overly complex or burdensome controls just invite workarounds, which creates a whole new set of unforeseen risks.
Take a common scenario like managing high-value transactions. A simple and effective preventive control is a dual-authorization protocol, which requires a second manager to approve any payment over a certain threshold. It’s a low-friction way to prevent both fraud and costly human error.
To back that up, a detective control could be an automated system that flags and sends an immediate alert to the compliance team whenever a payment is made to a new, unverified vendor account. This doesn't stop the payment, but it ensures immediate oversight.
Ethical considerations are just as important. Controls must be designed to respect employee privacy and comply with regulations like the Employee Polygraph Protection Act (EPPA). The focus should always be on monitoring processes and systems for anomalies, not on surveilling individuals.
To illustrate how these controls function in a real-world internal risk scenario, consider the following table. It breaks down the different control types and shows how they can be applied using a modern, ethical risk platform like E-Commander.
Control Types for Mitigating Internal Operational Risks
Control Type | Objective | Example Scenario (e.g., Insider Data Theft) | E-Commander Application |
|---|---|---|---|
Preventive | Stop an incident before it occurs. | Restrict access to sensitive databases based on job role (Principle of Least Privilege). | Use pre-hire integrity assessments to identify behavioral risk indicators for roles with high-level data access, preventing a poor fit. |
Detective | Identify an incident as it happens. | Set up automated alerts for unusual data access patterns, like large downloads outside of business hours. | Flag anomalous patterns in control adherence, such as a team consistently bypassing dual-authorization, signaling a systemic weakness. |
Corrective | Remediate damage and prevent recurrence. | Immediately revoke access credentials for the involved account and launch a forensic investigation. | Trigger a mandatory retraining module on data handling for the entire team after a near-miss is identified, fixing the root cause. |
As the table shows, a modern, ethical platform enhances each control layer, moving beyond simple technical fixes to address the human factor at the core of operational risk. This holistic approach is what builds true institutional resilience.
The Critical Role of Continuous Monitoring
Designing controls is only half the battle. Your business environment is always in motion—new tech is adopted, processes evolve, and fresh threats pop up. A control that worked perfectly last year might be completely obsolete today.
This is why continuous monitoring is non-negotiable.
Manual spot-checks and periodic audits just don't cut it anymore. They give you a snapshot in time, completely missing the dynamic nature of modern operational risks. True resilience comes from persistent, automated oversight that makes sure your controls are working day in and day out.
This shift is especially vital in sectors facing rapidly evolving threats. In finance, for instance, cyber threats now dominate the operational risk landscape. A recent report found that over 47 leading global financial firms named cybersecurity as their top emerging operational risk. In fact, for the fourth year running, cyber incidents were named the number one global business risk. You can get more details from the full operational risk report on ORX.org.
Implementing automated key risk indicators (KRIs) is a powerful way to get this done. These are specific metrics that act as an early warning system, telling you when a control might be failing or when your risk exposure is creeping up. For example, a sudden spike in data access requests from a single department could be a KRI that triggers an immediate review, letting you investigate a potential insider threat before a breach happens. That proactive stance is the essence of a modern, effective control framework.
Building a Resilient Incident Response Framework
Let's be realistic: even with the best preventive controls in the world, incidents are going to happen. It's not a matter of if, but when. The real test of an organization's resilience isn’t its ability to dodge every single bullet, but how it acts when one finally hits. This is where an efficient incident response framework becomes your playbook, turning potential chaos into a structured, manageable process.
Without a clear plan, teams scramble. Evidence gets lost or mishandled. Minor issues quickly spiral into full-blown crises. A well-defined framework ensures that from the moment an incident is flagged, everyone knows their role, what to do next, and how to work together to contain the damage and fix the root cause. This kind of systematic response is a non-negotiable part of any mature operational risk management process.
Defining Clear Escalation Paths
When an incident pops up, the first question is always the same: who needs to know, and how urgently? If your escalation paths are vague, you're guaranteeing critical delays. A well-designed framework maps this out with precision, defining triggers that automatically route issues to the right stakeholders based on severity and type.
For instance, a minor procedural slip-up might just ping a line manager for review. But an alert signaling a potential data breach or a serious conflict of interest? That has to trigger an immediate, automated escalation to a pre-defined group of responders from HR, Legal, and IT Security.
This structure takes the guesswork out of the equation and drives rapid, coordinated action. It also gives you a clean audit trail, proving your organization responded in a timely and appropriate way.
Fostering Cross-Functional Collaboration
Operational incidents rarely stay neatly within one department’s borders. A personnel issue can quickly morph into a legal liability or even a security threat. Your response framework absolutely must be built for seamless collaboration between these key teams.
A siloed response is a failed response. When HR, Legal, and Security operate from separate playbooks using fragmented data, they lose precious time and context. A unified platform is essential for creating a common operational picture where all stakeholders can see the same information and coordinate their actions in real time.
