The Top 12 Insider Threat Detection Tools for 2025: A Deep Dive
- Marketing Team

- Dec 23, 2025
- 17 min read
Insider threats, whether malicious, accidental, or negligent, represent one of the most complex challenges in modern cybersecurity and risk management. Unlike external attacks, these risks originate from trusted individuals, making traditional security perimeters ineffective. As organizations adopt remote work and navigate complex regulatory landscapes like GDPR and CCPA, the need for sophisticated insider threat detection tools has become critical.
However, the old approach of invasive surveillance and digital tripwires often creates a culture of distrust, harms employee morale, and raises significant privacy concerns. This guide moves beyond generic feature lists to provide a nuanced look at 12 leading solutions. We will explore how they balance security with ethics, evaluate their real-world applications, and help you identify a tool that protects your organization while respecting your people. This curated resource is designed for professionals in Human Resources, Corporate Security, and Operational Risk looking for actionable intelligence.
This listicle provides an in-depth, comparative analysis of the best platforms available. For each tool, you'll find a concise summary, key strengths and weaknesses, ideal use cases, screenshots, and direct links to help you make an informed decision. We place special emphasis on modern, privacy-preserving platforms like Logical Commander, which pioneer a non-judgmental, governance-first approach to proactively managing human risk. Of course, technology is only part of the solution. Beyond relying on software, organizations must also invest in their human firewall. This includes providing their workforce with effective IT security awareness training to build a resilient security culture from the ground up.
1. Logical Commander Software Ltd.
Logical Commander’s E-Commander platform stands out as a premier choice among insider threat detection tools by placing ethical design and human-centric decision-making at its core. Instead of relying on invasive surveillance or automated judgments, it operates on a privacy-first model that converts fragmented organizational data into clear, actionable risk signals. This approach allows security, HR, and compliance teams to identify potential threats proactively while upholding employee dignity and trust. The platform is engineered to deliver structured, non-judgmental insights, categorizing risks to guide human intervention rather than dictating it.
This focus on ethical governance makes E-Commander a strong fit for organizations operating in highly regulated industries or those committed to a culture of integrity. The platform's design philosophy explicitly rejects lie-detection logic and behavioral profiling, ensuring that it functions as a decision-support system, not a digital arbiter of truth. Its unified operational backbone gives stakeholders real-time visibility and auditable evidence, turning disparate data points into a coordinated risk management workflow. To get a deeper understanding of this proactive approach, you can explore their guide on ethical strategies to prevent insider threats.
Key Differentiators and Use Cases
E-Commander excels by unifying siloed functions into a single, modular platform. Modules like Risk-HR, EmoRisk (emotional risk), and SafeSpeak (whistleblower channel) provide a comprehensive toolkit for managing human-capital risks holistically. This integrated system is particularly effective for:
Proactive Threat Identification: Detecting early indicators of misconduct or integrity violations before they escalate into significant incidents.
Compliance and Auditing: Providing a clear, traceable record of risk identification and mitigation actions that align with GDPR, ISO 27001, and other global standards.
Cross-Departmental Collaboration: Enabling HR, Legal, Security, and Risk teams to work from a single source of truth with standardized workflows and dashboards.
Platform Strengths and Limitations
Pros | Cons |
|---|---|
Privacy-First, Ethical Design: Avoids surveillance and AI verdicts, protecting employee dignity while surfacing early risk signals. | No Public Pricing: Organizations must contact sales for a quote, which can slow down the initial evaluation process. |
Unified, Modular Platform: Provides real-time visibility, traceability, and audit-ready evidence across departments (HR, Security, Legal). | Requires Human Governance: The tool is a decision-support system; its value depends on strong internal processes and human oversight. |
Built-for-Compliance: Aligned with GDPR, EPPA, CCPA, and ISO 27001/27701, making it a safe choice for regulated industries. | Dependent on Data Quality: The effectiveness of risk signals is directly tied to the quality and integration of internal data sources. |
Rapid Time-to-Value: A no-credit-card free trial and quick activation allow organizations to see measurable results almost immediately. | |
Global Scalability: Trusted in over 47 countries by enterprises and governments, demonstrating its capability to scale from startups to sovereigns. |
Website: https://www.logicalcommander.com
2. Microsoft Purview Insider Risk Management (IRM)
Microsoft Purview Insider Risk Management (IRM) is an ideal solution for organizations deeply integrated into the Microsoft 365 ecosystem. Instead of adding another third-party tool, IRM leverages native signals from sources like Teams, SharePoint, and Microsoft Defender for Endpoint. This allows it to detect risky user activities directly within the environment where work happens, making it a powerful, consolidated option among insider threat detection tools.
The platform stands out by baking privacy directly into its workflows. Features like user pseudonymization ensure that alerts are evaluated based on the risk event itself, not the individual's identity, reducing bias until a potential threat is confirmed. This aligns with modern, trust-centric security approaches. The integrated case management tools provide a clear audit trail and facilitate collaboration between HR, legal, and security teams. This native integration streamlines the entire investigation process, from detection to resolution, without leaving the M365 environment. For a deeper look into its capabilities, you can explore this comprehensive guide to Insider Risk Management.
