What Are Insider Threats? A Guide to Human-Factor Risk Management
- Marketing Team

- 3 hours ago
- 14 min read
An insider threat is a security risk originating from within your organization. It involves current or former employees, contractors, or partners who misuse their authorized access, either intentionally or unintentionally. This human-factor risk isn't merely a cyber issue; it's a fundamental business liability that creates staggering financial, reputational, and operational damage. Proactive prevention, not reactive forensics, is the only sustainable way to manage it.
What Are Insider Threats in a Business Context?
To truly grasp what are insider threats, move past the image of a hacker breaching a firewall. Instead, picture a hidden structural weakness slowly compromising your organization's foundation from the inside. This is the nature of human-factor risk.
While external attacks are often loud and obvious, internal risks can silently undermine your company's core, going unnoticed until the damage becomes catastrophic. The threat comes from individuals who already possess legitimate access to your sensitive data, systems, and facilities. The critical challenge for Compliance, Risk, and Security leaders is that these threats are not uniform. They manifest in different ways, each demanding a distinct strategy focused on prevention and mitigation. Recognizing these variations is the first step toward building an internal risk program that is both effective and ethical.
The Three Faces of Insider Threats
Insider threats are not a monolith. Understanding their different forms is crucial, as a strategy designed to stop a malicious actor will fail to prevent a careless mistake. A modern, AI-driven preventive risk management approach must address the full spectrum of human-factor risk.
The table below breaks down the three primary categories. Each one presents a unique business challenge and requires a different preventive posture.
Threat Type | Primary Motivation | Common Business Impact |
|---|---|---|
Malicious Insider | Financial gain, espionage, or personal grievance. | Theft of intellectual property, system sabotage, fraud, reputational damage. |
Negligent Insider | Convenience, carelessness, or ignorance of policy. | Accidental data breaches, compliance violations, operational disruption. |
Compromised Insider | None (unwitting victim). | Data exfiltration by external attackers, ransomware deployment, network compromise. |
An effective internal risk strategy must address all three. Focusing solely on malicious employees leaves your organization exposed to the far more common risks tied to human error and credential theft. The goal is not to police employees but to understand and mitigate the human-factor risks that lead to these incidents in the first place.
An effective internal risk strategy must address all three categories, as focusing only on malicious intent leaves an organization exposed to the far more frequent occurrences of negligence and compromise. The goal is not to police employees but to understand and mitigate the human-factor risks that lead to incidents.
This is why a proactive, non-intrusive approach that focuses on identifying behavioral precursors is far more effective than traditional, reactive security tools. By understanding the different signals of human-factor risk, you can build a more resilient and ethical defense. You can learn more about these signals in our guide on recognizing insider threat indicators.
Understanding the True Cost of Unmanaged Internal Risk
When leaders ask "what are insider threats," they are often trying to quantify the real-world business impact. The answer extends far beyond a single security incident. Unmanaged internal risk unleashes a cascade of financial, legal, and reputational consequences that can overwhelm an organization. The cost and failure of reactive investigations have become too high to ignore.
The financial weight of insider threats has exploded, becoming one of the fastest-growing liabilities for modern companies. The average annual cost of an internal incident has now reached $17.4 million USD—a staggering 109.6% increase from $8.3 million in 2018. This isn't a slow creep; it's a clear signal that the problem is compounding. You can see the full breakdown in the Ponemon Institute Global Cost Study.
This infographic shows where these threats originate, challenging common assumptions.
