A Guide to the Risk Management API Integration Platform
- Marketing Team

- 3 days ago
- 15 min read
A risk management API integration platform is the central nervous system for your company's internal risk data. It uses Application Programming Interfaces (APIs) to weave together disconnected systems—like HR, Compliance, and Security—into a single, coherent picture. This creates one source of truth for spotting potential threats and misconduct ahead of time, without ever resorting to invasive surveillance.
Unifying Disparate Systems for Proactive Risk Intelligence
Historically, organizations handled internal risk in silos. The HR department kept its own records of employee relations issues, Compliance tracked regulatory adherence, and Security focused on protecting physical and digital assets. Each team used its own tools and spreadsheets, leading to a fragmented, reactive mess. This approach meant critical warning signs were routinely missed simply because the data was never connected. A modern risk management API integration platform completely changes this dynamic.

This kind of platform serves as an operational backbone, pulling in structured, non-judgmental data points from all these different sources. Manual data entry and disjointed investigations become a thing of the past. Instead, the platform automates the flow of information, enabling early signal detection and structured governance.
A modern platform is built on several key pillars that work together to turn isolated data into actionable intelligence.
Core Components of a Risk Management API Platform
Component | Function | Business Impact |
|---|---|---|
API Gateway | Manages, secures, and orchestrates API calls between all connected systems (HRIS, GRC, etc.). | Ensures secure and reliable data flow, preventing bottlenecks and unauthorized access. |
Data Normalization Engine | Translates data from various sources into a standardized, consistent format for analysis. | Eliminates data silos and allows for "apples-to-apples" comparison of risk indicators from different departments. |
Workflow Automation | Triggers predefined actions based on incoming data, such as creating a case or sending a notification. | Reduces manual work for HR and Compliance teams, speeding up response times to potential issues. |
Audit & Logging | Creates an immutable, time-stamped record of all data exchanges and actions taken. | Provides a defensible audit trail for regulatory reviews and internal investigations, ensuring transparency. |
These components are the engine that drives a more ethical and efficient operational model—one that prioritizes proactive prevention over costly reaction.
The Core Function of API Integration
At its heart, the platform’s power comes from its use of APIs. Think of an API as a secure messenger that lets different software applications talk to each other. For example, the platform can:
Receive alerts from a compliance system when new regulations are updated.
Ingest data from an HRIS about potential conflicts of interest.
Push notifications to a case management tool when a risk indicator requires verification.
This interoperability is what turns isolated data points into actionable intelligence. By standardizing the communication between systems, organizations can finally build a comprehensive, real-time view of their internal risk landscape. You can learn more about how this works by exploring the architecture of a modern ERM platform and its benefits.
By connecting disparate systems, a risk management API integration platform ensures that critical information no longer falls through the cracks. It provides a structured, auditable, and collaborative framework for protecting both the institution and its people.
This structured approach isn't about making judgments. It's about identifying indicators that warrant further, human-led verification according to established company policies. It empowers HR, Risk, and Legal teams to act fast and with confidence.
Understanding Core API Architecture and Design
Before you start plugging into endpoints, it’s worth taking a moment to understand the thinking behind our API’s architecture. A solid, well-designed foundation is what makes any risk management platform stable, scalable, and secure, and ours is built on principles that developers will find predictable and straightforward.
The entire platform is built around RESTful API principles. This isn’t a proprietary or complex system you have to learn from scratch. It means all communication happens over standard HTTP methods like GET, POST, PUT, and DELETE, and data is exchanged in JavaScript Object Notation (JSON), the lightweight format that has become the universal standard for web APIs. This approach guarantees broad interoperability, allowing our platform to connect seamlessly with just about any enterprise system you can think of—from a modern HRIS to a legacy compliance database.
Standardized Data Models for Consistency
A critical part of our architecture is the use of standardized data models. Think of these models as a common language for risk. They ensure that a "compliance event" flagged by a legal tool means the exact same thing as a "risk indicator" coming from an HR system. This consistency is the only way to create a single, unified view of risk across the entire organization.