Key Differentiators & Considerations
Feature | Analysis |
|---|---|
Use Case Focus | Best for detecting data theft, security policy violations, and risky user behavior within Microsoft 365. |
Strengths | Native signal integration reduces tool sprawl and simplifies deployment for existing M365 customers. Strong, built-in privacy controls. |
Limitations | Some advanced indicators and features require pay-as-you-go billing, which can make cost modeling complex. |
Pricing Model | Included with certain Microsoft 365 E5/A5 licenses. Some capabilities are consumption-based (Data Security and Privacy Units). |
3. Proofpoint Insider Threat Management (formerly ObserveIT)
Proofpoint Insider Threat Management excels at providing deep endpoint visibility, making it a powerful choice for organizations needing granular forensic evidence. Acquired from ObserveIT, this platform focuses on capturing detailed user activity metadata and offers optional screen captures to create a clear, context-rich timeline of events. This focus on endpoint agent-based monitoring makes it one of the more robust insider threat detection tools for investigating specific incidents related to data exfiltration, privilege abuse, or application misuse.
The platform is engineered to support investigations where clear, irrefutable evidence is required for HR or legal proceedings. It integrates seamlessly with the broader Proofpoint ecosystem, including its DLP and email security stacks, providing a more unified view of risk across different channels. Privacy is also a key consideration, with features like data masking to protect sensitive information during investigations. While the depth of data it collects is a major strength, it often requires careful tuning to manage alert volume and focus on the highest-priority risks.
Key Differentiators & Considerations
Feature | Analysis |
|---|---|
Use Case Focus | Ideal for forensic investigations, compliance monitoring, and collecting evidence of malicious or negligent user activity on endpoints. |
Strengths | Rich endpoint visibility with optional session recording for irrefutable proof. Strong integration with the Proofpoint security stack. |
Limitations | The quote-based pricing model lacks transparency. The high volume of data collected can require significant tuning to avoid alert fatigue. |
Pricing Model | Quote-based. A free trial is available to evaluate the platform's capabilities before committing. |
Website: Proofpoint Insider Threat Management
4. Forcepoint Insider Threat
Forcepoint Insider Threat is a mature solution designed for organizations that require deep visibility into user activities, particularly in highly regulated industries like finance and government. It differentiates itself by focusing on analytics that identify risky behaviors "left of loss," meaning before an actual data breach or incident occurs. The platform correlates user actions across endpoints and applications to build a comprehensive risk profile, moving beyond simple policy violations to understand user intent.
One of its most powerful features is the video replay capability, which provides irrefutable, context-rich evidence for investigations. This allows security analysts and HR teams to see exactly what happened, significantly accelerating triage and response. By integrating with the broader Forcepoint data protection ecosystem, it offers a layered defense mechanism. As a veteran in the space, Forcepoint provides one of the most robust investigation-focused insider threat detection tools, built for large enterprises needing granular control and evidence collection.
Key Differentiators & Considerations
Feature | Analysis |
|---|---|
Use Case Focus | Ideal for deep forensic investigations, intellectual property protection, and monitoring high-risk users in regulated environments. |
Strengths | "Left of loss" behavioral analytics provide early warnings. Video replay offers powerful, undeniable evidence for incident response. |
Limitations | Implementation can be complex and requires significant planning for full coverage. Pricing is not transparent and targets large enterprises. |
Pricing Model | Enterprise-focused pricing available through direct sales; not publicly listed. |
Website: Forcepoint Insider Threat
5. DTEX Systems InTERCEPT
DTEX Systems InTERCEPT offers a human-centric approach to insider risk, combining capabilities from next-gen DLP, UEBA, and user activity monitoring into a single, lightweight platform. It prioritizes proactive "left-of-loss" detection by focusing on behavioral indicators that signal intent, rather than just reacting to policy violations. This allows security teams to intervene early, before a minor risk escalates into a major incident, making it one of the more forward-thinking insider threat detection tools available.