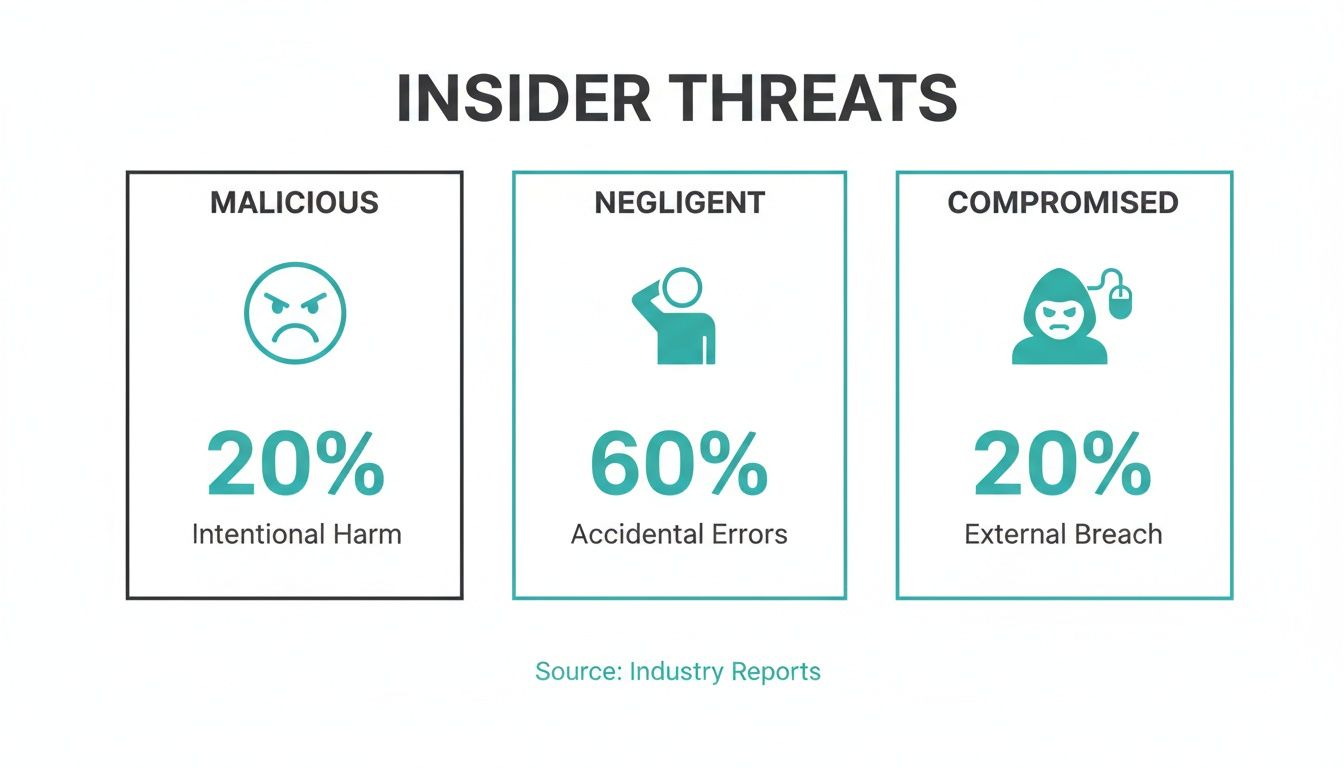
As the data makes clear, the vast majority of incidents stem from negligence, not malicious intent. This highlights why the best defense is a proactive one that addresses human error and closes policy gaps, rather than one that relies on reactive forensics after the fact.
The Hidden Financial Drain of Reactive Approaches
The true bill for an insider incident goes far beyond the direct loss. It's a multi-layered financial drain encompassing direct costs, regulatory fines, and the crushing expense of the reaction itself. Traditional, after-the-fact investigations exemplify this expensive and broken model.
Once an incident is discovered, a costly chain reaction begins:
Forensic Investigations: Hiring external experts to determine what happened can easily cost hundreds of thousands of dollars.
Legal Fees: Managing the legal fallout, from litigation to compliance reporting, adds another massive layer to the bill.
Operational Disruption: Business operations grind to a halt as systems are shut down and key teams are diverted, destroying productivity and revenue.
Reputational Damage: The impact on customer and partner trust is difficult to quantify but has undeniable long-term financial consequences.
The cycle of reacting to damage is a fundamentally broken model. It treats the symptom—the incident—while ignoring the root cause, which is the underlying human-factor risk that was allowed to fester.
This reactive stance keeps organizations in a constant state of financial and operational vulnerability. It forces them to pay a fortune to clean up messes that a smart, preventive strategy could have helped them avoid entirely.
Connecting Internal Risk to Corporate Liability
For Compliance, Risk, and Legal leaders, the line between unmanaged internal risk and corporate liability is razor-sharp. Every incident that could have been reasonably prevented represents a failure of governance and due diligence. This is where the cost transitions from financial loss to legal jeopardy.
Regulators increasingly ask: did the organization have the right controls in place to manage its internal risks? A reactive approach that only activates after a breach is nearly indefensible. It signals a lack of foresight and a failure to protect sensitive assets as required by compliance mandates.
This is precisely why a modern internal risk program must be built on proactive prevention. When you identify and address risk indicators before they escalate, you are not just cutting financial losses—you are building a defensible compliance posture. We delve deeper into this in our detailed guide on the true cost of reactive investigations. Shifting from a reactive cleanup crew to a preventive mindset is the only sustainable way to manage the escalating costs and liabilities tied to insider threats.
Why Traditional Security Fails to Stop Insider Threats
Your firewalls, antivirus software, and other conventional security tools operate on a single core assumption: the enemy is external. They are designed to defend a perimeter. But what happens when the threat doesn't need to break in because they already have a key? This is the fundamental reason traditional tools consistently fail to stop insider threats. They are designed for a different problem—one that starts and ends with humans, not technology.