Without these standards, you'd be stuck building complex, custom mappings for every single data source. That’s a recipe for errors and makes any kind of enterprise-wide analysis practically impossible. A robust risk management API integration platform solves this by enforcing a consistent structure for every piece of data that moves through the system.
This brings a few major benefits to the table:
Interoperability: Your systems can talk to each other without needing custom translators for every single integration.
Data Integrity: Information stays accurate and consistent as it flows between different platforms.
Scalability: New systems can be integrated much faster simply by conforming to the established data schema.
This architectural discipline is more important now than ever. The Integration Platform as a Service (iPaaS) market, which is a key enabler for this kind of API-driven risk management, is on track to hit USD 292.9 billion by 2035. This massive growth is driven by the fact that 83% of businesses now use APIs to achieve 53% faster integration compared to older, clunkier methods. You can find more insights on the expanding iPaaS market over at Precedence Research.
API Versioning for Stable Integrations
Finally, any mature API architecture has to have a clear strategy for managing change. We do this through a straightforward versioning policy. As we roll out new features or update data models, versioning ensures that your existing integrations keep working without any disruption. You'll typically see this handled by including a version number right in the API endpoint URL (e.g., ).
By implementing a clear versioning policy, the platform guarantees backward compatibility. This allows development teams to adopt new features at their own pace without the risk of breaking critical, established workflows that rely on older versions of the API.
This kind of architectural foresight provides the stability you need to build mission-critical business processes. It's a core piece of a resilient security architecture, ensuring the platform remains a reliable and compliant foundation for your entire risk management ecosystem. To go deeper, check out our guide on the principles of a strong security architecture.
Securing Integrations with Authentication and Authorization

Security isn't just a feature; it's the absolute foundation when you're handling sensitive HR and compliance data. For any risk management API integration platform, this means locking down access with bulletproof authentication and authorization. It’s all about controlling who can access what, and under what specific circumstances. These controls aren’t optional—they're what stand between you and a data breach.
The industry standard for securing API access is the OAuth 2.0 framework, and for good reason. It allows applications to get limited, delegated access without ever handling a user's raw credentials. This is a critical distinction, as it means your integrated systems never have to store sensitive passwords directly, massively reducing your security footprint.
Implementing OAuth 2.0 and Managing API Keys
The beauty of the OAuth 2.0 flow is that it’s built for secure, temporary access. Instead of relying on static passwords that can be stolen and reused, it works with access tokens. These tokens have a specific scope and a short lifespan, which dramatically shrinks your attack surface. If a token is compromised, it expires on its own.
The process is straightforward and breaks down into a few key steps:
Client Registration: First, you register your application with the platform. This gets you a unique client ID and client secret.
Authorization Grant: Your application then requests authorization from the user, clearly stating the permissions it needs (like read-only access to risk indicators).
Token Issuance: Once the user grants permission, the platform issues a short-lived access token and a long-lived refresh token.
API Access: The application then includes this access token in the header of every API call it makes. When that token expires, it uses the refresh token to get a new one automatically, without bothering the user again.
One thing you absolutely have to get right is storing API keys and client secrets securely. Never, ever hardcode them into your application's source code. Use environment variables or a proper secrets management service to keep them out of the wrong hands.
Scoping Permissions with Role-Based Access Control
Knowing who is making a request is only half the battle. You also have to control what they can do. This is where Role-Based Access Control (RBAC) comes in, enforcing the non-negotiable principle of least privilege. You don't assign permissions to individual users; you assign them to well-defined roles, and then put users into those roles.
For a risk management API integration platform, you might set up roles like these:
HR Analyst: Can see employee risk indicators but has no ability to change mitigation workflows.
Compliance Officer: Can create and manage compliance events and pull audit logs, but can't dig into specific HR personnel files.
System Administrator: Has full control to configure integrations and manage user roles, but is blocked from viewing the actual content of individual risk cases.