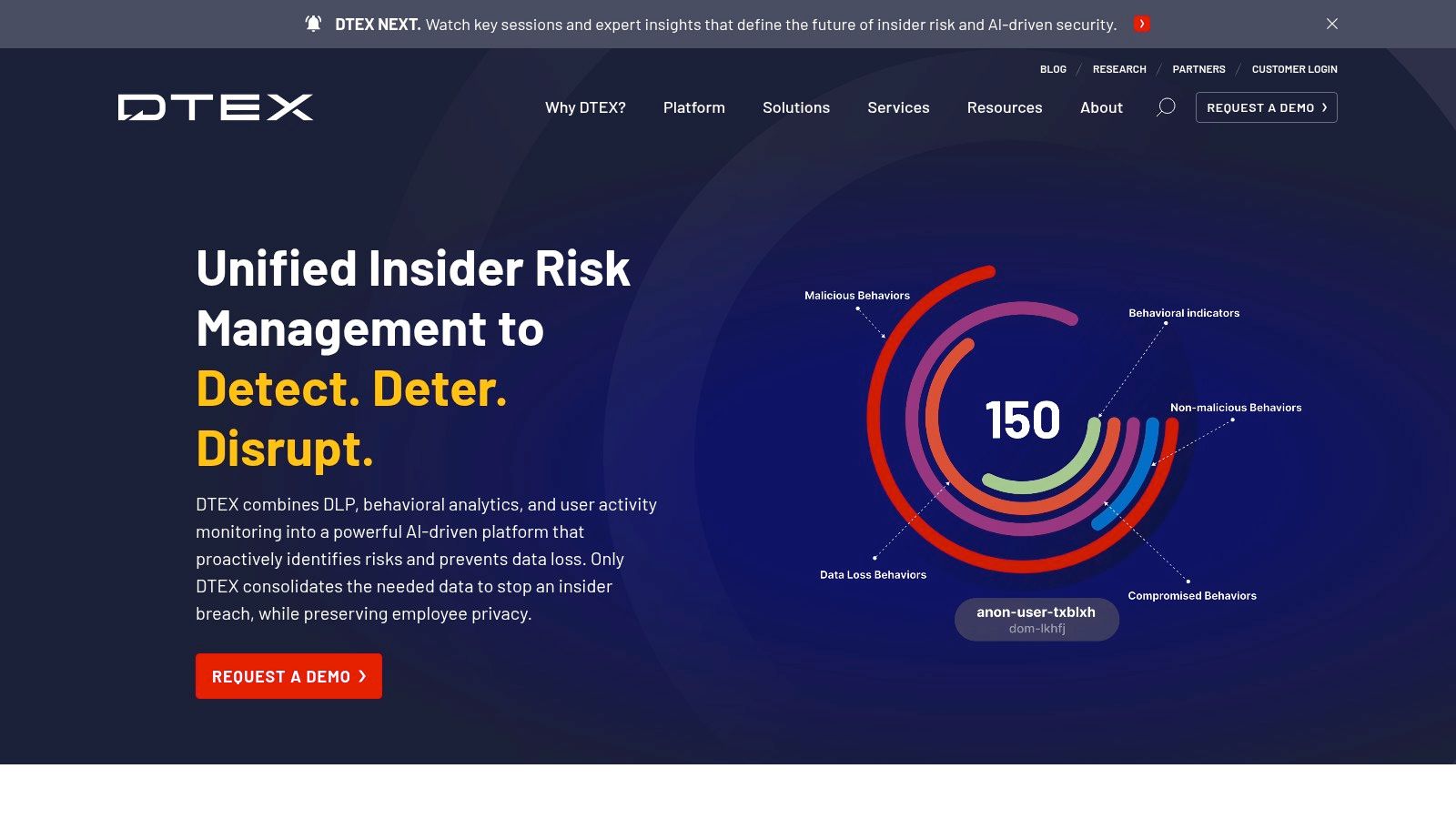
The platform is engineered with a strong emphasis on employee privacy, using pseudonymization to tokenize user data during analysis. This ensures investigations focus on the context of risky activities, not personal identities, until a credible threat is validated. Its endpoint-light agent is designed to minimize performance impact, a common concern with user monitoring solutions. DTEX also offers its i³ expert services for threat intelligence and managed hunting, which can augment an organization's internal security capabilities.
Key Differentiators & Considerations
Feature | Analysis |
|---|---|
Use Case Focus | Proactive detection of data exfiltration, IP theft, and compromised user credentials through behavioral analytics. |
Strengths | Lightweight endpoint agent has minimal system performance impact. Strong privacy-by-design architecture with data pseudonymization. |
Limitations | Requires an agent footprint for full visibility, which may be a hurdle in certain environments. Primarily targeted at mid-to-large enterprises. |
Pricing Model | Available by quote only. Also offered via the AWS Marketplace for streamlined procurement. |
Website: DTEX Systems InTERCEPT
6. Code42 Incydr (Insider Risk & DLP)
Code42 Incydr is a cloud-native SaaS solution laser-focused on detecting and responding to data exfiltration. Unlike broader platforms, Incydr excels at monitoring file movement to untrusted destinations such as personal cloud drives, USB devices, email, and code repositories. Its rapid deployment, available through the AWS Marketplace, makes it an attractive option for organizations looking to quickly gain visibility into how their critical data is being handled and shared.