Legacy internal security methods—like post-incident forensics and surveillance software—share a fatal flaw: they are entirely reactive. These approaches only engage after the damage is done, turning your Security, HR, and Legal teams into an expensive cleanup crew. They do not prevent a breach; they merely document its aftermath. This is a failed standard of internal risk management.
This reactive model is not just ineffective; it's often counterproductive. Surveillance systems are notorious for generating a flood of false positives, burying teams in meaningless alerts. Worse, these intrusive tactics erode employee trust, fostering a culture of suspicion that harms morale and productivity while creating significant legal liabilities.

The Legal and Ethical Pitfalls of Surveillance
In an attempt to gain internal visibility, many organizations resort to tools that monitor employee activity. This approach is a minefield of legal and ethical risks, particularly under regulations like the Employee Polygraph Protection Act (EPPA). Methods such as keystroke logging, email scanning, or any form of secret employee monitoring are not just invasive—they can lead to severe legal challenges and are not EPPA-aligned.
These legacy systems are flawed because they operate on a presumption of wrongdoing, treating every employee as a potential threat. This is a toxic foundation for a business and does little to address the root cause of most insider incidents: human error and negligence.
Erodes Trust: Constant monitoring signals a lack of trust, which is a fast way to damage company culture and loyalty.
Creates Liability: Intrusive surveillance can easily violate labor laws and privacy regulations, exposing the organization to fines and litigation.
Fails Prevention: Surveillance only captures an action as it happens, not the behavioral precursors that signal escalating risk.
The data paints a grim picture. Insider threats are no longer a secondary concern; they now account for 45% of all data breaches globally. Even more telling, the average time to identify an insider threat incident is a staggering 77 days—a massive window for damage to occur. This long detection time highlights the absolute failure of reactive, surveillance-based tools.
Overlooking Hidden Vulnerabilities
Beyond active systems, traditional security often overlooks massive vulnerabilities in plain sight—such as on retired or decommissioned assets. Inadequate data wiping or a poor understanding of proper data sanitization practices can lead to significant data exposure long after a device has left active service. A knowledgeable employee can easily exploit these weaknesses.
The old model of monitoring and reacting is no longer a viable strategy for managing what are insider threats. It exposes organizations to unacceptable levels of financial, reputational, and legal risk, proving that a proactive, ethical approach is the only sustainable path forward.
Ultimately, traditional security fails because it is focused on technology and perimeters, not people. It lacks the nuance to distinguish between a simple mistake and a high-risk pattern of behavior. To truly manage internal risk, you must shift your focus from reactive forensics to proactive prevention. A stronger framework begins with a modern risk-based approach that addresses human-factor risk ethically and effectively.
Adopting the New Standard of Ethical Risk Prevention
The persistent failure of traditional security proves one thing: reacting to damage is a losing strategy. The old model of waiting for a breach and then scrambling to investigate is fundamentally broken, costly, and ineffective.
The new standard for managing internal risk is built on a simple, powerful idea—proactive prevention. This modern approach shifts the focus from after-the-fact forensics to AI-driven, ethical risk identification. It's about understanding the human-factor risks that lead to incidents and addressing them before they cause financial, legal, or reputational harm. This is not about more surveillance; it's the ethical, EPPA-aligned alternative.
The new standard is entirely non-intrusive and aligns with regulations like EPPA by design. It uses AI-driven risk assessments to identify behavioral precursors to risk without any form of monitoring or surveillance. This methodology preserves employee dignity while giving HR, Compliance, and Security leaders the foresight needed to act. Instead of documenting mistakes, the goal is to create a framework that reduces the likelihood of those mistakes happening in the first place.
Moving from Reactive to Proactive Risk Management
Shifting from a reactive posture to a preventive one requires a fundamental change in mindset and technology. It means moving away from a model that asks "What happened?" to one that asks "What could happen?"
This proactive stance is built on identifying and analyzing behavioral risk indicators in a structured, objective way. It focuses on patterns and precursors, not policing individual actions. This allows organizations to spot potential conflicts of interest, policy disregard, or other high-risk situations before they escalate into damaging incidents.
The business benefits are clear:
Preserves Employee Trust: By avoiding surveillance and intrusive monitoring, you maintain a positive and productive workplace culture.
Ensures Compliance: An EPPA-aligned approach protects the organization from the significant legal liabilities associated with improper employee investigation techniques.
Provides Actionable Intelligence: Instead of a flood of false-positive alerts, this method delivers targeted insights that allow for early, constructive intervention.