This granular control ensures that users and the systems they connect to only have access to the exact data and actions they need to do their jobs. It’s not just a best practice; it’s a core requirement for complying with data protection laws like GDPR and security standards such as ISO 27001. By strictly scoping permissions from the start, you build a secure and compliant environment by design.
A Practical Guide to Key API Endpoints and Data Models
Successfully integrating with our risk management platform really comes down to a solid grasp of two core components: the API endpoints and the data models they speak. Think of endpoints as the direct phone lines into our system—specific URLs your applications will call to create, retrieve, update, or delete risk-related information.
Each endpoint is purpose-built for a specific job, which keeps interactions logical, secure, and easy to manage. This structured approach is what allows developers to build powerful, maintainable integrations. You wouldn't use the endpoint for pulling compliance reports to submit a new risk signal, for example. The separation is intentional and keeps things clean.
Core Endpoints for Risk and Compliance Workflows
We’ve organized the platform’s functionality across several key endpoints that serve as the building blocks for automating your internal risk and compliance processes. Getting to know their specific purpose is the first step toward building a truly responsive and intelligent system.
Here are the primary endpoints you'll be working with:
/risk-indicators: This is your main channel for managing individual risk signals. Use a request to push a new indicator from a connected system, a request to pull existing ones based on criteria like date or source, and to update a signal's status as it moves through your workflow.
/mitigation-workflows: This endpoint controls what happens after a risk indicator is flagged. You can use it to programmatically assign a case to an HR investigator, kick off a formal review, or escalate an issue based on your company's predefined governance rules.
/compliance-events: Use this resource to log and track events tied directly to your regulatory requirements. It's crucial for creating an auditable trail, whether you're documenting the completion of mandatory training or logging a potential conflict of interest disclosure.
/audit-logs: This is a read-only endpoint that provides a chronological, unchangeable record of all API activity. It's essential for security reviews and proving compliance during internal or external audits by showing exactly who accessed what data and when.
This separation of concerns makes the API predictable and much easier to work with. Each endpoint handles a distinct part of the risk management lifecycle, from the initial signal to the final resolution and report.
To help you get started, here's a quick summary of these essential endpoints.
Endpoint Quick Reference
Endpoint | Description | Supported Methods |
|---|---|---|
Manages individual risk signals from source systems. | , , | |
Triggers and manages response processes for risk events. | , | |
Logs auditable events related to regulatory mandates. | , | |
Provides a read-only history of all API interactions. |
Having these distinct resources allows you to build modular, resilient integrations that map directly to your real-world processes.
Understanding the Underlying Data Models
Behind every endpoint is a well-defined data model that dictates the structure of the information being exchanged. These models, always formatted in JSON, are what keep data consistent and machine-readable across every system you connect. When you're dealing with structured documents, for instance, knowing what a standard Certificate of Insurance Template contains helps clarify the exact fields an API needs to process.
A typical object, for example, might look like this:
{ "indicatorId": "ind-a4b1c8e2", "sourceSystem": "HRIS-Platform", "indicatorType": "ConflictOfInterest", "timestamp": "2023-10-26T10:00:00Z", "severity": "Medium", "employeeId": "E-12345", "details": { "description": "Employee holds external position with a key vendor.", "relatedEntity": "Vendor-XYZ Corp" }, "status": "PendingReview"}
This structured format is absolutely vital. The field gives you clear traceability, while standardized values for and are what enable automated routing and prioritization. By mapping these data models to your internal HR and compliance workflows, you can build incredibly powerful automations.
Key Takeaway: The data model is the contract between your system and our API. Sticking to its structure isn't just a suggestion—it's non-negotiable for a successful integration. It guarantees that the risk intelligence flowing into the platform is accurate, consistent, and actionable.
This consistency allows our platform to pull in data from dozens of different sources and consolidate it into a single, unified view without any guesswork. It’s this structured approach that transforms disconnected data points into a coherent, operational picture of your risk landscape.