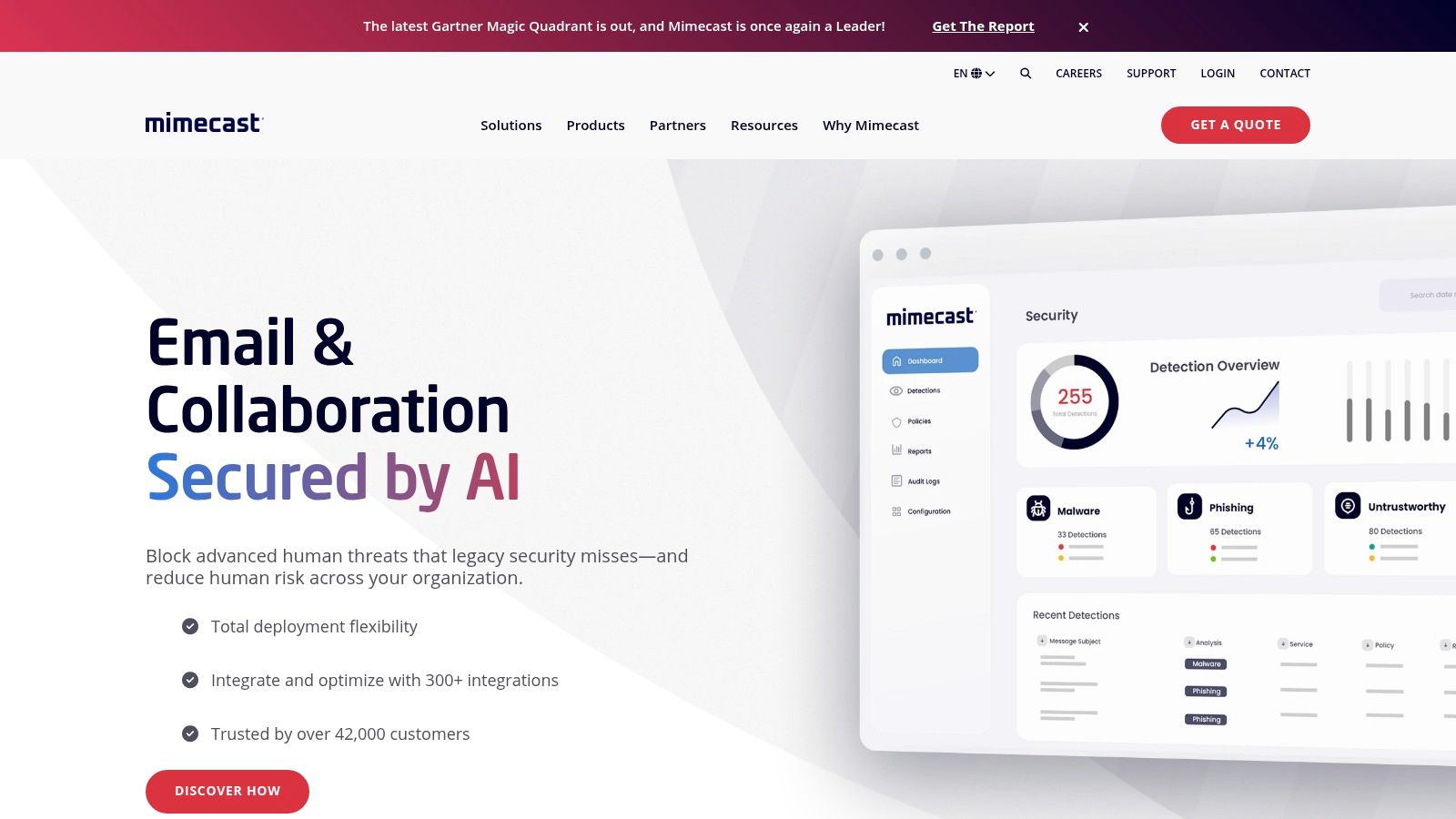
The platform provides investigators with contextual timelines, showing exactly what data left, where it went, and who was responsible. A key differentiator is its optional "Instructor" add-on, which delivers micro-learning videos to users in real-time to correct risky behavior, reinforcing security policies without punitive measures. For those exploring multi-faceted insider risk solutions, it's beneficial to understand how tools like Code42 Incydr integrate with broader comprehensive Data Loss Prevention strategies. Its specialized focus and FedRAMP-authorized government edition make it a noteworthy choice among insider threat detection tools.
Key Differentiators & Considerations
Feature | Analysis |
|---|---|
Use Case Focus | Primarily for detecting and preventing data exfiltration via common vectors like cloud, USB, and email. |
Strengths | Fast cloud-native deployment and strong coverage of key exfiltration pathways. Behavioral coaching add-on offers a proactive, educational approach. |
Limitations | Broader UEBA capabilities beyond file movement may require additional tools. Public pricing is not readily available. |
Pricing Model | Per-user subscription. Available via AWS Marketplace, often using private offers rather than public list pricing. |
Website: Code42 Incydr
7. Securonix UEBA / Unified Defense SIEM
Securonix positions its cloud-native Unified Defense SIEM as a powerhouse for large-scale security analytics, with its User and Entity Behavior Analytics (UEBA) capabilities at the forefront of its insider threat detection. Rather than just collecting logs, Securonix applies advanced, risk-based machine learning to baseline normal user behavior and pinpoint dangerous deviations. This makes it a strong contender for enterprises needing to sift through massive data volumes to find subtle indicators of compromise or malicious insider activity.