This means building workflows that make it easy to share sensitive information securely and make joint decisions. For example, when HR opens an investigation, the framework should let them securely loop in the Legal team for counsel without having to export sensitive data into unsecured emails, which keeps the whole process buttoned up and defensible.
Building Meaningful Dashboards and KPIs
Once the immediate fire is out, the focus shifts to governance and getting better for next time. This is where reporting and key performance indicators (KPIs) become invaluable. Leadership doesn't need a raw data dump; they need a clear, real-time snapshot of the organization's risk posture.
Effective dashboards turn complex data into actionable insights. You should be tracking a few essential KPIs:
Mean Time to Detect (MTTD): How fast are we identifying incidents?
Mean Time to Remediate (MTTR): How long does it take us to fix an issue once we know about it?
Incident Recurrence Rate: Are we seeing the same problems pop up over and over again?
Control Effectiveness Score: Are the fixes we’re putting in place actually reducing our risk?
Tracking these metrics creates a powerful feedback loop. If your MTTR is creeping up, for example, it might be a sign that your remediation workflows need a tune-up or that your teams are stretched too thin. This data-driven approach is also crucial for showing compliance to auditors and regulators, giving them a transparent, auditable record of your risk management activities.
Ultimately, this system turns every incident into a learning opportunity, strengthening your entire operational risk management process. A crucial piece of this is also having a thorough Business Continuity Planning checklist to prepare for and handle broader disruptions. The need for these tools is driving huge market growth; the global risk management market is projected to more than double, hitting US$23.7 billion by 2028, fueled by the demand for smarter ways to analyze and mitigate risk. You can discover more insights about these risk management statistics on procurementtactics.com.
Your Actionable Operational Risk Rollout Plan
Strategy is nothing without execution. Let's move from the concepts we've discussed to the concrete actions you can take to implement or sharpen your operational risk management process. This isn't just about avoiding losses; it’s about making a deliberate shift from a defensive, reactive posture to one of proactive, ethical prevention.
This is how you build a more resilient, trustworthy, and successful organization from the inside out. Here are the steps you can take today to get started and drive real change.
Secure Leadership Buy-In and Form Your Team
Before a single policy is written, you need executive sponsorship. Your first move is to frame this initiative not as a cost center, but as a clear strategic advantage that protects the brand, improves decision-making, and builds a stronger culture.
Use the risk assessment matrix from earlier to make your case. Present the top three operational risks facing the business in a clear, data-driven way. Once you have that support, it’s time to assemble your cross-functional team. Pull in dedicated representatives from HR, Legal, IT, and key Operations departments. They’ll be your champions on the ground, and their combined expertise is essential for mapping risks and designing controls that actually work in the real world.
Select the Right Technology Partner
Let’s be honest: spreadsheets and siloed systems are the enemies of an effective risk program. To get real-time visibility and foster genuine collaboration, a unified operational platform is non-negotiable.
When you're evaluating partners, look for a solution that:
Is Ethical by Design: It must focus on objective, auditable signals and procedural gaps, not employee surveillance. This is a critical legal and cultural distinction.
Fosters Collaboration: The platform should provide a single source of truth that brings HR, Legal, and Security together, breaking down the silos that let risks fester.
Provides Actionable Dashboards: It has to translate raw data into clear, intuitive KPIs that leadership can understand and act on instantly.
Run a Focused Pilot Program
Don’t try to boil the ocean. Pick one high-risk, high-impact business process for a pilot program—something like vendor onboarding or expense approvals is a perfect starting point. A limited scope lets you test your workflows, configure your technology, and demonstrate tangible value quickly.
A successful pilot builds incredible momentum. It becomes a powerful internal case study that makes the argument for a broader rollout for you. This simple incident response flow shows how detection, response, and reporting form a continuous loop.