Integrating Webhooks for Real-Time Event Notifications
Proactive risk management has to be built on real-time data, not on batch jobs that run overnight. While our API endpoints are perfect for pulling data whenever you need it, webhooks are essential for pushing information to your systems the second a critical event happens. This reactive, event-driven approach is a core part of any modern risk management API integration platform.
Instead of your application constantly polling an endpoint to ask, "Anything new yet?"—a process that burns through resources—webhooks completely flip the script. Our platform proactively sends a notification straight to your designated endpoint as soon as something important occurs, like a new risk indicator being flagged. This means you get critical alerts immediately, letting you kick off response workflows in seconds, not hours.
The Webhook Subscription Process
To start getting these automated notifications, you first need to register a secure endpoint (a URL) where your application is ready to listen for incoming data. You can handle this through a simple API call or right within the platform's user interface.
During the registration process, you’ll need to specify a few key things:
The Endpoint URL: This is the public-facing URL of your service that will receive the webhook payloads. It absolutely must be a secure HTTPS endpoint.
Event Types: You subscribe only to the events that actually matter to your workflows, such as , , or . This keeps your system from getting bogged down with irrelevant noise.
A Secret Key: This is a unique, confidential string we use to sign requests, allowing you to verify that every incoming notification is genuinely from our platform.
Once you're subscribed, our platform will send an HTTP POST request with a JSON payload to your URL whenever one of your chosen events is triggered. This event-driven architecture is incredibly efficient and unlocks automated workflows that would be impossible with traditional API polling.
The flowchart below shows how our key API endpoints and webhooks work together, creating a seamless flow from initial risk detection all the way to automated mitigation and compliance tracking.
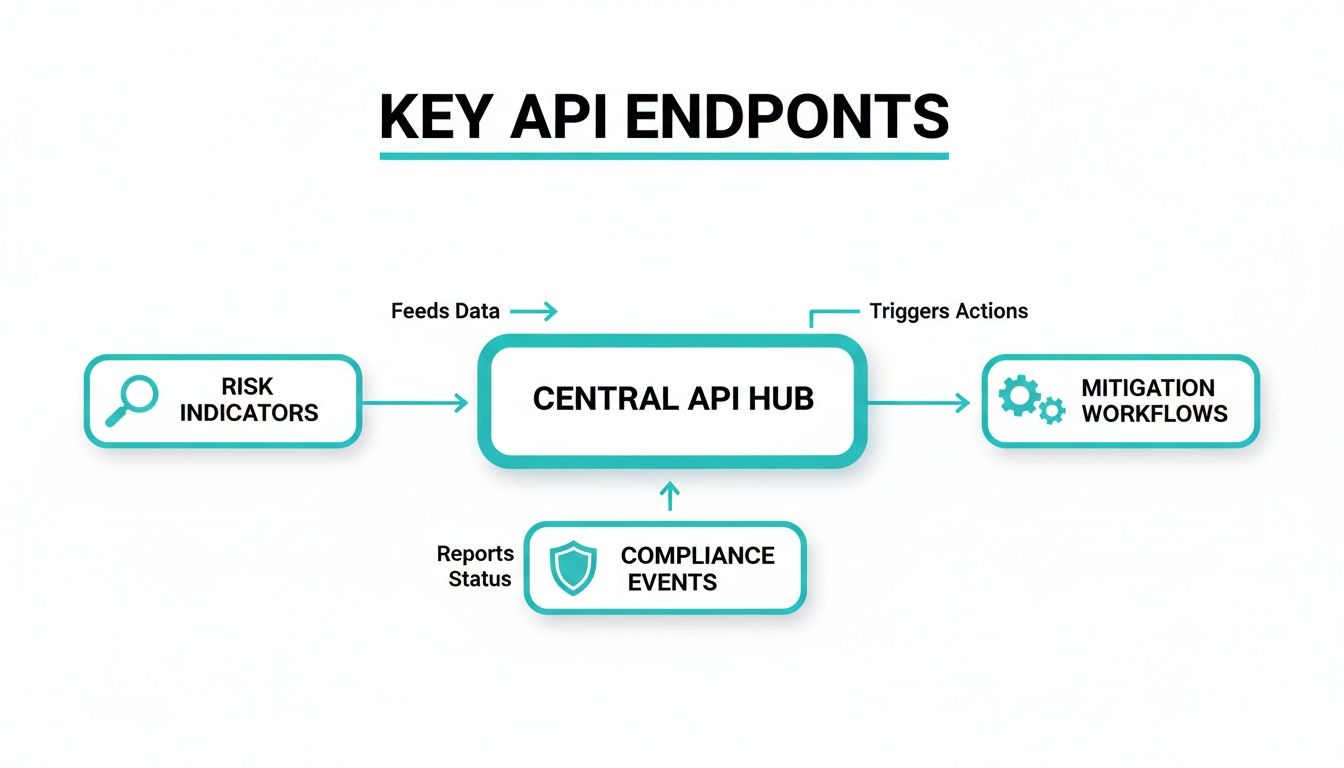
As you can see, an initial risk indicator can trigger a mitigation workflow, which in turn logs a compliance event, all without any manual intervention.
Securing and Handling Webhook Payloads
Security is non-negotiable when you’re dealing with webhooks. Because your endpoint is publicly accessible, you must verify that every single request you receive is legitimate. Each webhook payload sent from our platform will include a special HTTP header, usually , which contains a hash generated using the secret key from your subscription.
Your application’s first job is to perform the same hashing calculation on the payload it just received and compare the result to the signature in the header. If they match, you know the request is authentic. If they don't, discard it immediately.