The platform’s strength lies in its mature UEBA content and outcome-focused Threat Detection, Investigation, and Response (TDIR) workflows. Its deep integration with data platforms like Snowflake enables powerful, large-scale analytics. For organizations already invested in the AWS ecosystem, Securonix offers flexible procurement through the AWS Marketplace, with multiple contract terms and private offer options available. This flexible approach, combined with its analytical depth, allows organizations to conduct the kind of proactive internal threats assessments needed to stay ahead of sophisticated risks.
Key Differentiators & Considerations
Feature | Analysis |
|---|---|
Use Case Focus | Ideal for enterprise-scale threat hunting, compromised account detection, and identifying sophisticated insider threats through behavioral analytics. |
Strengths | Mature and robust UEBA analytics capable of handling massive data volumes. Flexible procurement and deployment options via AWS Marketplace. |
Limitations | As a full-featured SIEM, it may be overly complex and expensive for smaller organizations or teams with a narrow insider risk focus. |
Pricing Model | Enterprise-focused pricing. Available directly or via AWS Marketplace with 12, 24, and 36-month contract options and UEBA add-ons. |
Website: Securonix Unified Defense SIEM
8. Splunk UEBA (native in Splunk Enterprise Security)
For organizations already leveraging Splunk for security information and event management (SIEM), the native Splunk User and Entity Behavior Analytics (UEBA) capabilities offer a seamless path to detecting insider threats. Integrated directly into Splunk Enterprise Security (ES), this solution analyzes machine data from across the IT environment to baseline normal user and entity behavior. By consolidating SIEM and UEBA, security teams can investigate suspicious activities, such as unusual data access or privilege escalation, within a single, familiar interface.
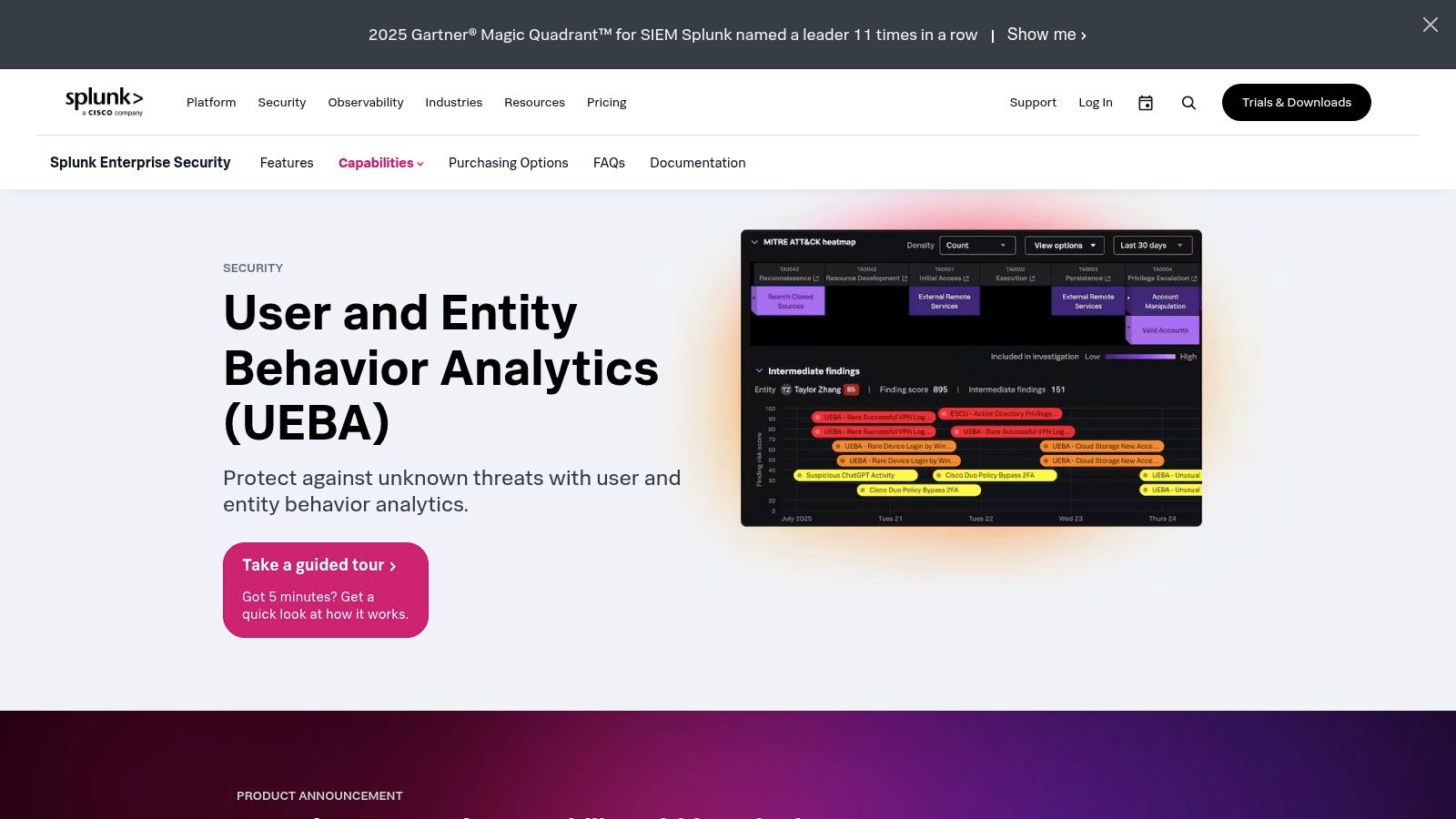
Splunk UEBA excels at identifying anomalies by applying machine learning models to existing data streams, eliminating the need for separate data collection agents. It uses entity risk scoring and peer analytics to contextualize behavior, highlighting deviations that might otherwise go unnoticed. This makes it one of the most powerful insider threat detection tools for teams looking to enrich their existing security operations with advanced behavioral analytics. The extensible framework and vast library of apps on Splunkbase also allow for significant customization to fit unique organizational use cases.