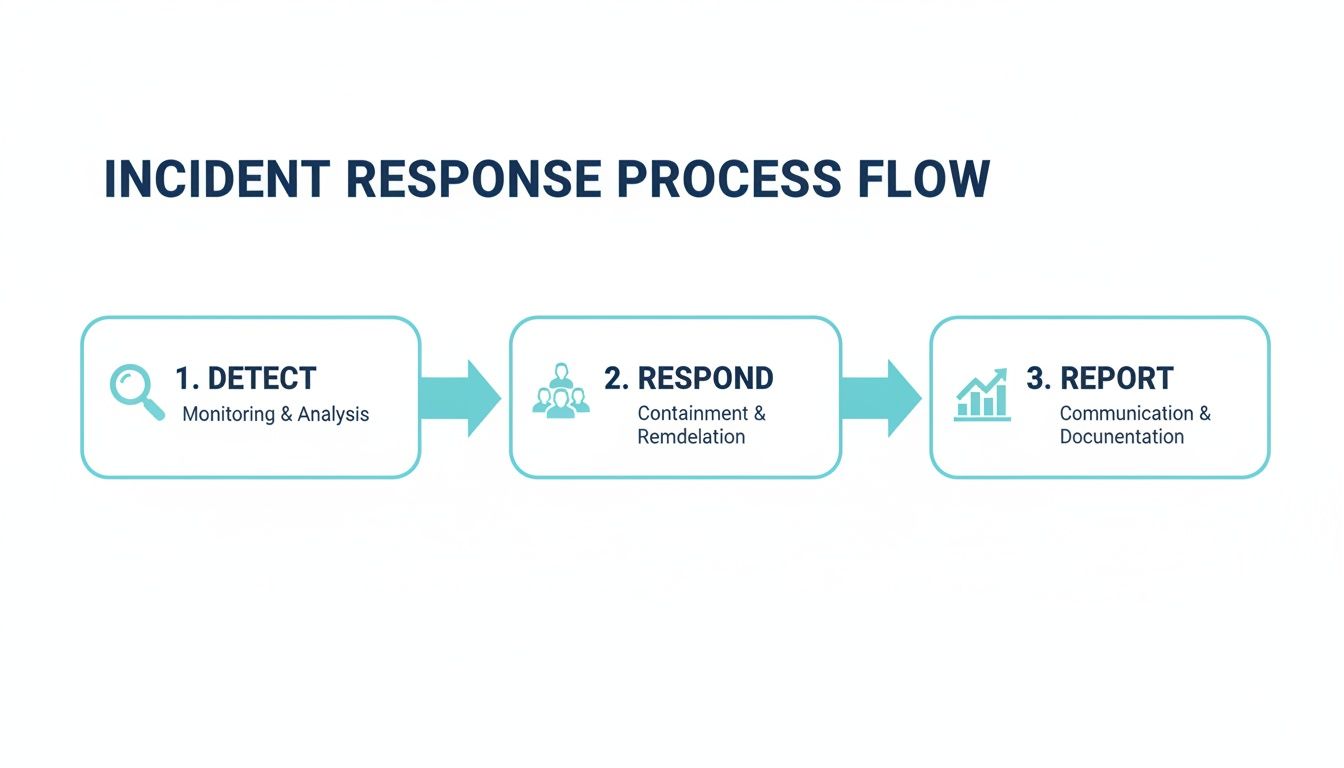
This visual underscores a critical point: every response must feed back into the system through reporting. That’s how you get smarter and improve future detection.
A successful rollout hinges on clear communication. Explain the 'why' behind the new process—how it protects both the company and its employees by creating a fairer, more transparent environment. Emphasize that the goal is proactive problem-solving, not punitive oversight.
Your Questions, Answered
When you're looking at building a modern operational risk process, you're bound to have questions. Let's dig into some of the most common ones we hear from leaders trying to get ahead of risk without creating a culture of distrust.
What Are the Core Stages of This Process?
Think of a modern process as a continuous loop, not a one-off project. It’s a cycle that keeps your organization resilient.
It all starts with Risk Identification, where your cross-functional team gets together to spot potential internal and external threats before they can cause any real damage. From there, you move into Risk Assessment. This is where you analyze each threat's likelihood and potential impact, which is absolutely critical for prioritizing your efforts and focusing on what matters most.
Next up is Risk Mitigation—the action phase. Here, you design and implement the controls needed to prevent, detect, or correct issues. The fourth stage, Monitoring and Reporting, is about continuously tracking how well those controls are working and giving leadership clear, actionable insights through KPIs. Finally, Incident Response gives you a structured playbook for managing events when they do occur, making sure every incident becomes a learning opportunity.
How Can We Implement This Without Creating a Surveillance Culture?
This is a huge—and valid—concern. The key is to focus on objective, auditable signals, not subjective behaviors. An "ethical by design" approach uses technology to identify structural risks, like a procedural loophole or a conflict of interest, not to make judgments about people. The system flags that a process is vulnerable, not that a person has bad intentions.
The goal of an ethical operational risk management process is to put guardrails on the road, not cameras in the car. It’s about strengthening procedures and providing decision-support, empowering human experts in HR and Legal to make informed choices with data, not replacing their judgment.
Transparency is also non-negotiable. The entire process has to be based on clear internal policies, preserve due process, and be communicated openly. That's how you build trust and get everyone on board.
What Is the Biggest Mistake Companies Make?
By far, the most common mistake is keeping operational risk stuck in a silo. When it’s treated as just another compliance task managed in scattered spreadsheets, the data becomes fragmented, insights are delayed, and the response is always reactive. This isolation makes it impossible to get the cross-functional collaboration you need to see the full picture.
Effective risk management demands a unified platform where HR, Security, Legal, and Audit teams can work together with a shared, real-time view of the organization's risk landscape. This integration is what finally moves the function from a simple cost center to a powerful strategic enabler that protects both the business and its people.
Ready to move from a reactive, siloed risk process to a unified, ethical, and proactive strategy? Logical Commander Software Ltd. provides the E-Commander platform to help your organization know first and act fast, turning scattered information into structured operational insight. Discover how our AI-driven, non-surveillance approach can protect your institution and your people by visiting us at https://www.logicalcommander.com.
%20(2)_edited.png)