Best Practice: Always validate the webhook signature before processing any data. Failing to do so opens your system up to forged requests and creates a massive security vulnerability. It's also smart to build in resilience by implementing a retry mechanism with exponential backoff to handle any temporary network failures on your end.
Security and Compliance by Design
When you're dealing with sensitive data from HR, Legal, and Integrity teams, security and compliance can't be an afterthought. They have to be baked into the very foundation of any risk management API integration platform. The architecture itself must enforce ethical lines and stand up to serious regulatory scrutiny. It’s all about building in robust security from the start, making sure every single interaction is secure, traceable, and compliant by default.
This security-first mindset starts with protecting the data. Whether it's moving between your systems or sitting in the platform's database, all information must be locked down with strong encryption like AES-256. This ensures that even if a breach were to happen, the data itself remains unreadable. Just as critical, the platform must provide comprehensive audit logs—an unchangeable, time-stamped record of every API call, data request, and configuration change.
Alignment with Global Regulatory Frameworks
A truly compliant platform doesn't just check boxes; it aligns its core architecture with major international data protection and security frameworks. This is about building trust and ensuring the platform can be rolled out globally with confidence. Key frameworks include:
GDPR (General Data Protection Regulation): The API has to support principles like data minimization, making sure only essential data is ever processed.
CCPA/CPRA (California Consumer Privacy Act/Privacy Rights Act): It must have built-in mechanisms that allow individuals to access, delete, and understand how their data is used.
ISO 27001: The platform's security controls, from who can access what to how incidents are handled, should follow this internationally recognized standard for information security.
This built-in alignment provides a strong, defensible foundation, which is absolutely crucial for organizations operating under heavy regulatory oversight. For a deeper look into this subject, our guide on achieving compliance in business operations offers additional context.
Preventing Abuse with Rate Limiting
To keep the platform stable and shut down abuse, smart rate limiting is essential. These policies automatically cap the number of API requests a single user or app can make in a given timeframe. It’s a simple but incredibly effective way to guard against denial-of-service (DoS) attacks and stop a misconfigured integration from flooding the system.
By designing security and compliance into every layer of the API, the platform becomes a trusted partner for sensitive operations. It provides HR and legal teams with the assurance that their data is handled ethically and in accordance with global standards.