Key Differentiators & Considerations
Feature | Analysis |
|---|---|
Use Case Focus | Ideal for identifying compromised credentials, privileged user abuse, and data exfiltration by leveraging existing SIEM data. |
Strengths | Deep integration with Splunk ES consolidates workflows and reduces tool sprawl. Leverages existing data, simplifying deployment for current customers. |
Limitations | Effective use requires significant Splunk expertise for tuning and content management. Costs are tied to data ingestion, which can be expensive. |
Pricing Model | Requires Splunk Enterprise Security licensing. Pricing is typically based on data ingestion volume or compute resources. |
9. Exabeam UEBA
Exabeam UEBA is a powerful solution for organizations looking to augment their existing SIEM or deploy a standalone platform focused on behavioral analytics. It excels at establishing normal baselines for user and device activity and then using AI to flag risky deviations. This timeline-centric approach helps security analysts quickly understand the sequence of events leading to a potential incident, making it a highly effective tool for detecting credential abuse and other sophisticated insider threats.
What sets Exabeam apart is its emphasis on the investigation experience. The platform automates the creation of "Smart Timelines," which stitch together related user activities into a coherent narrative, significantly reducing the manual effort required to investigate alerts. This focus on workflow and automation streamlines the process from detection to response. Its flexibility allows it to be layered over existing data lakes and SIEMs, providing advanced behavioral analytics without requiring a complete infrastructure overhaul, making it a versatile choice among insider threat detection tools.
Key Differentiators & Considerations
Feature | Analysis |
|---|---|
Use Case Focus | Ideal for detecting credential abuse, lateral movement, and anomalous behavior by augmenting SIEM capabilities. |
Strengths | Strong investigation workflow with automated timelines. Flexible deployment options as a standalone or add-on solution. |
Limitations | Requires significant data integration and initial tuning to establish accurate baselines and minimize false positives. |
Pricing Model | Enterprise-focused, quote-based pricing. Costs will vary depending on data volume and deployment model. |
Website: Exabeam UEBA
10. Netskope Insider Risk (part of Netskope One)
Netskope offers a SASE-native approach to insider risk, making it an excellent choice for organizations prioritizing the prevention of data exfiltration across cloud, web, and SaaS applications. By integrating User and Entity Behavior Analytics (UEBA) with inline and API-based data protection, it moves beyond simple detection to active prevention. The solution assigns a dynamic User Confidence Index (UCI) risk score to each user, enabling adaptive policies that can block risky actions in real time.
The platform's strength lies in its consolidation of network, cloud, and data controls within the Netskope One platform. This unified architecture provides deep visibility into user activities, regardless of their location or device, which is critical for modern, distributed workforces. For teams looking for insider threat detection tools that can also enforce data loss prevention (DLP) policies consistently across all traffic, Netskope provides a compelling, integrated solution that reduces complexity and improves security posture against both malicious and accidental insider threats.
Key Differentiators & Considerations
Feature | Analysis |
|---|---|
Use Case Focus | Primarily for preventing data exfiltration from cloud/SaaS applications and enforcing adaptive security policies. |
Strengths | Strong consolidation of network, cloud, and data controls in one platform. The User Confidence Index (UCI) allows for dynamic, risk-based policy enforcement. |
Limitations | The broad SASE scope can increase deployment breadth and initial rollout complexity. Pricing is not publicly listed and is typically sold via direct channels. |
Pricing Model | Custom enterprise pricing. Requires direct engagement with the sales team for a quote. |
Website: Netskope Insider Risk
11. Teramind (UAM, DLP, Insider Threat)
Teramind is a well-regarded solution that combines user activity monitoring (UAM), data loss prevention (DLP), and insider threat detection capabilities. It is particularly popular with small to mid-market organizations seeking comprehensive visibility and forensic evidence without the complexity of enterprise-grade platforms. The platform excels at capturing detailed user actions, providing security teams with video-level proof for investigations.