Why Formal Programs are Becoming Mission-Critical
The strategic need for formal insider risk programs is now undeniable. Research highlights major gaps in organizational preparedness. Currently, 71% of organizations feel they are at least moderately vulnerable to internal risks, yet a staggering 69% still rely on informal, unstructured processes to manage them.
This is changing rapidly. Gartner predicts that half of all medium and large enterprises will adopt formal programs by 2025—a massive jump from just 10% in recent years. This momentum is supported by data showing 77% of organizations have either started or are planning an insider risk program. To learn more about this industry shift, you can explore the full insider threat statistics and research.
The new gold standard for internal risk management is not about catching bad actors; it’s about building a resilient organization. It's an ethical, intelligent system that identifies human-factor risks proactively, allowing for intervention that is corrective, not punitive.
This shift is crucial because detection remains a major challenge. With 60% of HR-security coordination still happening manually, the median time to detect a breach is about 11 days, creating a dangerous window for data theft and fraud. Investing in a structured, AI-driven program closes this gap. You can gain further insights into how this works by reading our article on ethical insider threat detection solutions.
By adopting this new standard, you not only strengthen security but also fortify your governance, reputation protection, and compliance posture for the challenges ahead.
Putting a Modern Insider Threat Program into Action
Moving from theory to practice is the most critical step in defending against internal risks. Implementing a modern insider threat program requires a clear roadmap—one that leaves outdated surveillance behind and embraces an ethical, preventive framework. The goal is to build a cohesive system that protects the organization without creating a culture of distrust.
The process must begin with executive buy-in, demonstrating that a proactive program is not another cost center but a strategic investment in corporate resilience, compliance, and reputation. From there, the focus shifts to integrating the program into the fabric of your existing HR, Compliance, and Security workflows. A modern program cannot succeed in a silo.

Breaking Down Silos with a Unified Platform
One of the biggest roadblocks to managing internal risk is the departmental silo. HR may observe a performance issue, Security might flag unusual access patterns, and Legal could be aware of a conflict of interest—but these dots are rarely connected. This fragmentation creates dangerous blind spots that an insider can exploit, whether intentionally or not.
The new standard tears down these walls with a unified risk platform. A centralized system like Logical Commander serves as the single source of truth for all human-factor risk, ensuring HR, Compliance, and Security operate from the same playbook. This coordinated layer transforms disconnected information into a clear, complete picture of risk.
Building a modern insider threat program means replacing fragmented, manual processes with a single, intelligent system. This integration provides real-time visibility into human-factor risks, allowing teams to collaborate and act decisively before a minor issue becomes a crisis.
This unified view is essential for early detection and prevention. It enables your teams to spot converging risk signals that would be invisible in isolation, creating opportunities for proactive intervention instead of reactive cleanup.
Delivering Actionable Insights, Ethically
The core of a modern program is its ability to deliver actionable, preventive insights without violating employee privacy or legal boundaries. This is where a solution like Logical Commander’s E-Commander / Risk-HR module becomes indispensable, as it was purpose-built to operate within the strict confines of EPPA and other labor regulations.
The platform delivers insights by:
Conducting Non-Intrusive Assessments: It uses structured, AI-driven assessments to identify behavioral precursors tied to risk, completely avoiding any form of surveillance.
Focusing on Prevention: The system is designed to flag potential issues like conflicts of interest or a disregard for policy, enabling corrective action, not punitive measures.
Protecting Employee Dignity: By rejecting secret monitoring or any analysis of mental state, the process remains transparent, fair, and respectful.
This ethical foundation protects your organization from both internal threats and the serious legal liabilities associated with invasive investigation methods. It proves that strong security and a healthy workplace culture are not mutually exclusive.
Empowering Partners to Deliver the New Standard
This shift toward ethical, proactive risk management represents a major opportunity for consultants, B2B SaaS providers, and security advisors. Our PartnerLC program is specifically designed to help these allies deliver this new standard in risk prevention to their clients.
By joining our partner ecosystem, you can:
Expand Your Service Offerings: Add a powerful, EPPA-aligned risk management solution to your portfolio.
Provide Differentiated Value: Offer a non-intrusive alternative to outdated and legally risky surveillance tools.
Drive Client Success: Help your clients build more resilient, compliant, and ethical organizations.
Implementing a modern insider threat program is a strategic imperative. By unifying workflows, embracing ethical technology, and building strong partnerships, organizations can finally move from constantly reacting to damage to proactively preventing it.
It's Time to Get Ahead of Insider Threats
If you take one key takeaway from this guide, let it be this: reactivity is no longer a viable option. The old way of managing internal risk—waiting for a breach and then scrambling to clean up the aftermath—is a recipe for financial and reputational disaster.