The global open API market is projected to grow from USD 4.53 billion to USD 31.03 billion by 2033. This explosive growth highlights the urgent need for secure data flow across increasingly complex systems, making platforms with embedded compliance indispensable. Discover more insights about the rise of real-time data integration on integrate.io.
Developing with Code Samples and SDKs
Getting an integration off the ground shouldn't mean reinventing the wheel. For any developer connecting to a risk management API integration platform, the real work is in the business logic, not wrestling with raw HTTP requests. This is exactly why well-built code samples and Software Development Kits (SDKs) are so critical—they bridge the gap between reading the documentation and writing functional code.
Instead of hand-crafting every API call, SDKs give your team pre-built libraries in languages they already use, like Python or JavaScript. These toolkits handle the tedious but crucial work of authentication, request formatting, and error handling. This frees up your developers to focus on what actually matters: connecting the platform’s capabilities to your core business processes.
Leveraging Pre-Built Integration Assets
Using an SDK isn't just a matter of convenience; it’s a strategic move that delivers real, measurable advantages right from the start. These libraries are designed to get you from concept to a production-ready integration in a fraction of the time, all while enforcing best practices.
The benefits become obvious almost immediately:
Faster Implementation: You can skip writing all the boilerplate code for authentication and managing API requests.
Reduced Errors: By handling the low-level communication, an SDK drastically cuts down on common mistakes like malformed requests or improper token handling.
Simplified Maintenance: When the API gets an update, you just update the SDK version. You don’t have to go back and rewrite your custom integration code from scratch.
This push for ready-made integration assets reflects a huge market shift away from manual, error-prone processes toward API-driven governance. The API Integration Service Market, valued at USD 5.54 billion in 2026, is on track to hit USD 7.68 billion by 2032. This growth shows just how much businesses are prioritizing speed and reliability. You can dig into the expansion of prebuilt integration assets on ResearchAndMarkets.com to see the full trend.
By offering robust SDKs and clear code samples, a modern risk management API integration platform empowers developers to build secure, reliable, and powerful integrations with greater speed and confidence.
Ultimately, these resources are all about turning the platform’s power into a seamless extension of your own systems. They provide a practical launchpad for automating everything from submitting risk indicators to logging compliance events, letting your team build better integrations, faster.
Frequently Asked Questions
Integrating with our risk management API can prompt a few detailed questions about performance, security, and customization. Below, you’ll find straightforward answers drawn from real-world projects and best practices our team relies on every day.
How Should We Handle API Rate Limits
Rate limits keep the API reliable for everyone. If you exceed your allowance, the server returns a 429 Too Many Requests error.
To work around this without disrupting your workflows:
Cache Smartly: Store data locally when it doesn’t change often, cutting down repeated calls.
Use Bulk Endpoints: Fetch or update multiple records in a single request instead of looping through individual calls.
Apply Exponential Backoff: When you hit a 429, pause and retry with increasing delays rather than hammering the endpoint.
What Are Best Practices For Storing API Keys Securely
Your API keys should never live in plain sight. Hard-coding them in source files exposes you to major security risks if your repository is ever leaked or compromised.
Instead, protect credentials with these methods:
Environment Variables: Inject keys at runtime so they never appear in your codebase.
Secrets Management Services: Rely on tools like AWS Secrets Manager, Azure Key Vault, or HashiCorp Vault for automated rotation, access controls, and audit logging.
Can We Create Custom Risk Indicators Through The API
Yes—our platform was built for flexibility. Beyond the default risk indicators, you can define entirely new types via the API to match your internal taxonomy.
Once you register a custom indicator, it behaves just like the standard ones. You’ll see it in reports, alerts, and workflow automations, preserving data integrity and consistency across your HR and compliance processes.
At Logical Commander Software Ltd., we provide the ethical, AI-driven platform to help you prevent internal risks before they escalate. Our E-Commander platform unifies risk intelligence across HR, Compliance, and Security to protect your organization and its people. Know First, Act Fast!
%20(2)_edited.png)