What makes Teramind a strong contender among insider threat detection tools is its transparent pricing and deployment flexibility, offering cloud, on-premises, and private cloud options. This straightforward approach allows for faster procurement and proof-of-concept (PoC) timelines, a significant advantage for teams with limited resources. Its powerful rule engine can automatically detect and block policy violations in real-time. However, features like screen and audio recording require stringent governance and clear communication with employees to balance security with privacy.
Key Differentiators & Considerations
Feature | Analysis |
|---|---|
Use Case Focus | Ideal for forensic investigations, productivity monitoring, and enforcing data handling policies in smaller teams. |
Strengths | Transparent and published pricing tiers simplify procurement. Rich forensic evidence capture, including video playback. |
Limitations | Intrusive monitoring capabilities necessitate careful privacy and ethical governance. Advanced features are often locked in higher-cost tiers. |
Pricing Model | Tiered subscription model based on features and deployment type (Cloud or On-Premises). Prices are published publicly. |
Website: Teramind Pricing Plans
12. Syteca (formerly Ekran System)
Syteca offers a robust insider risk management platform that combines deep user activity monitoring (UAM) with privileged access management (PAM) capabilities. Rebranded from Ekran System, it provides granular visibility into user actions through detailed session and screen recordings, creating a comprehensive audit trail for investigations. This makes it a strong choice for organizations needing to monitor high-risk users, critical servers, and third-party vendors with a single, integrated solution.
The platform’s strength lies in its ability to not only detect risky behavior but also prevent it. It includes identity and access controls, such as multi-factor authentication and one-time passwords, alongside its monitoring features. When its behavioral analytics engine detects a deviation from normal activity, it can trigger real-time alerts or even block the suspicious session automatically. This dual-functionality appeals to security teams looking to consolidate their insider threat detection tools with access governance controls, simplifying their tech stack.
Key Differentiators & Considerations
Feature | Analysis |
|---|---|
Use Case Focus | Best for monitoring privileged user activity, auditing third-party access, and investigating security incidents with video evidence. |
Strengths | Combines UAM and PAM-adjacent controls in one suite, offering both monitoring and prevention. Detailed session recordings provide irrefutable audit trails. |
Limitations | The recent rebranding from Ekran System may cause some initial brand confusion during research. Pricing is not transparent and requires a direct quote. |
Pricing Model | Varies by edition and the number of monitored endpoints. A free trial and demo portal are available to test the platform. |
Website: Syteca
Top 12 Insider Threat Detection Tools — Feature Comparison
Solution | Core approach | Privacy & compliance / Quality (★) | Target audience (👥) | USP & Pricing (✨ / 💰) |
|---|---|---|---|---|
Logical Commander Software Ltd. 🏆 | AI-driven, privacy‑first unified platform (E‑Commander + Risk‑HR, EmoRisk, SafeSpeak) for early, non‑judgmental signals | ★★★★☆ · Built-in GDPR/EPPA/CPRA/ISO alignment | 👥 HR, Compliance, Security, Legal, Risk, Internal Audit; SMB→Gov | ✨ Ethical‑by‑design, no surveillance; rapid TTV · 💰 Free trial (no CC); contact sales |
Microsoft Purview IRM | Native M365 signal aggregation, policy templates, integrated case mgmt | ★★★☆☆ · Pseudonymization & privacy controls | 👥 Microsoft 365 customers, enterprises | ✨ Native M365 integration; 💰 Pay‑as‑you‑go/DSPU complexity |
Proofpoint Insider Threat | Endpoint‑centric metadata + optional visual evidence; DLP integration | ★★★☆☆ · Privacy controls & masking | 👥 HR/legal teams needing endpoint forensics | ✨ Rich endpoint evidence; 💰 Quote‑based; free trial |
Forcepoint Insider Threat | Deep user activity monitoring, behavioral analytics & risk scoring | ★★★★☆ · Enterprise/gov compliance focus | 👥 Large enterprises, government | ✨ "Left‑of‑loss" analytics, triage speed; 💰 Enterprise quotes |
DTEX Systems InTERCEPT | Lightweight endpoint telemetry + UEBA, tokenization/pseudonymization | ★★★★☆ · Strong pseudonymization emphasis | 👥 Mid→large enterprises seeking low‑impact endpoint telemetry | ✨ Fast TTV, low perf impact; 💰 Quote; AWS Marketplace |
Code42 Incydr | Cloud‑native DLP/insider risk focused on file exfiltration (cloud, USB, email) | ★★★☆☆ · FedRAMP Gov edition available | 👥 Teams prioritizing data‑exfiltration prevention | ✨ Rapid rollout, behavioral coaching add‑on; 💰 Private offers / marketplace |
Securonix UEBA / SIEM | Cloud SIEM with advanced UEBA and risk‑based detections at scale | ★★★★☆ · Mature analytics & enterprise controls | 👥 Large enterprises needing SIEM‑scale analytics | ✨ Scalable UEBA content; 💰 Significant pricing & onboarding |
Splunk UEBA (ES) | Entity risk scoring, peer analytics, anomaly detection inside Splunk ES | ★★★☆☆ · Quality depends on ES licensing/data | 👥 Splunk customers, SOC and IR teams | ✨ Consolidates SIEM+UEBA; 💰 ES license + ingestion costs |