Real security requires a complete mindset shift from reaction to prevention. It starts with understanding what are insider threats, but true success comes from stopping them—ethically and efficiently—before they cause lasting damage. We've seen how outdated surveillance tools fail and why a proactive, AI-driven, and non-invasive approach is the only sustainable path forward.
Now, it’s time to put that knowledge into action.
A truly modern defense doesn't stop at your firewall. Consider the hardware you retire—old laptops, servers, and storage devices are often overlooked weak points teeming with sensitive data. That’s why a process as straightforward as secure hard drive shredding is a non-negotiable part of a comprehensive internal risk program. It’s this holistic mindset, covering both human behavior and physical assets, that builds genuine resilience.
Transform How You Manage Internal Risk
This is the exact shift Logical Commander was built to facilitate. Our platform gives your HR, Compliance, and Security teams the tools they need to manage human-factor risk without resorting to invasive surveillance or legally risky methods. It’s about building a stronger, more ethical organization from the inside out.
By adopting an EPPA-aligned, non-intrusive strategy, you can finally:
Prevent incidents before they escalate into costly breaches or investigations.
Strengthen your compliance posture by demonstrating proactive governance.
Protect your reputation and foster a culture of integrity and trust.
Unify risk management across HR, Legal, and Security for a complete view of risk.
The era of after-the-fact cleanups is over. Use the options below to see how our platform can transform your approach to internal risk, protect your most valuable assets, and fortify your organization against the complex challenge of insider threats.
Your Questions on Insider Threats, Answered
As leaders delve into the complexities of internal risk, important questions arise. It’s a nuanced topic that demands clear, practical answers grounded in a modern, ethical approach to risk management. Here are some of the most common questions we address.
How Can We Detect Insider Threats Without Invasive Employee Monitoring?
This is the central question for modern risk management. Ethical insider threat detection focuses on high-risk behaviors and objective risk signals, not intrusive surveillance.
An EPPA compliant platform like Logical Commander does not analyze the content of emails or messages. It doesn’t track keystrokes or monitor screens. Instead, its AI human risk mitigation technology uses structured, non-intrusive risk assessments to identify behavioral patterns that often precede misconduct or conflicts of interest.
This approach flags the precursors to a problem, giving HR and Compliance the opportunity to intervene and prevent an incident. It’s a method that protects the company while fully respecting employee privacy.
Is an Insider Threat Program Only for Large, Regulated Companies?
Absolutely not. While it's non-negotiable for regulated industries, any organization with valuable intellectual property or sensitive data needs a formal program. Mid-sized companies are prime targets for data theft and can be crippled by the financial and reputational fallout from a single incident.
The principles of proactive, ethical risk management scale to any business size. A structured program is an investment in building a culture of integrity and protecting key assets, which benefits organizations in every industry.
What Is the Difference Between an Insider Threat and Human Error?
The difference lies in context and intent. A simple human error is typically a one-off, unintentional mistake without an underlying pattern. An insider threat—even a negligent one—almost always involves a repeated disregard for policy or a convergence of circumstances that create a significant level of risk.
For instance, accidentally sending one email to the wrong person is a mistake. However, repeatedly violating data handling policies while accessing sensitive files outside one’s job description indicates a negligent insider risk. Advanced Risk Assessments Software is designed to distinguish between a simple slip-up and a high-risk behavioral pattern that requires attention.
How Does This Approach Comply with EPPA and Labor Laws?
Full compliance is the cornerstone of a modern program. A platform like Logical Commander is built from the ground up to be EPPA-aligned, meaning it strictly avoids anything that could be construed as lie detection, psychological evaluation, or coercive analysis.
There is no surveillance and no secret monitoring—practices that are both ethically problematic and legally hazardous.
Instead, the platform provides a transparent and objective framework for assessing risk. It’s an ethical decision-support tool that gives HR and legal teams the intelligence they need to act, while ensuring every process is fair, respectful, and fully compliant.
This commitment to ethical standards protects the organization from two threats simultaneously: the internal risks themselves, and the massive legal liabilities that come from using outdated, invasive methods.
Ready to build a stronger, more resilient organization from the inside out? Logical Commander provides the AI-driven, EPPA-aligned platform you need to prevent internal risks before they cause damage.
Start a Free Trial: Get platform access and explore our features.
Request a Demo: See our non-intrusive risk assessment technology in action.
Become an Ally: Join our PartnerLC ecosystem to deliver the new standard in risk prevention.
Contact Us: Discuss an enterprise deployment with our team of experts.
%20(2)_edited.png)