Exabeam UEBA | Baselines, automated smart timelines and investigation playbooks | ★★★★☆ · Strong investigation UX & automation | 👥 Security ops, enterprises needing investigation automation | ✨ Automated timelines & playbooks; 💰 Quote‑based |
Netskope Insider Risk | SASE‑native inline/API DLP + UEBA with adaptive policy & UCI scoring | ★★★☆☆ · Strong cloud/SaaS controls | 👥 Cloud‑first orgs and SaaS‑heavy enterprises | ✨ Adaptive policy & UCI scoring; 💰 Direct sales (quote) |
Teramind (UAM, DLP) | UAM + DLP with screen/audio capture, OCR, keystroke options | ★★☆☆☆ · Intrusive capture — privacy risk if misconfigured | 👥 SMBs / mid‑market needing full visibility | ✨ Published pricing tiers, quick PoC; 💰 Transparent published tiers |
Syteca (formerly Ekran) | Session/screen recording + privileged access controls & analytics | ★★★☆☆ · UAM+PAM blend; rebrand noted | 👥 Teams needing UAM + privileged session controls | ✨ Combined UAM/PAM capabilities; 💰 Quote‑based; free demo/trial |
Making the Right Choice: From Detection to Dignified Prevention
Navigating the landscape of insider threat detection tools can be a formidable task. This guide has detailed a range of solutions, from the broad-spectrum capabilities of SIEM and UEBA platforms like Securonix and Splunk to the focused user activity monitoring of Teramind and the data-centric approach of Code42 Incydr. Each tool offers a unique lens through which to view and manage internal risks, but selecting the right one requires a thoughtful, strategic approach that extends far beyond a simple feature comparison.
The core takeaway is that the most effective insider risk management programs are not built on surveillance alone. They are built on a foundation of trust, clear policy, and a commitment to employee dignity. The ultimate goal is not just to catch malicious actors but to create a security-conscious culture that prevents incidents from occurring in the first place. This requires a fundamental shift in mindset, moving away from reactive, punitive measures toward proactive, preventative, and supportive interventions.
Key Considerations for Your Final Decision
As you evaluate the options presented, from comprehensive platforms like Microsoft Purview to specialized tools like DTEX InTERCEPT, consider how each aligns with your organization's specific context. The best insider threat detection tool for a highly regulated financial institution will differ from that for a fast-paced tech startup. Your decision-making process should be a collaborative effort involving Security, IT, HR, and Legal departments to ensure all perspectives are represented.
Before committing to a solution, ask these critical questions:
What is our primary risk? Are we more concerned with accidental data leaks, malicious data theft, or workplace safety issues? Align your tool choice with your highest-priority use cases.
How will this impact our culture? Will the chosen tool foster a sense of security or a feeling of being constantly watched? Solutions that focus on anonymized data and policy-based alerts are often better for maintaining trust.
What are our integration needs? How well will the tool integrate with our existing security stack, such as our SIEM, SOAR, and HR information systems? Seamless integration is key to operational efficiency.
Can we manage the operational overhead? Consider the resources required to manage alerts, conduct investigations, and maintain the system. A high volume of false positives can quickly overwhelm a security team.
The Shift Toward Proactive, Ethical Prevention
The most forward-thinking solutions in this space are those that recognize the human element at the center of insider risk. They understand that most incidents are not born from malicious intent but from factors like stress, disengagement, or simple error. This is where a new generation of tools, exemplified by Logical Commander's E-Commander, is redefining the market.
Instead of invasive monitoring and retrospective analysis, these platforms focus on capturing non-judgmental, privacy-preserving signals. They empower managers with the context they need to intervene supportively and proactively, long before a security event materializes. This approach doesn't just detect threats; it helps build a more resilient and supportive organization. It transforms the role of security from an enforcer to a partner in employee well-being and operational excellence.
Choosing your insider threat detection tool is a defining moment for your organization's security and culture. By prioritizing solutions that are effective, ethical, and aligned with your company values, you can build a robust defense that protects your assets while respecting your people. The right strategy will turn a critical vulnerability into a source of organizational strength and trust.
Ready to move beyond traditional surveillance and embrace a proactive, privacy-first approach to insider risk? Discover how Logical Commander Software Ltd. provides the tools to mitigate risks through non-judgmental signals, empowering your team to act preventatively and with dignity. Learn more about our innovative E-Commander platform.
%20(2)_edited.png)
